Microprocessor data flow address matching self-trapping device used for software debugging
A technology of address matching and microprocessors, applied in software testing/debugging, electrical digital data processing, instruments, etc., can solve problems such as difficult to determine instruction errors and difficulties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
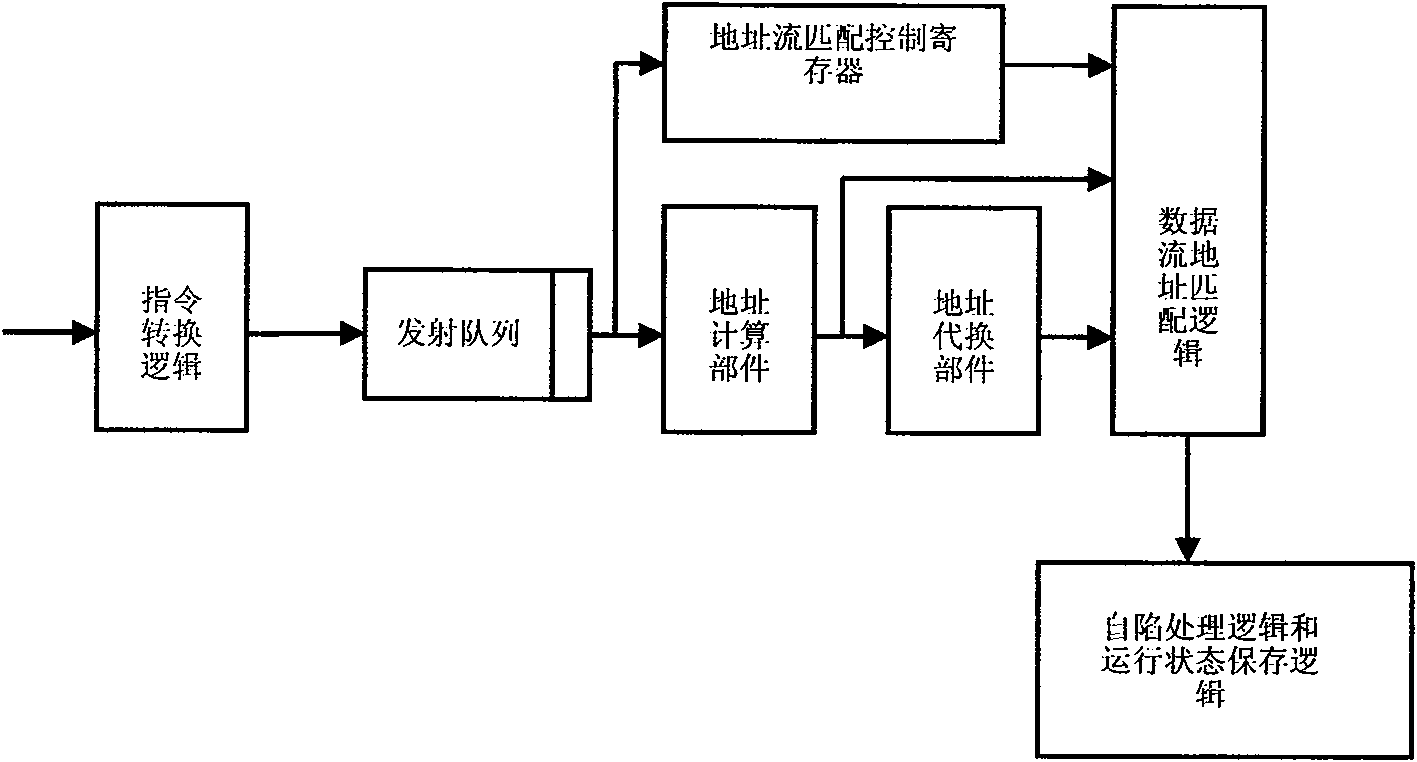
[0016] Assuming that the data of 16 consecutive bytes starting from the physical address 0x16340 is found to be different from the expected value after the program finishes running, you can determine which memory access instruction wrote the data into the main memory in the following way.
[0017] 1. Software configuration data flow address matching control register DA_MATCH, set the MATCH bit to 1, PA bit to 1, EN[1:0] to "10", ADDR[n:0] to 0x16340; configure the data flow mask register DA_MASK, set MASK[n:0] to 0xfff...ffff0.
[0018] 2. When running an error program, the data flow address matching logic will check all the memory access instructions during the running of the program. When the physical address of the "write instruction" on the correct path falls within the range from 0x16340 to 0x1634f, a self-trap will occur. And keep the running state of the microprocessor when the write instruction is executed.
[0019] 3. The software reads the saved processor running st...
Embodiment 2
[0021] Assume an array (contiguous 8192 bytes starting from virtual address 0x302000, ie 1 8KB page). The program only accesses a part of the data in the array (1024 bytes, namely 0x303000~0x3033ff), but it is found that other parts of the array have been accidentally rewritten during program execution. Then you can determine which memory accesses occur in other parts of the array as follows.
[0022] 1. Software configuration data flow address matching controller DA_MATCH, set the MATCH bit to 0, PA bit to 0, EN[1:0] to "11", ADDR[n:0] to 0x303000; configure the data flow mask register DA_MASK, set MASK[n:0] to 0x3ffc00.
[0023] 2. When the error program is running, the data flow address matching logic will check all the access instructions in the running process of the program. When the virtual address [21:10] of the access instruction on the correct path is not 0xc0c, a self-trap will be generated and the address will be kept. The operating state of the microprocessor at...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com