A method for accessing memory with multiple permissions
A storage and permission technology, applied in the field of data management, can solve the problems of incorrect system status, restricted data modification, misoperation of data modification, etc., and achieves the effect of flexible and simple access form, fast read and write operations, and improved security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] The specific process of embodiment one is as follows Figure 5 Shown:
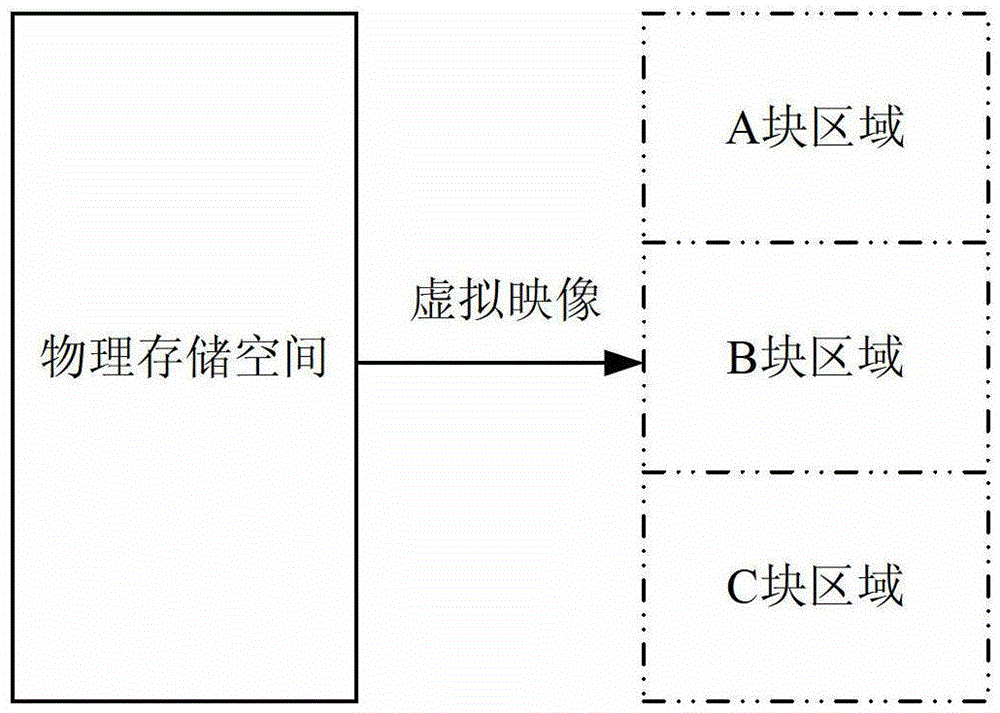
[0054] Step 1. After the product is powered on, the program starts, and the physical storage area is virtualized into three blocks, which are called block A, block B, and block C respectively. Among them, blocks A and B store information about product characteristics, and block C stores product configuration parameter information.
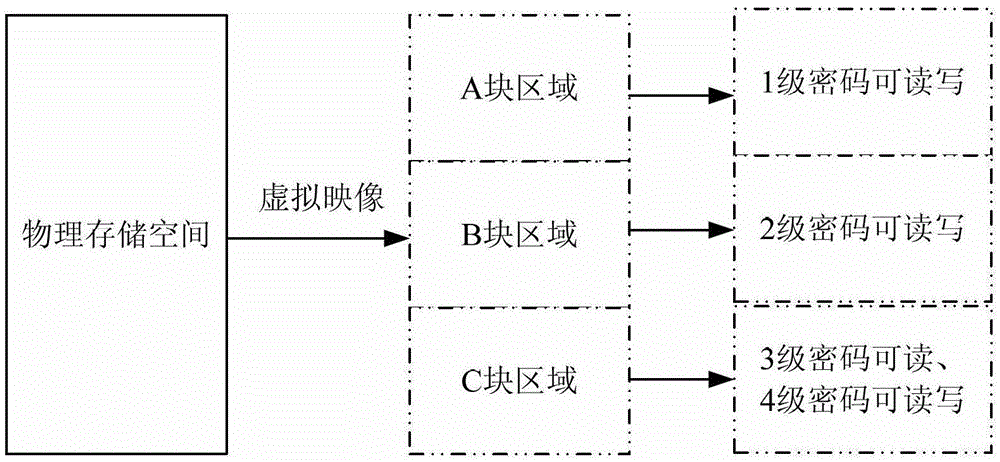
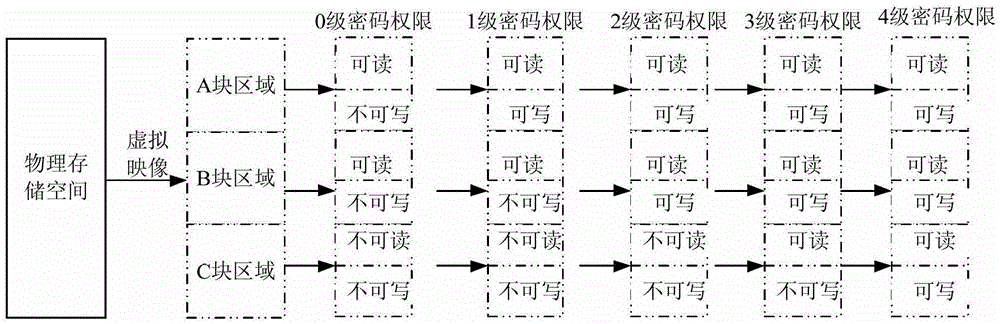
[0055] In the initial state, the default password authority is zero-level password authority, and the information in the storage areas of block A and block B in the memory is read into the buffers BufferA and BufferB of the product respectively. If the user needs to read the storage contents of block A and block B, the contents in the buffer pools BufferA and BufferB can be read to a relevant interface (for example, a display interface).
[0056] The buffer pool BufferC stores default information when the program starts, which can be regarded as "invalid information" a...
Embodiment 2
[0069] The concrete process of embodiment two is as follows Figure 6 Shown:
[0070] Step 1. After the product is powered on, the program starts, and the physical storage area is virtualized into three blocks, which are called block A, block B, and block C respectively. Among them, blocks A and B store information about product characteristics, and block C stores product configuration parameter information.
[0071] In the initial state, the default password authority is zero-level password authority, and the information in the storage areas of block A and block B in the memory is read into the buffers BufferA and BufferB of the product respectively. If the user needs to read the storage contents of block A and block B, the contents in the buffer pools BufferA and BufferB can be read to a relevant interface (for example, a display interface).
[0072] The buffer pool BufferC stores default information when the program starts, which can be regarded as "invalid information" a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com