File encryption method
A file encryption and file technology, applied in the field of encryption, can solve the problems of reducing the security and reliability of encrypted packaged files, and achieve the effect of increasing difficulty and improving security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
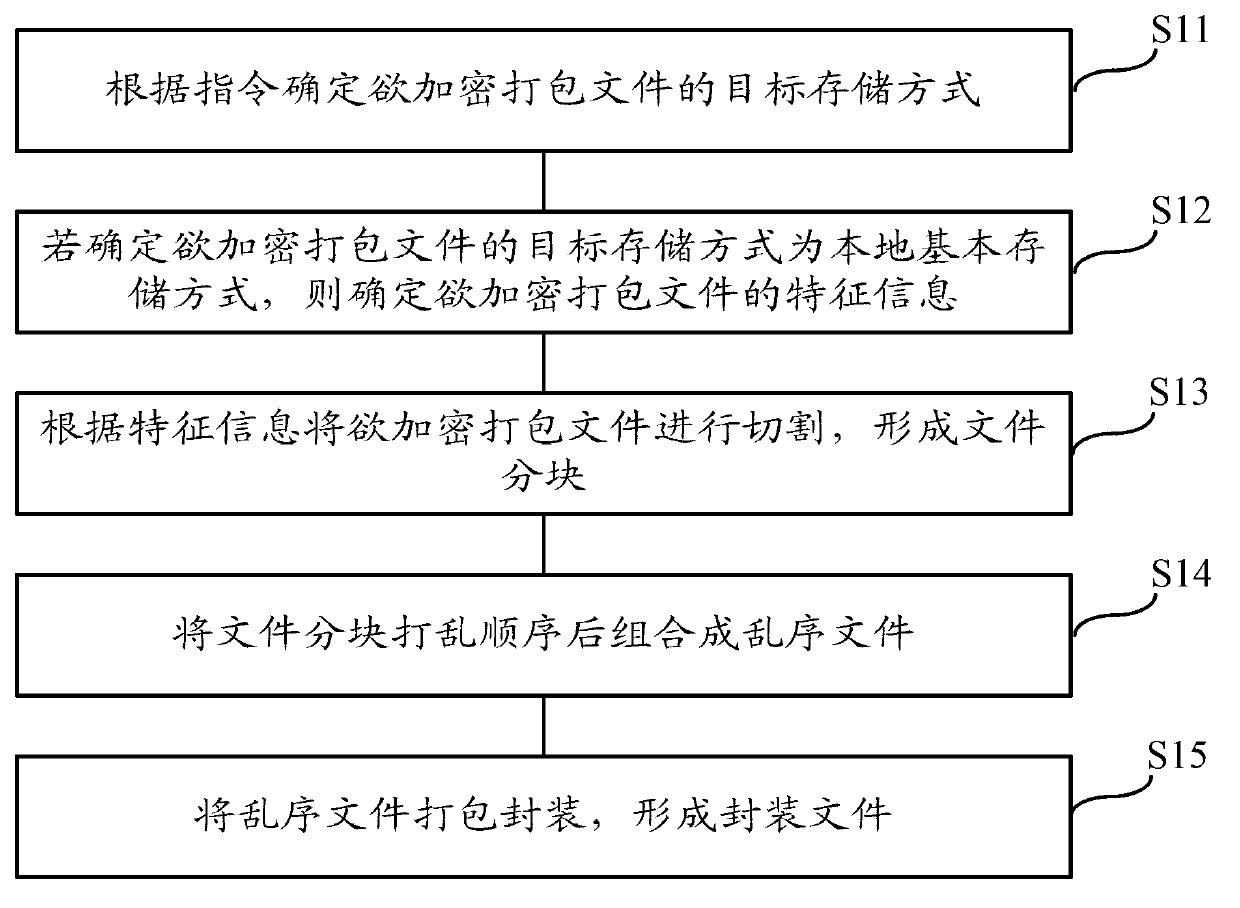
[0019] Embodiment 1 of the present invention provides a file encryption method, such as figure 1 As shown, the main processing steps include:
[0020] Step S11: Determine the target storage method of the encrypted package file according to the instruction;
[0021] Step S12: If it is determined that the target storage mode of the file to be encrypted is the local basic storage mode, then determine the feature information of the file to be encrypted;
[0022] Step S13: cutting the file to be encrypted and packaged according to the feature information to form file blocks;
[0023] Step S14: Shuffle the order of the blocks of the files and combine them into a random file;
[0024] Step S15: Pack and package the out-of-sequence files to form a package file.
[0025] If an illegal user wants to bypass the feature information to extract the files in the packaged file, even if the feature information of the packaged file is bypassed, they can only extract out-of-order files formed...
Embodiment 2
[0061] Embodiment 2 provides a file encryption method, the main processing steps include:
[0062] Step S21: Determine the target storage method of the file to be encrypted and packaged according to the instruction;
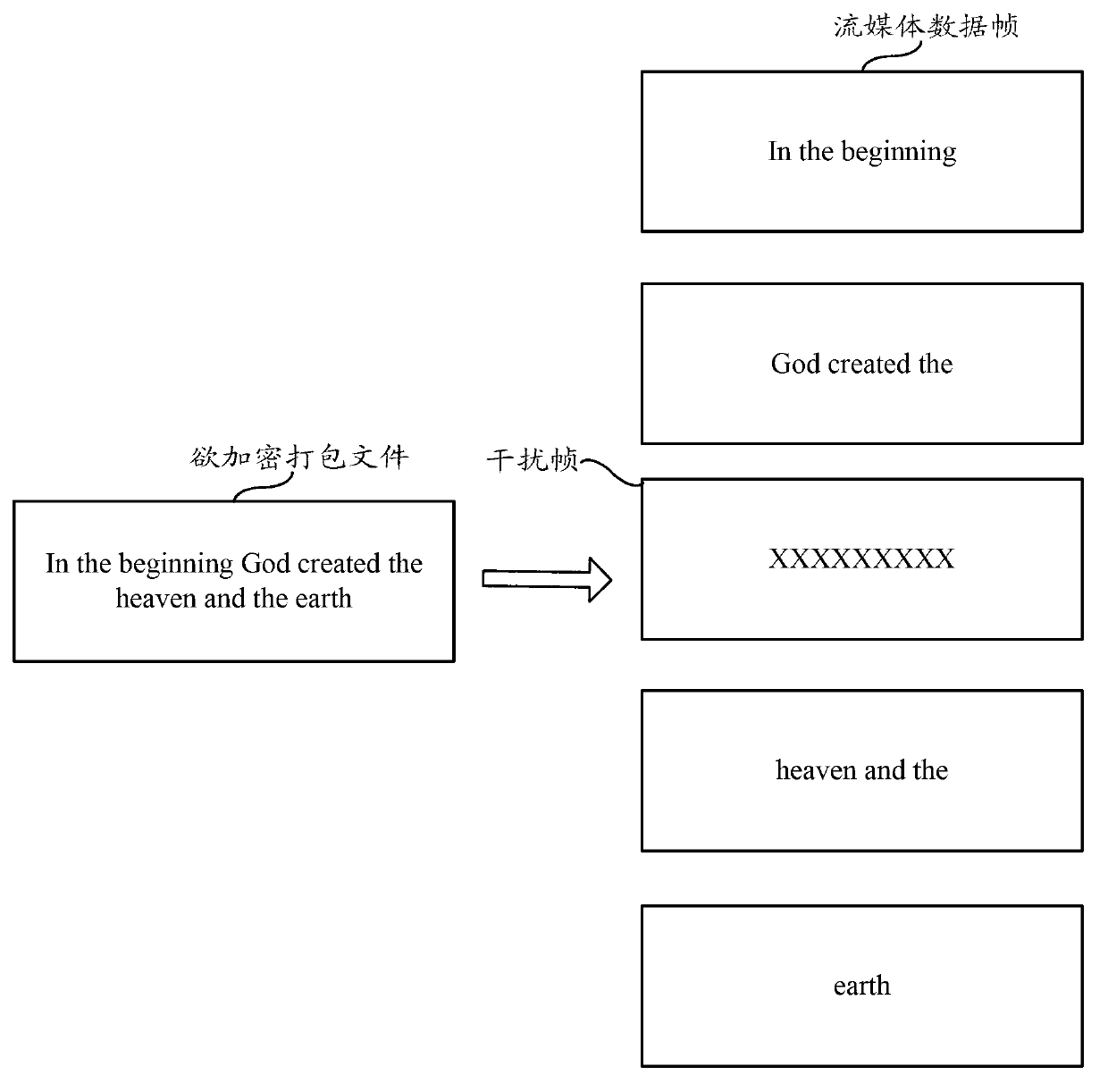
[0063] Step S22: If it is determined that the target storage mode of the file to be encrypted and packaged is a local read-only storage mode, then convert the packaged file to be encrypted into a streaming media data frame;
[0064] Step S23: Determine the characteristic information of the streaming media data frame;
[0065] Step S24: According to the feature information, the stream media data frames are scrambled and combined into a scrambled file;
[0066] Step S25: Pack and package the out-of-sequence files to form a package file.
[0067] Preferably, when the packaged file to be encrypted is a document file, such as a word file, a text document or an electronic form, the information in the document file is not only easy to be identified and read, but also ...
Embodiment 3
[0097] Step S31: Determine the target storage method of the encrypted packaged file according to the instruction;
[0098] Step S32: When it is determined that the target storage method of the file to be encrypted and packaged is a cloud storage method, after storing the packaged file to be encrypted in the cloud server, the cloud server sends cloud link information;
[0099] Step S33: Determine the feature information of the cloud link information;
[0100] Step S34: Segment the cloud link information according to the feature information to form link information segments;
[0101] Step S35: Shuffle the sequence of the link information segments and combine them into a random file;
[0102] Step S36: Pack and package the out-of-sequence files to form a package file.
[0103] The feature information set in this embodiment may include one or more of time stamp information, predetermined opening location information, verification password information, predetermined opening user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com