Video steganography method based on motion vector
A technology of motion vector and video steganography, which is applied in the field of video coding and information hiding, can solve the problem of not having a more effective definition of distortion function, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
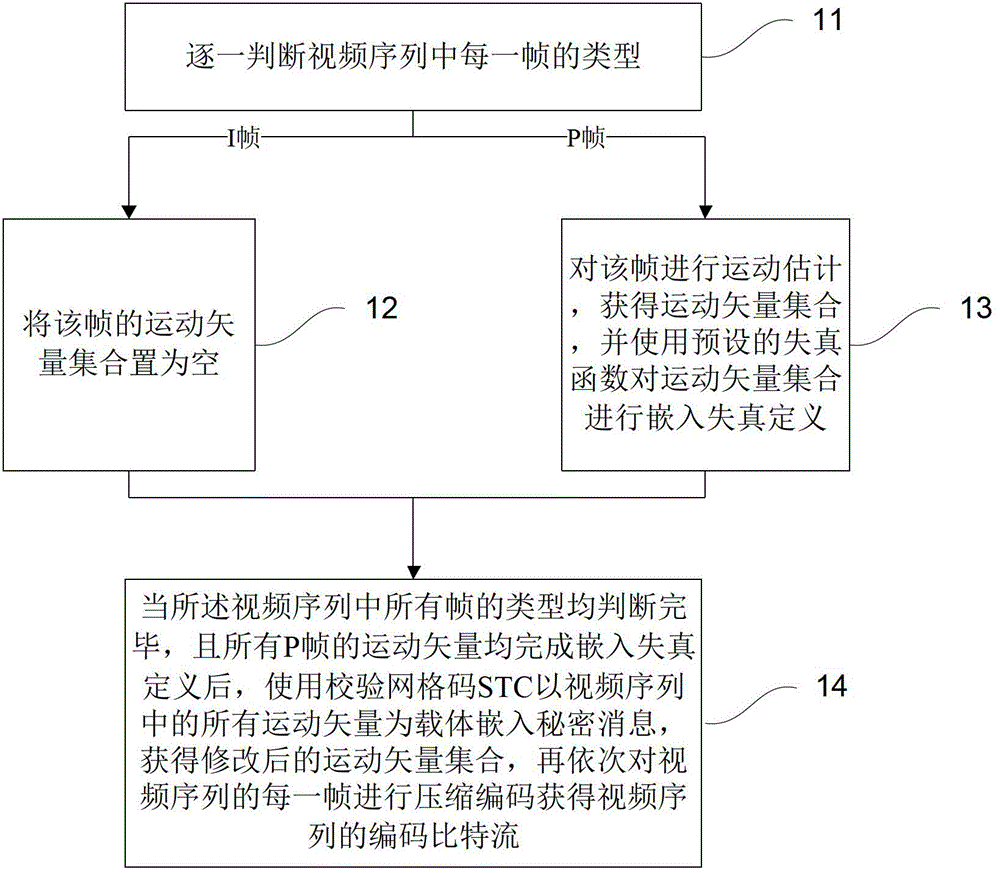
[0022] figure 1 It is a flow chart of a motion vector-based video steganography method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method mainly includes the following steps:
[0023] Step 11, judging the type of each frame in the video sequence one by one. If the tth frame is a key frame I frame that adopts intra-frame predictive encoding, then proceed to step 12; if the tth frame is a predictive frame P frame that adopts inter-frame predictive encoding, then proceed to step 13.
[0024] In the embodiment of the present invention, before judging the type of the video frame, it is necessary to decode the coded bit stream to obtain the corresponding video sequence, and the arrangement of the frame images in the video sequence is also arranged according to its original time sequence.
[0025] The embodiment of the present invention mainly distinguishes video frames that use two compression coding methods: a key frame I frame that adopts i...
Embodiment 2
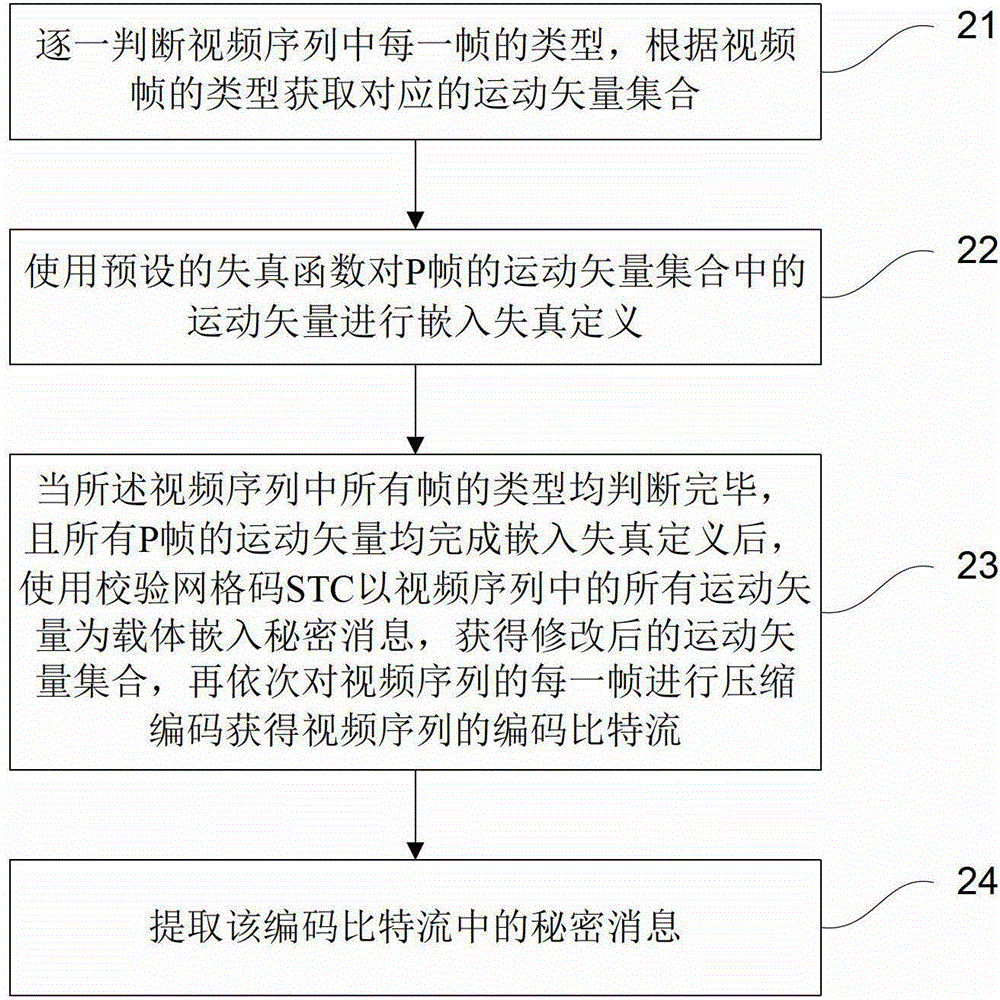
[0039] In order to facilitate understanding of the present invention, below in conjunction with Figure 2-Figure 3 The present invention is further introduced, such as figure 2 As shown, the method mainly includes the following steps:
[0040] Step 21, judge the type of each frame in the video sequence one by one, and obtain the corresponding motion vector set according to the type of the video frame.
[0041] The embodiment of the present invention mainly distinguishes video frames that use two compression coding methods: a key frame I frame that adopts intra-frame predictive coding and a predictive frame P frame that adopts inter-frame predictive coding.
[0042] If the tth frame is an I frame, motion estimation is not performed, and the motion vector set MV of the frame is directly t Leave blank.
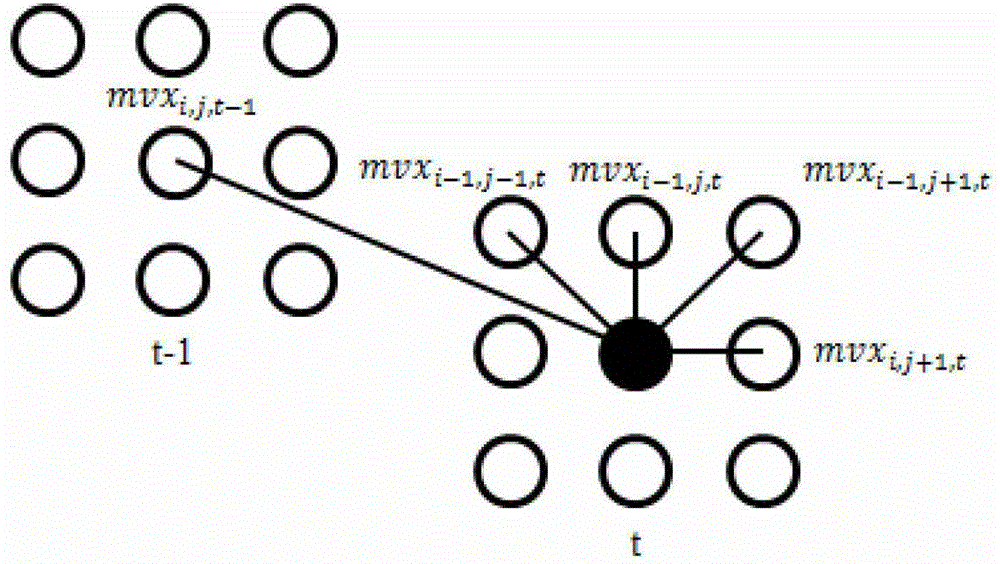
[0043] If the tth frame is a P frame, perform motion estimation. Specifically, motion estimation is performed on each coding block in the frame to obtain the motion vector m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com