Wireless sensor network security data discovery and dissemination method based on Hash tree
A wireless sensor and network security technology, applied in network topology, wireless communication, public key for secure communication, etc., can solve the problems of ignoring data discovery and dissemination security, and achieve the effect of ensuring efficiency and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
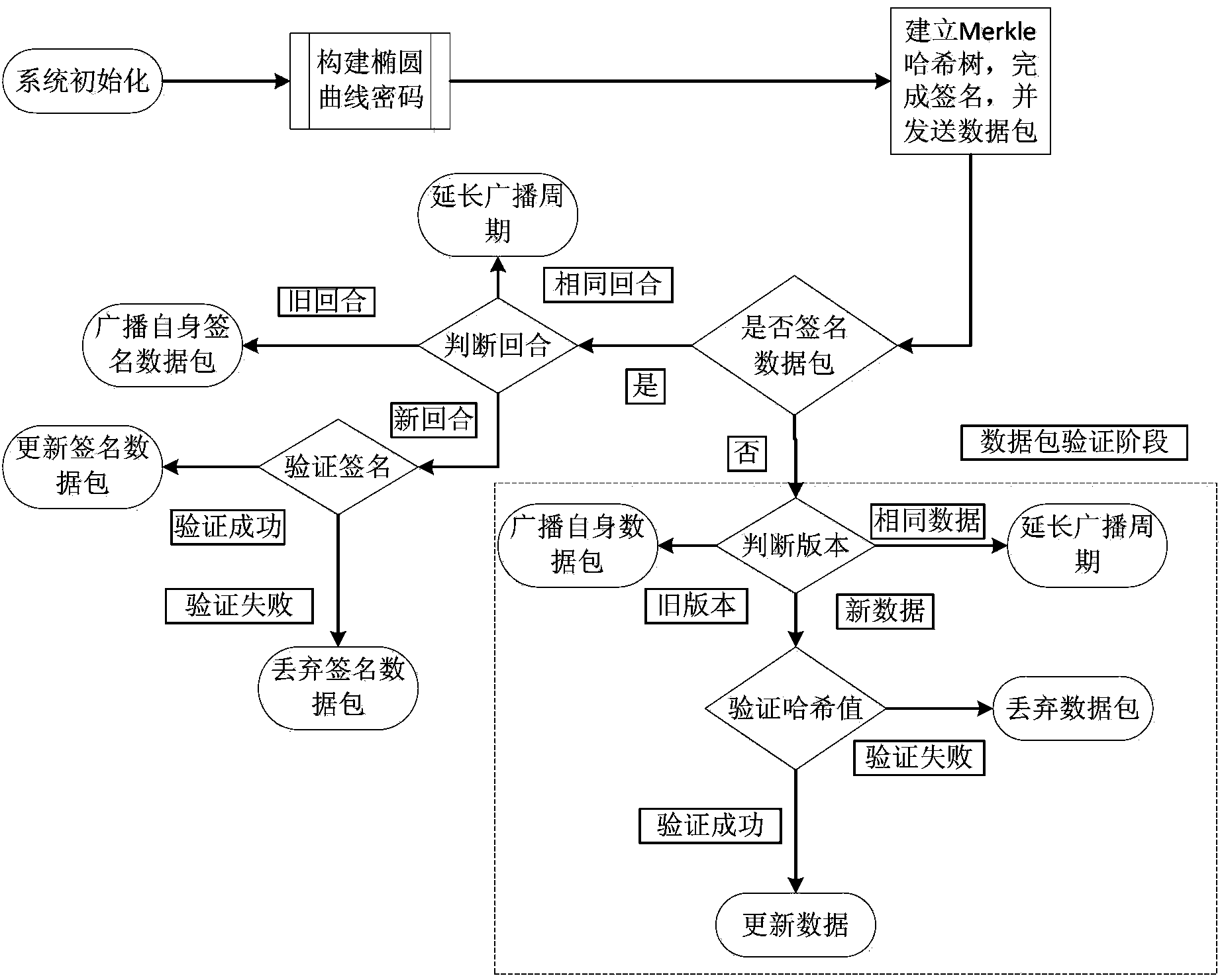
[0037] Such as figure 1 As shown, SeDrip is divided into three stages: system initialization, packet preprocessing and data packet verification.
[0038] In the system initialization phase, the base station obtains the private key SK and the public parameters {PK, Q, p, q, H(.)} by performing the following operations, where PK is the public key, thereby establishing an elliptic curve cryptosystem: the base station first selects a One-way hash function H(.), such as SHA-1, and choose an elliptic curve E about GF(p), where p is a large prime number. Use Q to represent the origin of E, and use another large prime number q to represent the order of Q. Furthermore, select the private key SK∈GF(q), and use the formula PK=SK*Q to generate the public key. Finally, each public parameter is preloaded into each node of the network. For example: in the 160-bit elliptic curve encryption, PK and Q are both 320-bit long, and p and q are both 160-bit long.
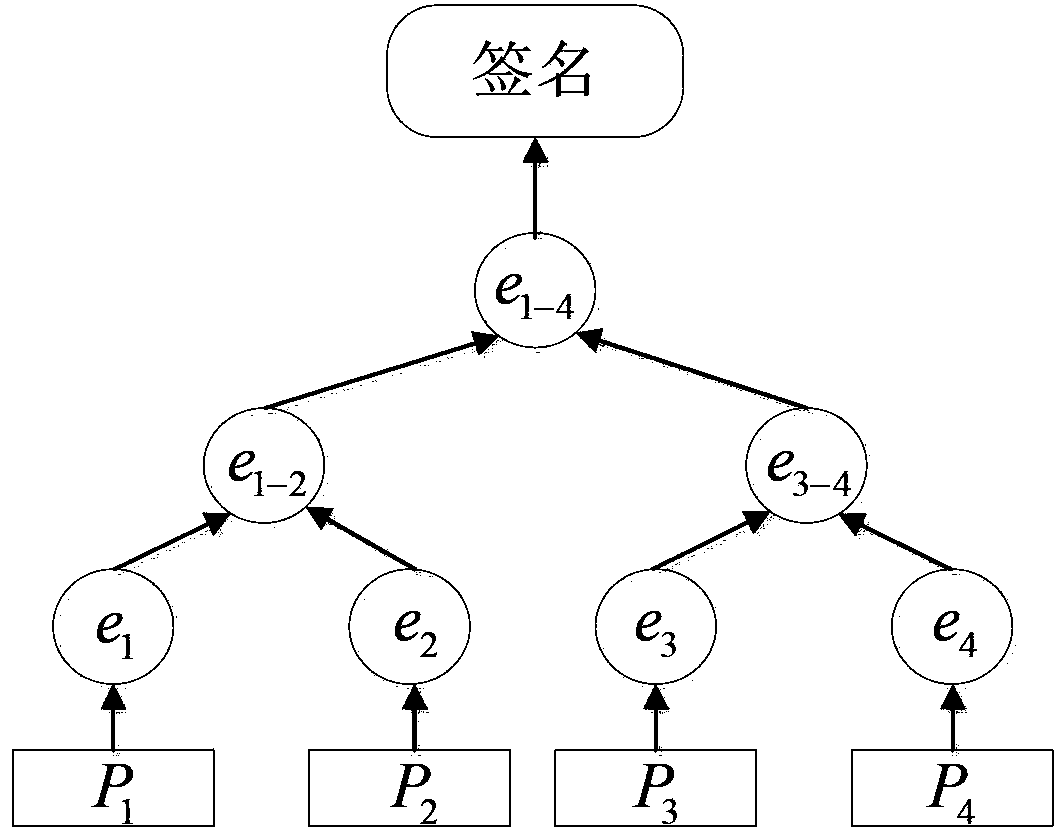
[0039] In SeDrip, a quadruple ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com