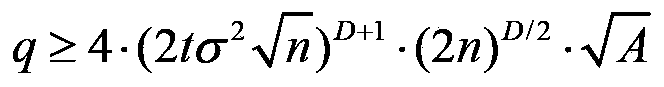Method and system for sequencing ciphertexts orienting to homomorphic encryption
A homomorphic encryption and ciphertext technology, which is applied in the field of multi-party computing and cryptography, can solve the problems that the ciphertext sequence cannot be determined, the ciphertext cannot be directly compared in size, and the calculation cannot be supported, so as to ensure data security and homomorphic encryption. The effect of ciphertext sequencing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
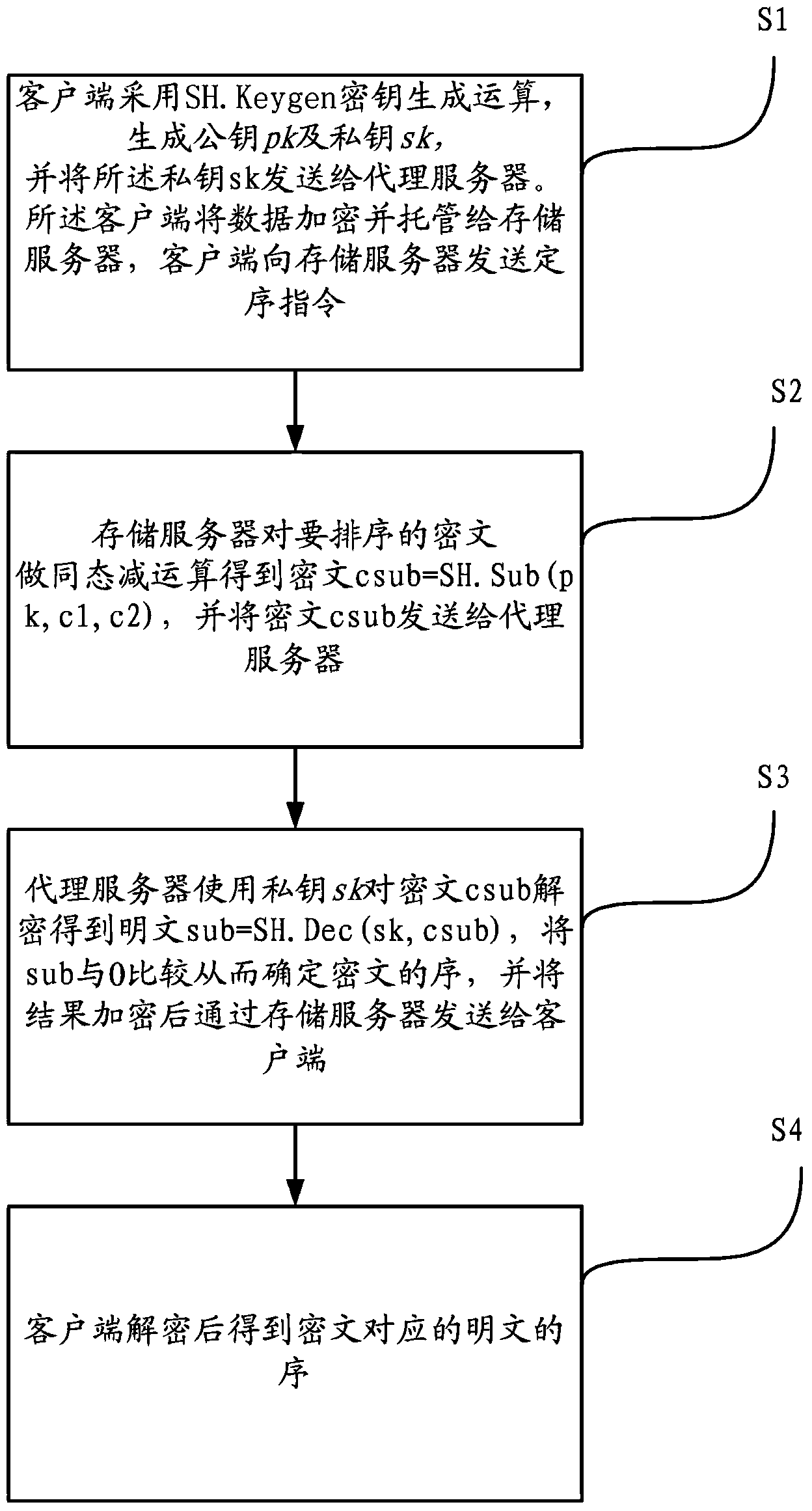
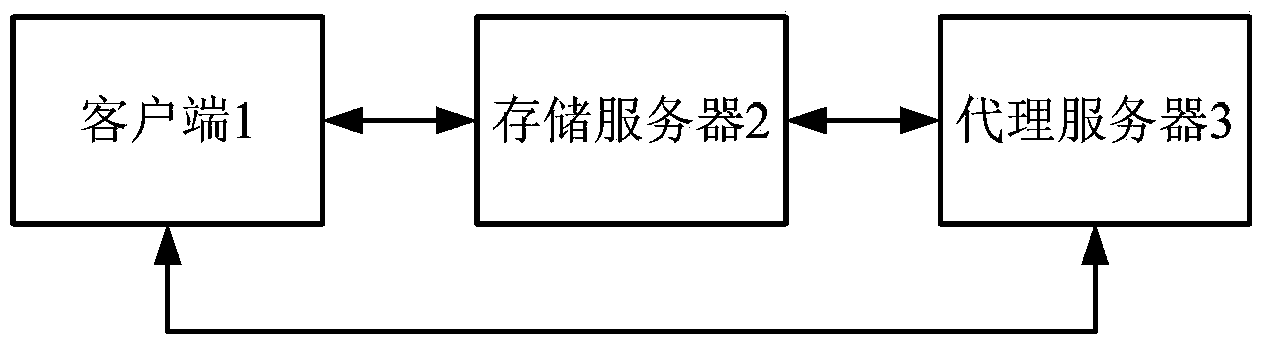
[0027] The present invention adopts the homomorphic encryption scheme on the RLWE with relatively high efficiency at present. In order to facilitate understanding, the principle of homomorphic encryption is introduced below.
[0028] First of all, parameter setting, the homomorphic encryption scheme selected by the present invention is on the polynomial ring, and the polynomial ring R=Z[X] / F(x), R q =R / qR=Z s [X] / F(X), the ciphertext space is R q . Here, the F(X) takes a circular polynomial, F(X)=Φ m (X)=(X m -1) / (X-1), where m is a prime number, this selection is to make full use of packing technology to improve space storage utilization. In addition, the dimension of F(X) is n=m-1, and the coefficients of the ciphertext polynomial are all modulo q, then the coefficient range of the corresponding polynomial is (-q / 2,q / 2]; in the discrete Gaussian distribution where σ is the standard deviation.
[0029] The plaintext space is R t = Z t [X] / F(X), t≡1(modm) (the paramet...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com