Method and device for user recognition
A user and current user technology, applied in the network field, can solve problems such as the inability to effectively identify the user's identity, and achieve the effect of ensuring uniqueness and timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
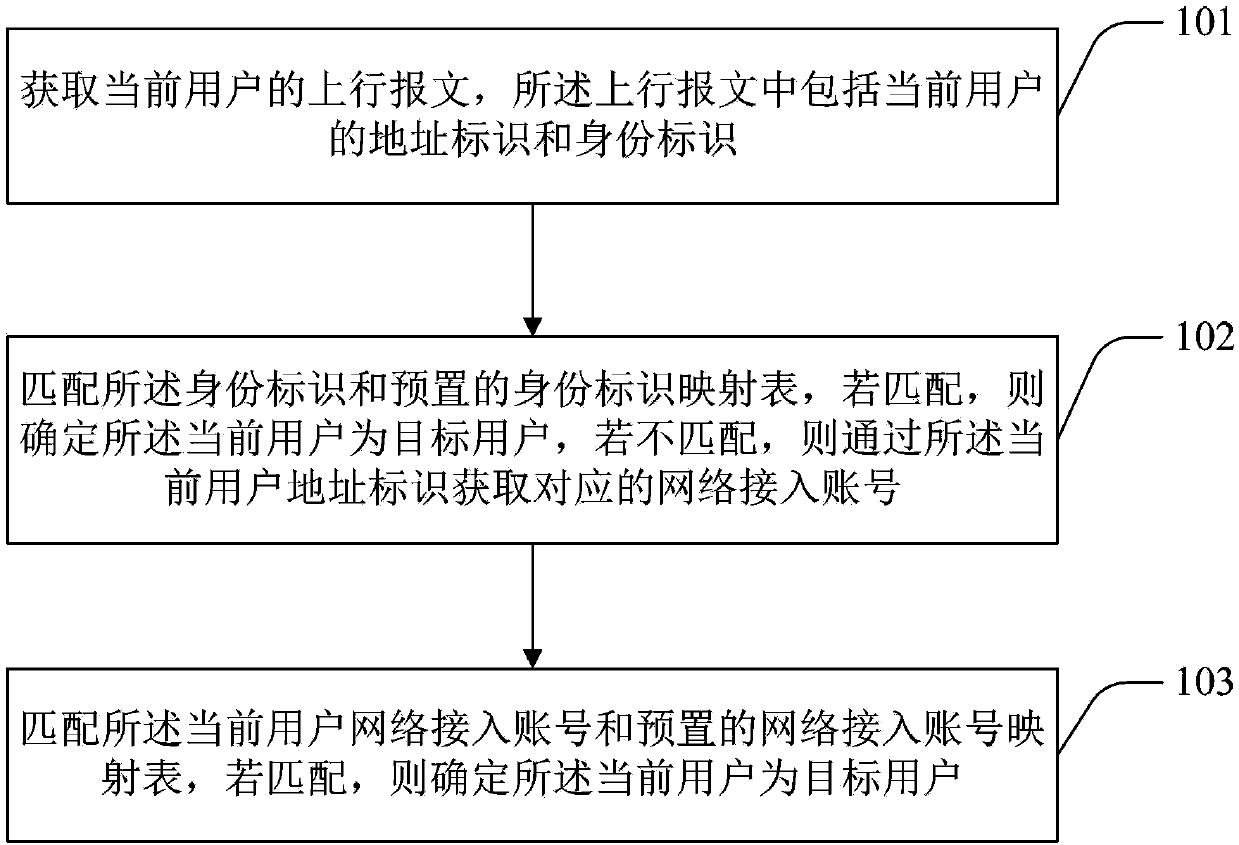
[0042] This embodiment provides a method for user identification, see figure 1 , the method includes:
[0043] In step 101, the uplink message of the current user is acquired, and the uplink message includes the address identifier and identity identifier of the current user.
[0044] The user's uplink message may be a Hypertext Transfer Protocol (Hypertext Transfer Protocol, HTTP) uplink message, or an uplink message based on other protocols, such as a File Transfer Protocol (File Transfer Protocol, FTP) uplink message, etc. .
[0045] The acquired uplink message of the user may be the uplink message sent by the user for the first time, or any uplink message sent during this communication process, which is not limited in the present invention. Taking a user accessing a website through a browser as an example, the user may click links multiple times when visiting the website, and each time the user clicks a new link, the HTTP uplink message of the current user can be obtained...
Embodiment 2
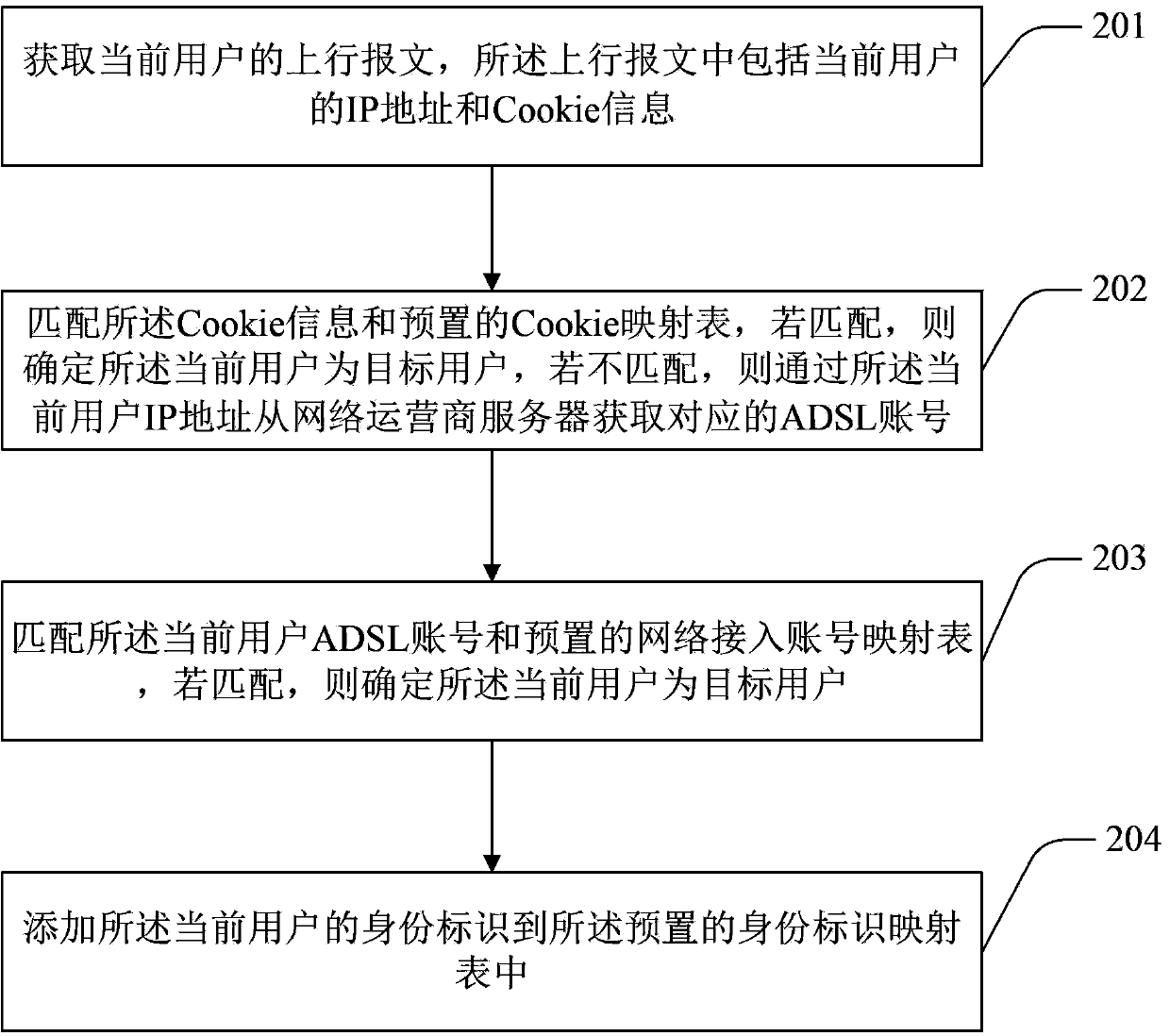
[0063] refer to figure 2 , shows a flow chart of a method for identifying a user according to Embodiment 2 of the present invention. In this embodiment, the IP address is used as the user address identifier, the Cookie information is used as the user identity identifier, and the ADSL account is used as the user network access account as an example for description. . The user identification method in this embodiment includes the following steps:
[0064] In step 201, the uplink message of the current user is obtained, and the uplink message includes the IP address and Cookie information of the current user.
[0065] Step 202, match the Cookie information with the preset Cookie mapping table, if they match, determine that the current user is the target user, if not, obtain the corresponding ADSL from the network operator server through the current user IP address account.
[0066] Step 203, matching the ADSL account of the current user with a preset network access account ma...
Embodiment 3
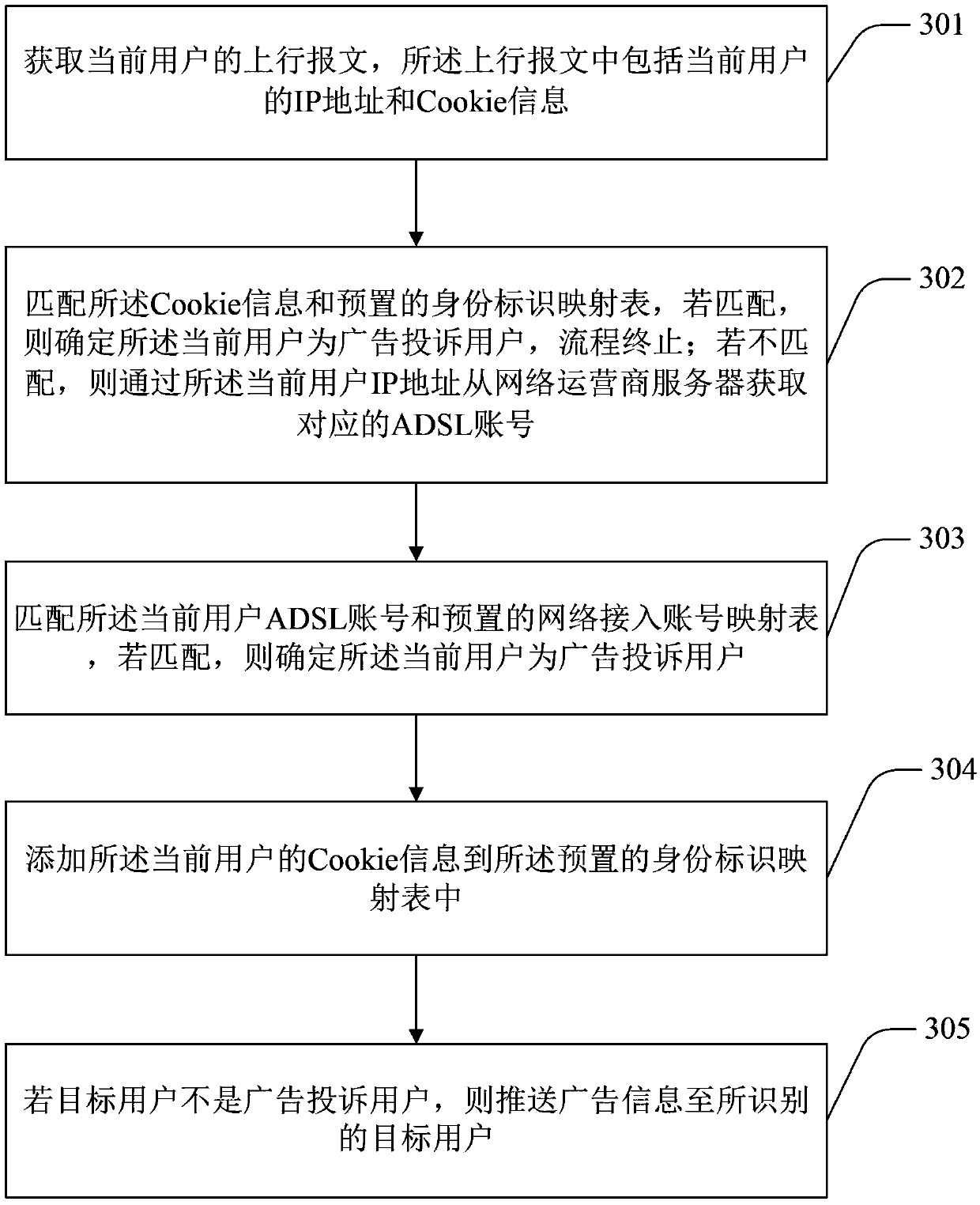
[0072] Embodiment 3 This implementation discloses another user identification method, see image 3 , the steps included in this embodiment are as follows:
[0073] In step 301, the uplink message of the current user is acquired, and the uplink message includes the IP address and Cookie information of the current user.
[0074] Step 302, match the cookie information with the preset identity mapping table, if they match, then determine that the current user is an advertisement complaint user, and the process ends; The server obtains the corresponding ADSL account.
[0075] Step 303, matching the ADSL account of the current user with the preset network access account mapping table, and if they match, determining that the current user is an advertisement complaint user.
[0076] Further, before the matching of the current user ADSL account and the preset network access account mapping table, it also includes: collecting the user network access account according to the preset fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com