Method and system for identifying Trojan horse behavior
A Trojan horse and behavior technology, applied in the field of Trojan horse behavior identification methods and systems, can solve the problem of insufficiently comprehensive Trojan horse behavior feature recognition, and achieve the effect of protecting the interests of information assets and comprehensive and accurate evidence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
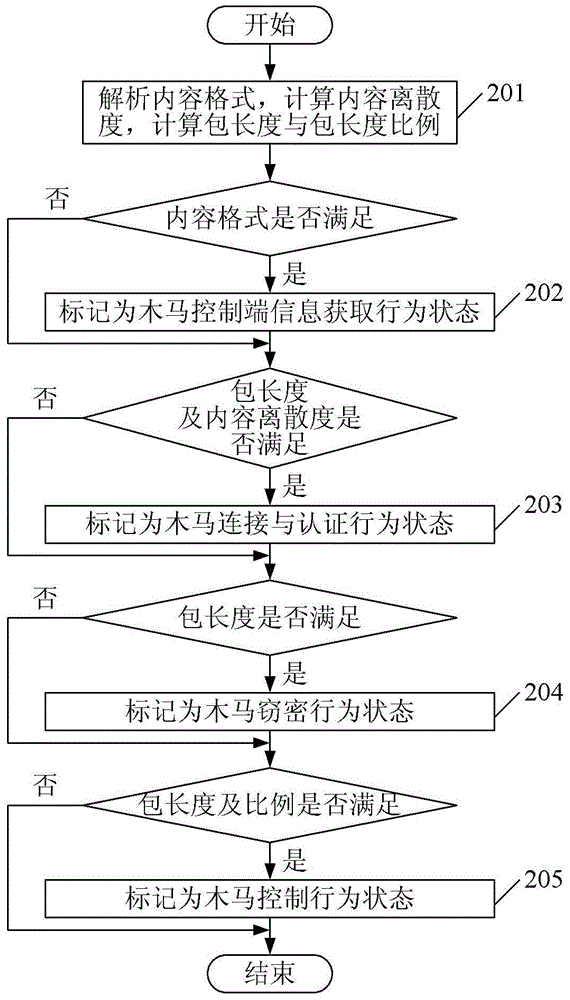
[0051] Embodiment 1. A method for identifying a Trojan horse behavior, comprising:
[0052] Configure Trojan behavior characteristics;
[0053] Capture network packets;
[0054] Identifying the Trojan horse behavior state of the network packet based on the Trojan horse behavior characteristics;
[0055] The identified Trojan horse behavior status is recorded, and the Trojan horse behavior is identified based on the record.
[0056] In an implementation manner of this embodiment, the Trojan horse behavior characteristics include any of the following situations or any combination thereof:
[0057] The response content is domain name: port or IP address: port format;
[0058] The length of the response packet is less than 200 bytes, and the content dispersion is greater than 0.3;
[0059] The length of the data packet sent from the internal network to the external network is greater than 200 bytes.
[0060] In this embodiment, the step of identifying the Trojan horse behavio...
Embodiment 2
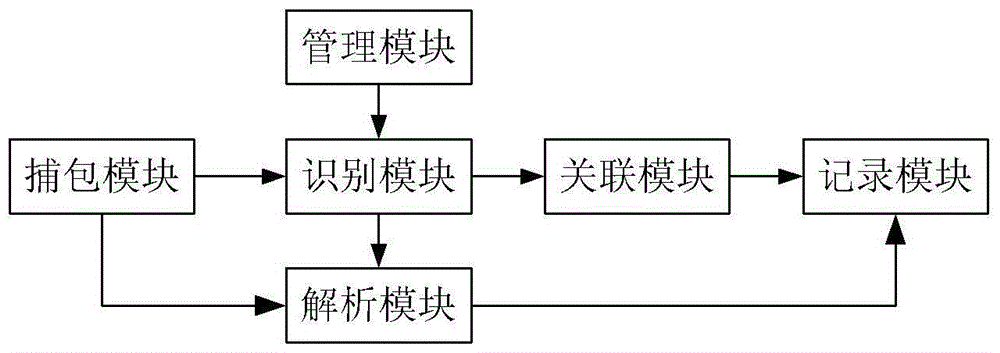
[0080] Embodiment two, a kind of identification system of Trojan horse behavior, such as figure 2 shown, including:
[0081] The management module is used to configure the behavior characteristics of the Trojan horse;
[0082] Packet capture module, used to capture network packets;
[0083] An identification module, configured to identify the Trojan horse behavior state of the network packet based on the Trojan horse behavior characteristics;
[0084] The association module is configured to record the identified behavior state of the Trojan horse, and identify the behavior of the Trojan horse based on the record.
[0085] In an implementation manner of this embodiment, the Trojan horse behavior characteristics include any of the following situations or any combination thereof:
[0086] The response content is domain name: port or IP address: port format;
[0087] The length of the response packet is less than 200 bytes, and the content dispersion is greater than 0.3;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com