Malicious program detection method
A malicious program and detection method technology, applied in the field of network security, can solve problems such as the difficulty of determination, the difficulty of killing or cleaning malicious programs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples, so that the realization process of how to use technical means to solve technical problems and achieve technical effects in the present invention can be fully understood and implemented accordingly.
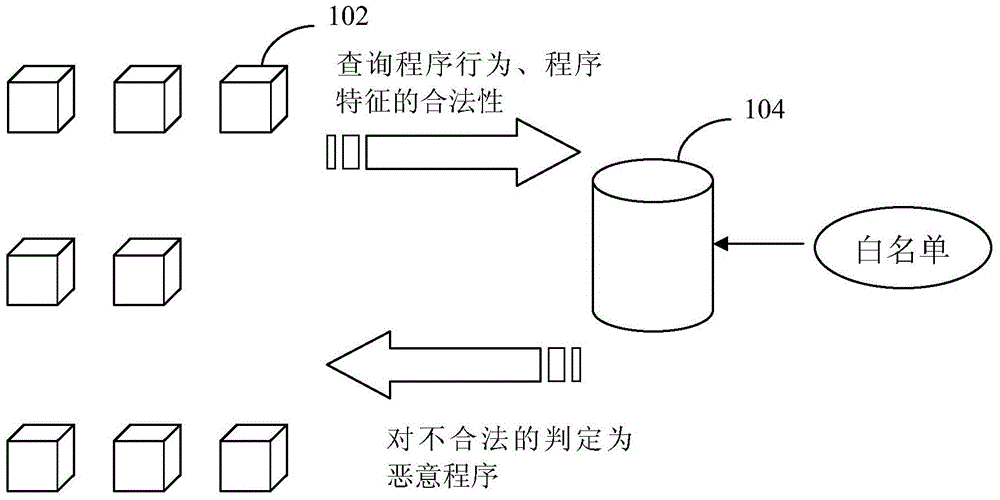
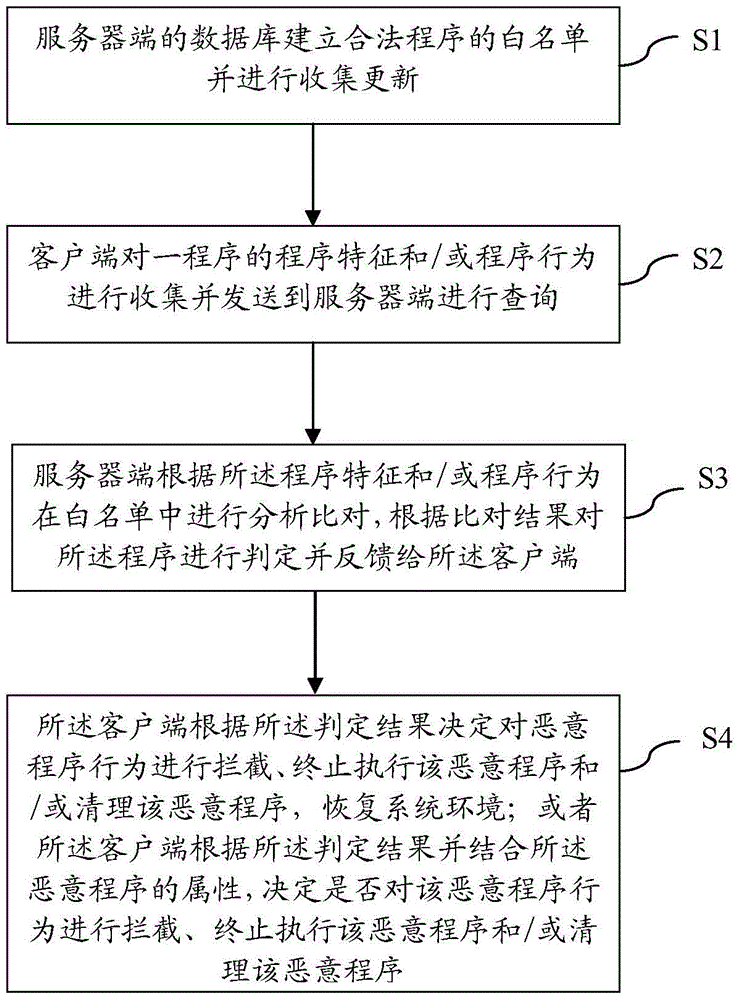
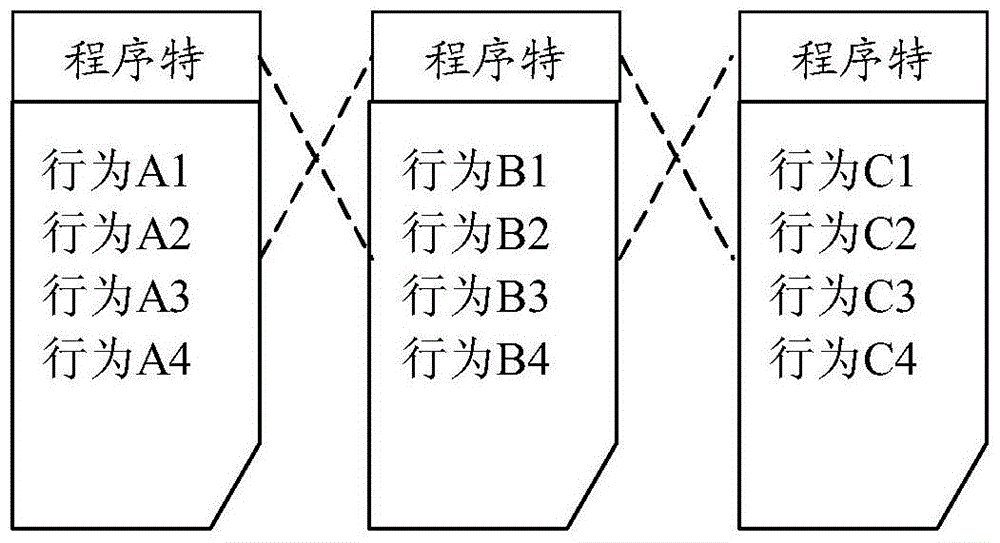
[0029] The core idea of the present invention is: the server-side database establishes a whitelist of legal programs and collects and updates them; The characteristics and / or program behaviors are analyzed and compared in the white list, and the program is judged according to the comparison result and fed back to the client.
[0030] The white list detection method for malicious programs in the cloud security mode composed of a large number of client computers 102 -servers 104 will be described below. A cloud fabric is a large client / server (CS) architecture such as figure 1 Shown is a schematic diagram of the implementation mode of the present inv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com