Database auditing method based on bridged mode
A database and pattern technology, applied in the direction of electrical digital data processing, special data processing applications, calculations, etc., can solve problems such as the inability to audit databases, and achieve the effect of improving data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
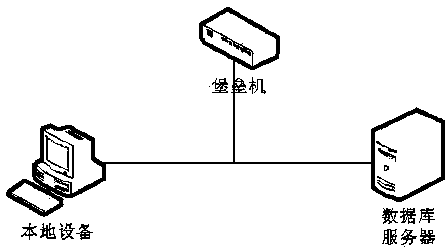
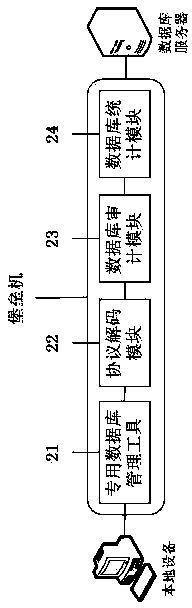
[0025] as attached figure 2 As shown, a kind of database auditing method based on bridge pattern of the present invention, specific implementation is as follows:
[0026] 1. The network port of the bastion machine is configured as a bridge mode, and is deployed on the intermediate path between the local device and the remote database server;
[0027] 2. On the local device, log in to the management system of the bastion host through a browser, and add information such as the IP address, port, database user name, and password of the remote database server;
[0028] 3. The management system of the bastion host can create a virtual desktop connection of the added remote database server through the protocol proxy mode, and the operation and maintenance user can connect to the remote database server through the special database management tool 21 to perform related operation and maintenance management operations;
[0029] 4. After the user logs in the special database management ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com