Security auditing method based on aspect oriented programming (AOP) and annotation information system
An annotation information and security audit technology, applied in the field of security audit based on AOP and annotation information system, can solve problems such as complex processing, high coupling, and reduced code readability, so as to reduce workload, shorten construction period, and solve speed reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
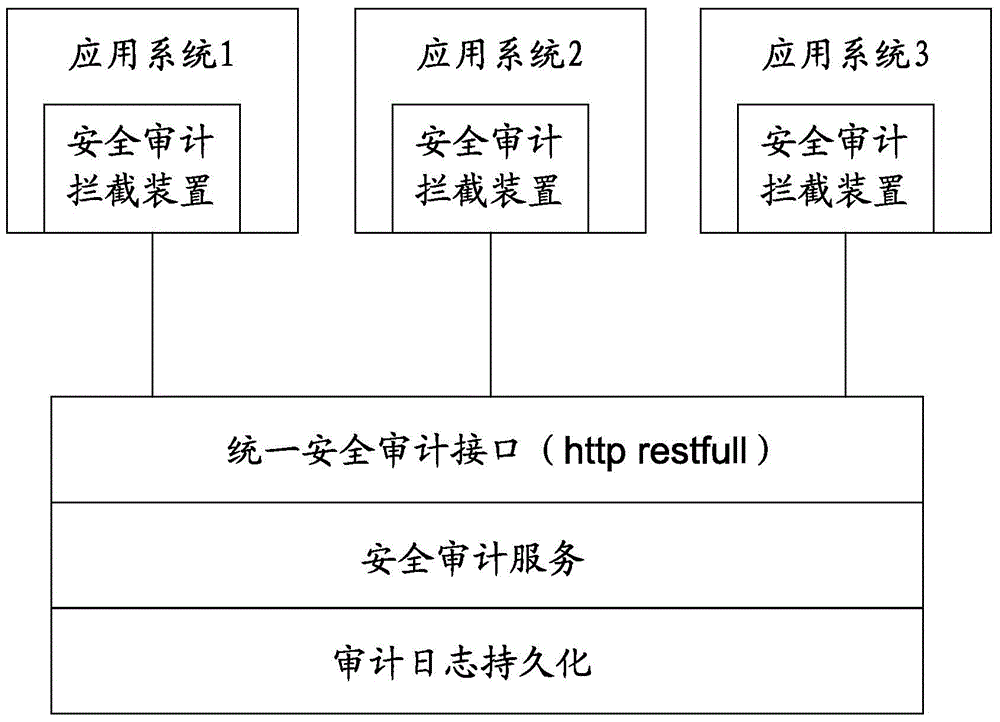
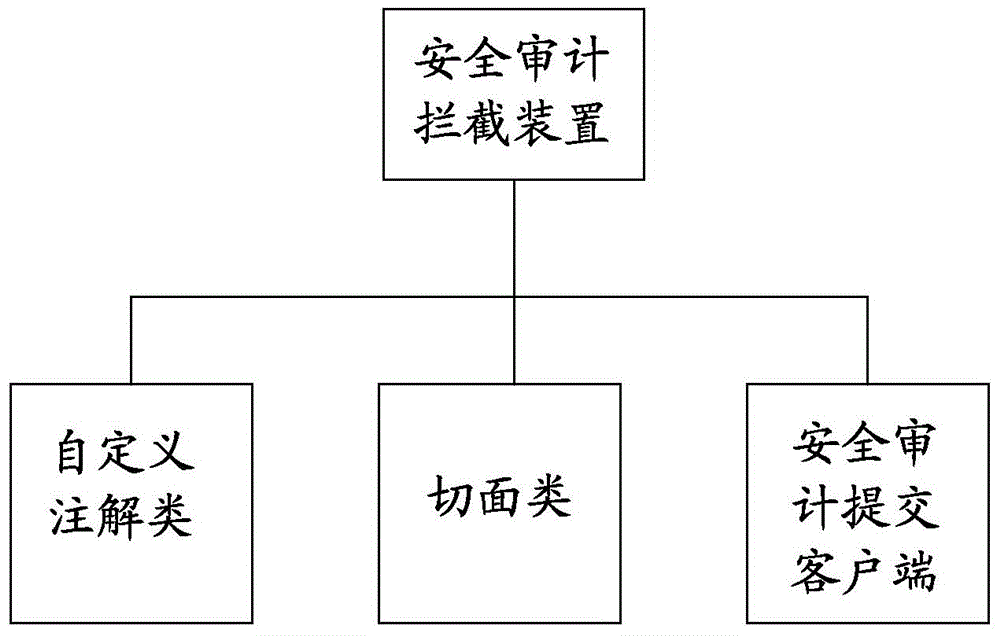
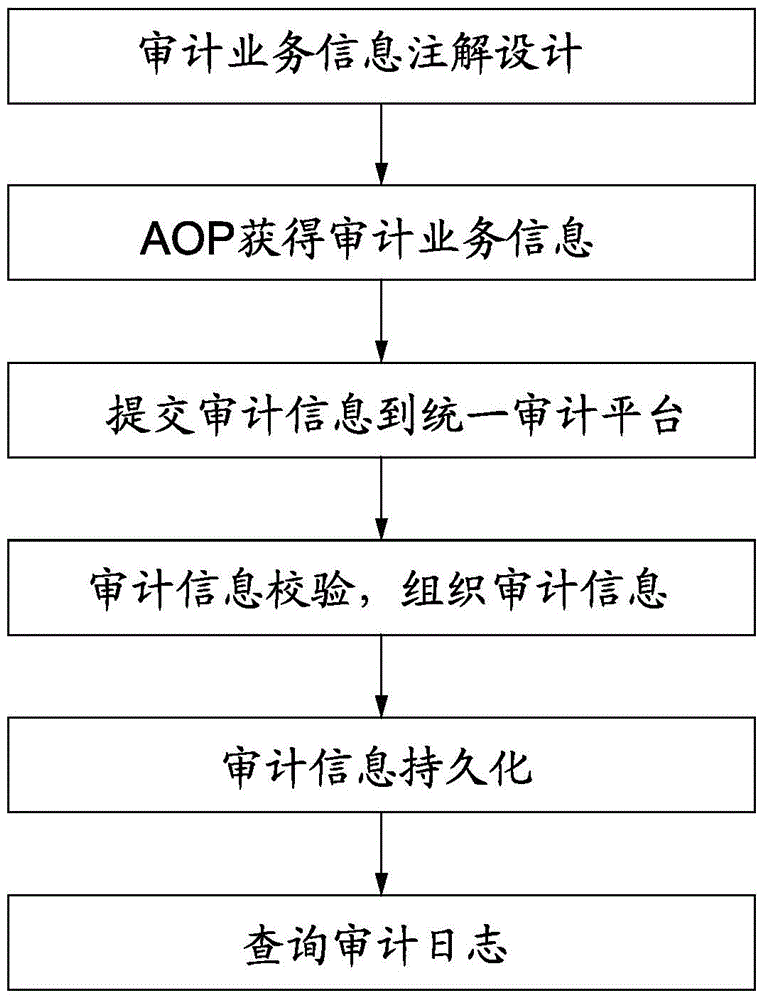
[0048] In the present invention, all application systems uniformly store their safety audit information on the safety audit platform, such as figure 1 Shown. Business systems (such as collaborative office, quality system, etc.) no longer continue to store security audit logs; the security audit log platform provides external security audit log services (only add and query interfaces are provided), and the security audit log platform also provides user-oriented security Audit log query service (that is, you can directly query the security audit log through the query interface provided by the security audit log platform). Due to the centralized management of security audit logs, the audit logs need to be managed in a sub-system. For example, an audit administrator in a collaborative office cannot retrieve the audit logs of the quality system or other application systems. Each application system does not need to build a security audit module, but only needs to introduce a security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com