Method, equipment and system used for realization of intelligent entrance guard
A smart access control and access control technology, applied in the field of access control, can solve problems such as potential safety hazards, cumbersome processes, and unsuitable scenarios for temporary use, and achieve the effect of cost saving and wide application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
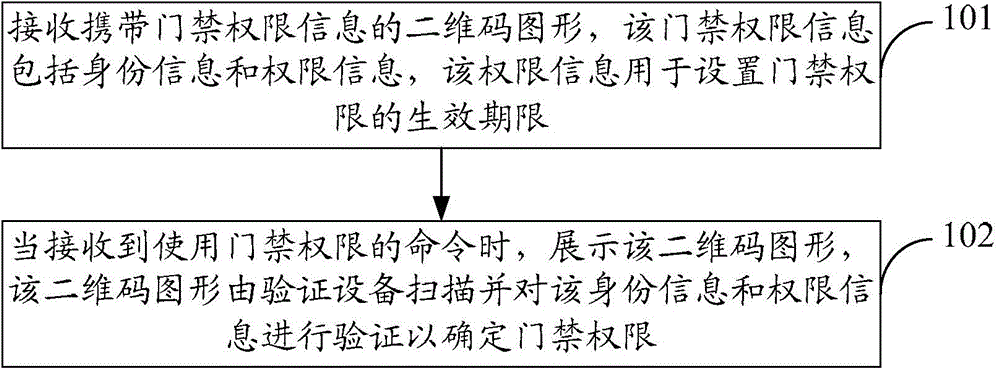
[0062] see figure 1 , this embodiment provides a method for implementing intelligent access control, including the following steps.
[0063] In step 101, a two-dimensional code pattern carrying access control authority information is received, the access control authority information includes identity information and authority information, and the authority information is used to set an effective period of access control authority.
[0064] Wherein, the two-dimensional code pattern is obtained by converting the access control authority information into two-dimensional codes. The access control authority information is a string of characters, which can be converted into a two-dimensional code to obtain a two-dimensional code graphic. The identity information may be an identity ID, and the identity ID is unique.
[0065] In step 102, when the command to use the access control authority is received, the two-dimensional code pattern is displayed.
[0066] Wherein, the two-dimen...
Embodiment 2
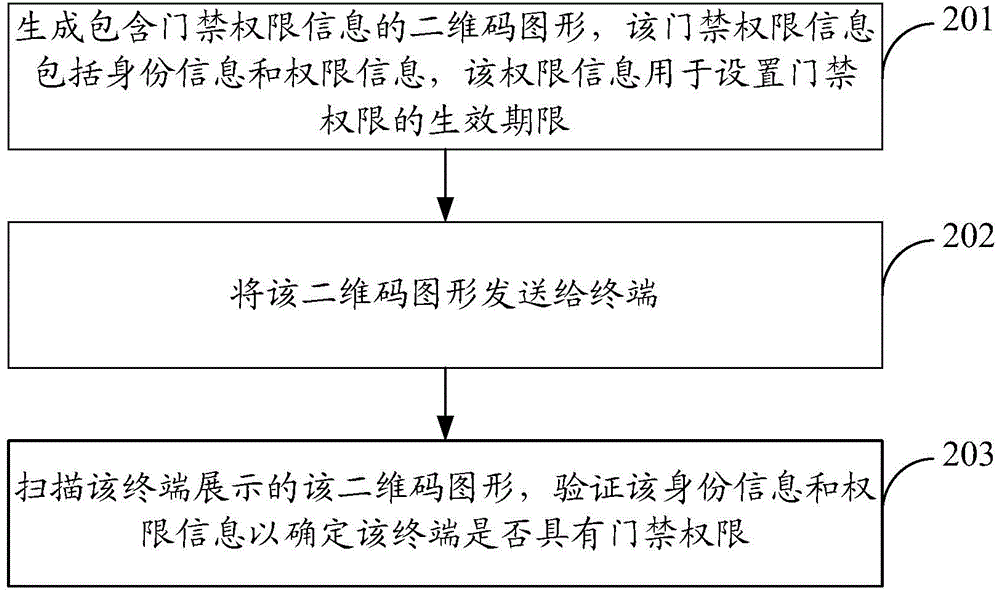
[0075] see figure 2 , this embodiment provides a method for implementing intelligent access control, including the following steps.
[0076] In step 201, generate a two-dimensional code graphic containing access control authority information, the access control authority information includes identity information and authority information, and the authority information is used to set the effective period of the access control authority;
[0077] Wherein, the two-dimensional code pattern is obtained by converting the access control authority information into two-dimensional codes. The access control authority information is a string of characters, which can be converted into a two-dimensional code to obtain a two-dimensional code graphic. The identity information may be an identity ID, and the identity ID is unique.
[0078] In step 202, the two-dimensional code graphic is sent to the terminal;
[0079] In step 203, the two-dimensional code pattern displayed by the terminal ...
Embodiment 3
[0092] see image 3 , this embodiment provides a method for implementing intelligent access control, including the following steps.
[0093] In step 301, receive a two-dimensional code graphic carrying access control authority information, the access control authority information includes identity information and authority information, the authority information is used to set the effective period of the access control authority, and the authority information includes the effective time of the access control authority and / or effective times.
[0094] Wherein, the two-dimensional code pattern is obtained by converting the access control authority information into two-dimensional codes. The access control authority information is a string of characters, which can be converted into a two-dimensional code to obtain a two-dimensional code graphic. The identity information may be an identity ID, and the identity ID is unique.
[0095] By setting the effective time and / or effective...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com