Cloud service identity authentication method and device
An identity authentication and cloud service technology, applied in the field of cloud service identity authentication methods and equipment, can solve problems such as personal property loss, lack of security, data loss, etc., to avoid waste of network resources, improve user experience, and enhance security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
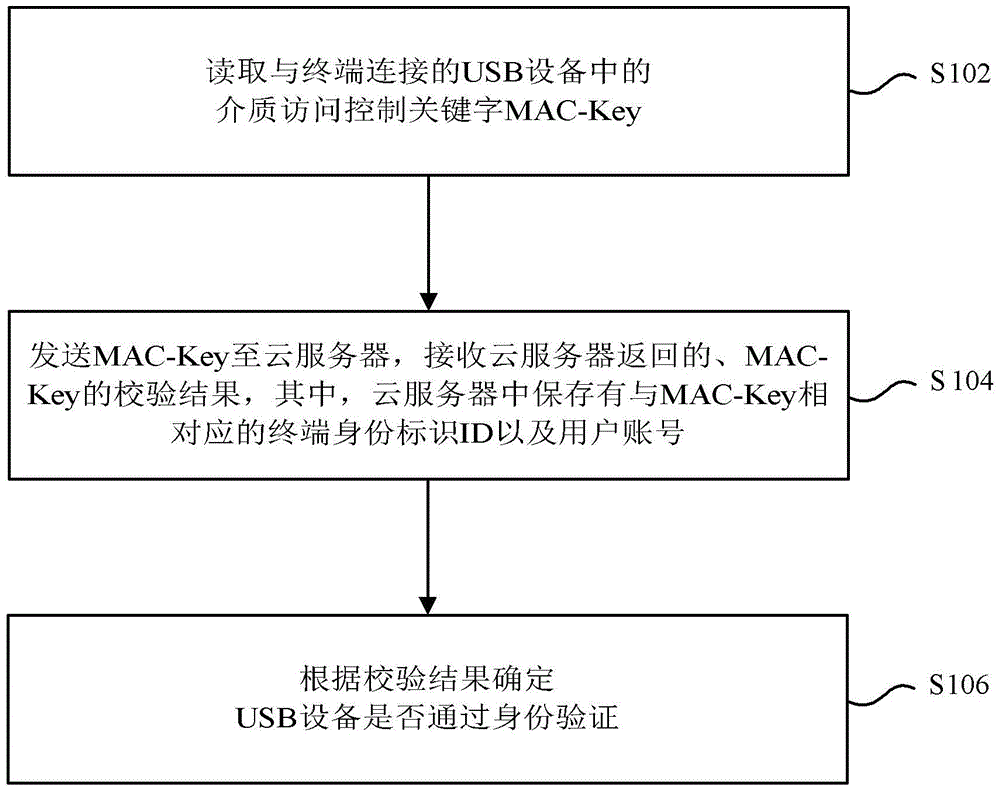
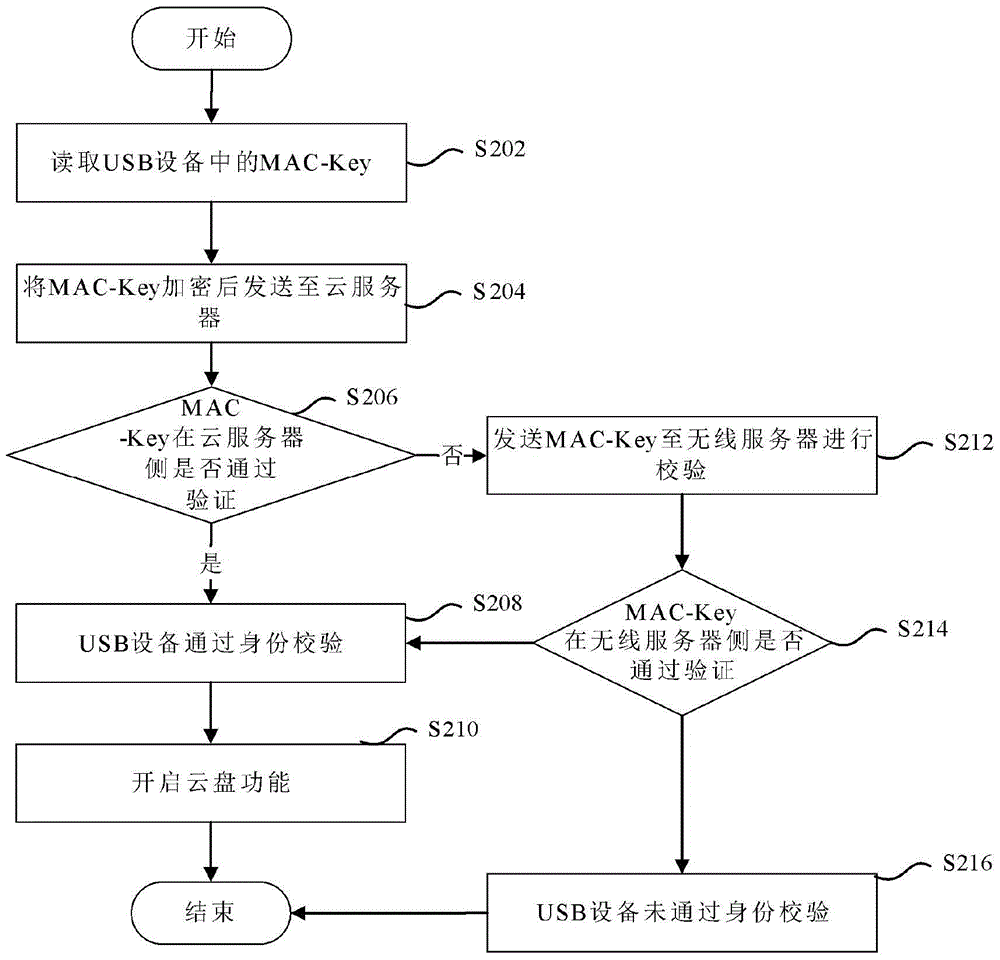
[0054] figure 2 The flowchart showing the processing of the cloud service identity authentication method according to a preferred embodiment of the present invention is used to support any of the above cloud service identity authentication methods, so as to make the above cloud service identity authentication method more clear and understandable. It should be noted that, in order to explain this preferred embodiment more concisely and easily, in this preferred embodiment, the terminal is set as a computer. see figure 2 , this preferred embodiment includes at least step S202 to step S216.
[0055] Step S202, read the MAC-Key in the USB device.
[0056]Connect the USB device to the terminal, and a prompt box will pop up in the lower right corner of the computer, prompting that it will take 3 minutes to successfully connect the USB device to the terminal. During the connection process, if the USB device is not compatible with the current system of the computer, a prompt wind...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com