Account number single sign on protecting method and device
A single sign-on and protection device technology, applied in the transmission system, electrical components, etc., can solve the problems of stealing user virtual property and user loss, achieve the effect of protecting personal information and virtual property, and improving system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
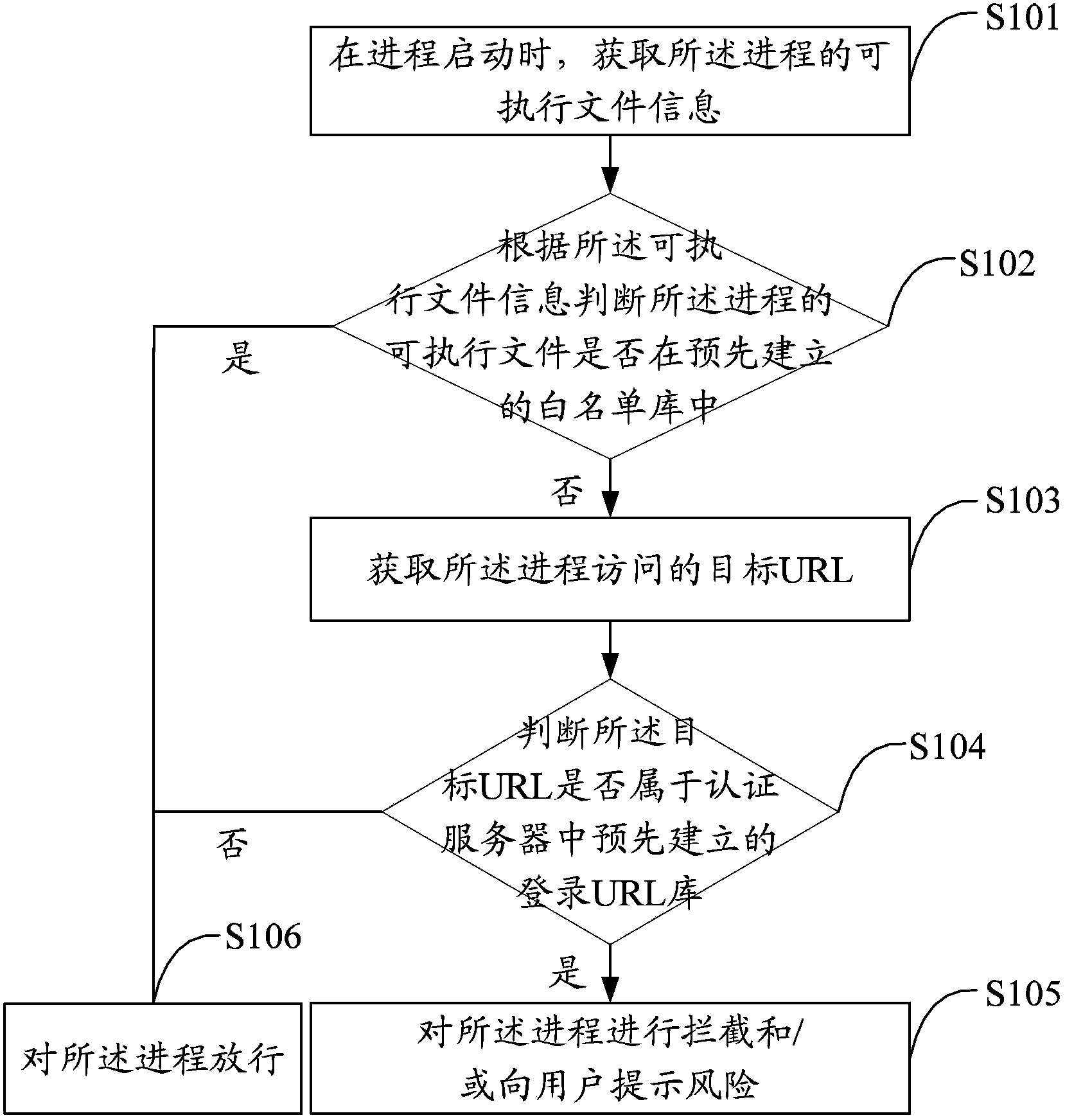
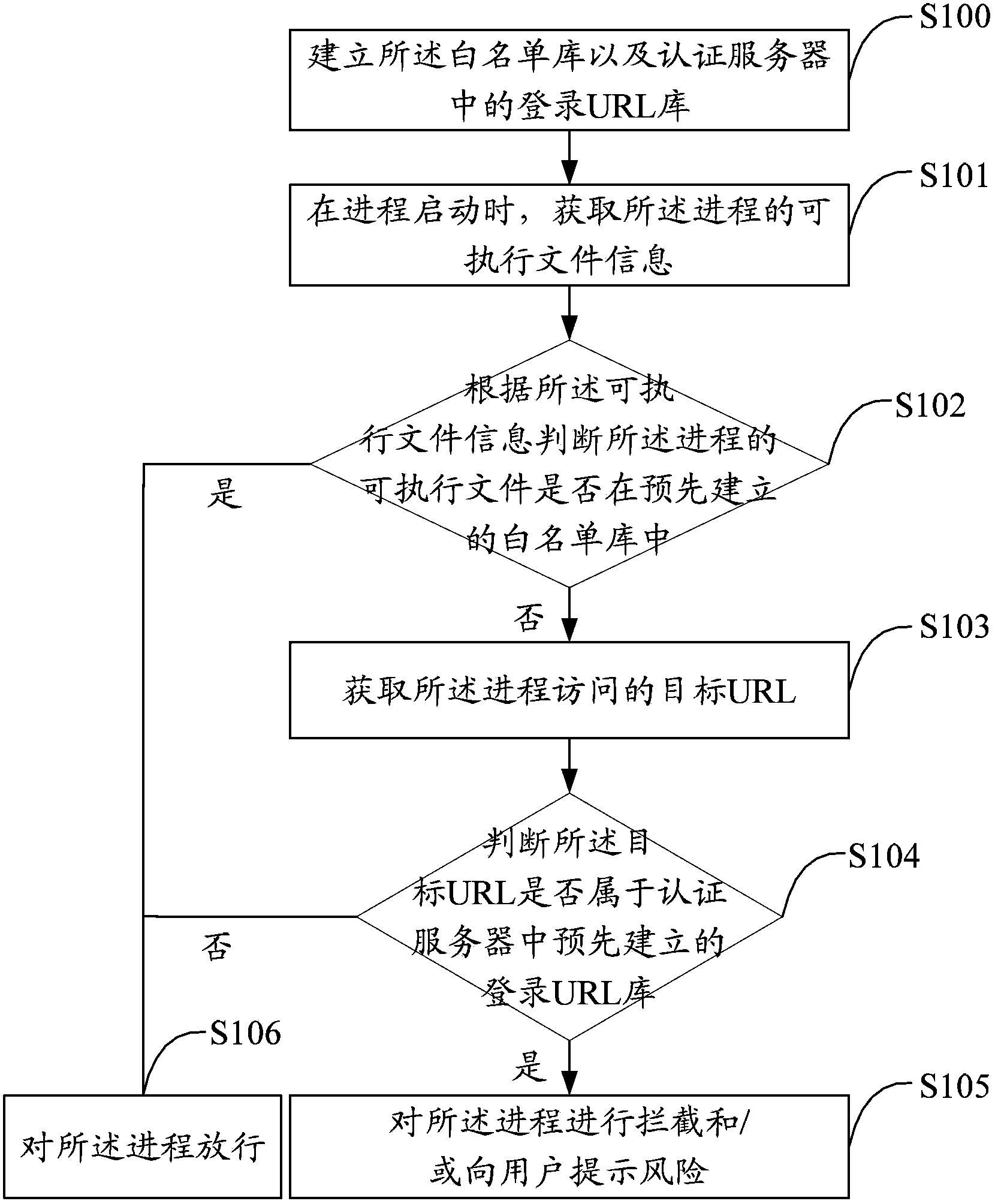
[0024] The solution of the embodiment of the present invention is mainly: through the URL (Uniform / Universal Resource Locator, Uniform / Universal Resource Locator) of the pre-established whitelist library and an authentication server to log in to the library, when a program not in the whitelist library accesses the URL of the authentication server When logging in to the URL contained in the library, the process is intercepted or the risk is prompted to the user, so as to protect the security of the single sign-on of the user account system.
[0025] Such as figure 1 As shown, the first embodiment of the present invention proposes an account single sign-on protection method, including:
[0026] Step S101, when the process starts, obtain the executable file information of the process;
[0027] In this embodiment, by means of injection, any account SSO process is injected to obtain the executable file information of the process, and the executable file information includes the na...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com