Method and apparatus for determining a cryptographic key in a network
A cryptographic key, network technology, applied in the field of computer program products
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] In the following description of preferred exemplary embodiments of the present invention, the same or similar reference signs are used for elements shown in different figures and acting similarly, wherein a repeated description of these elements is omitted.
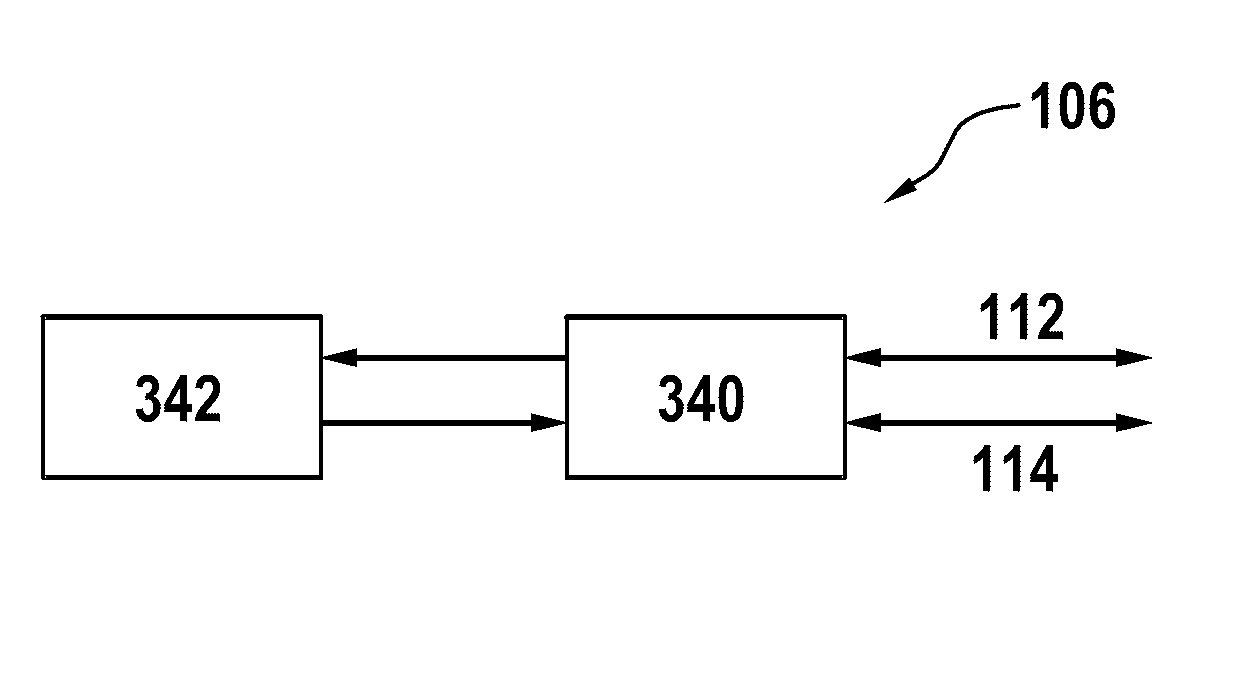
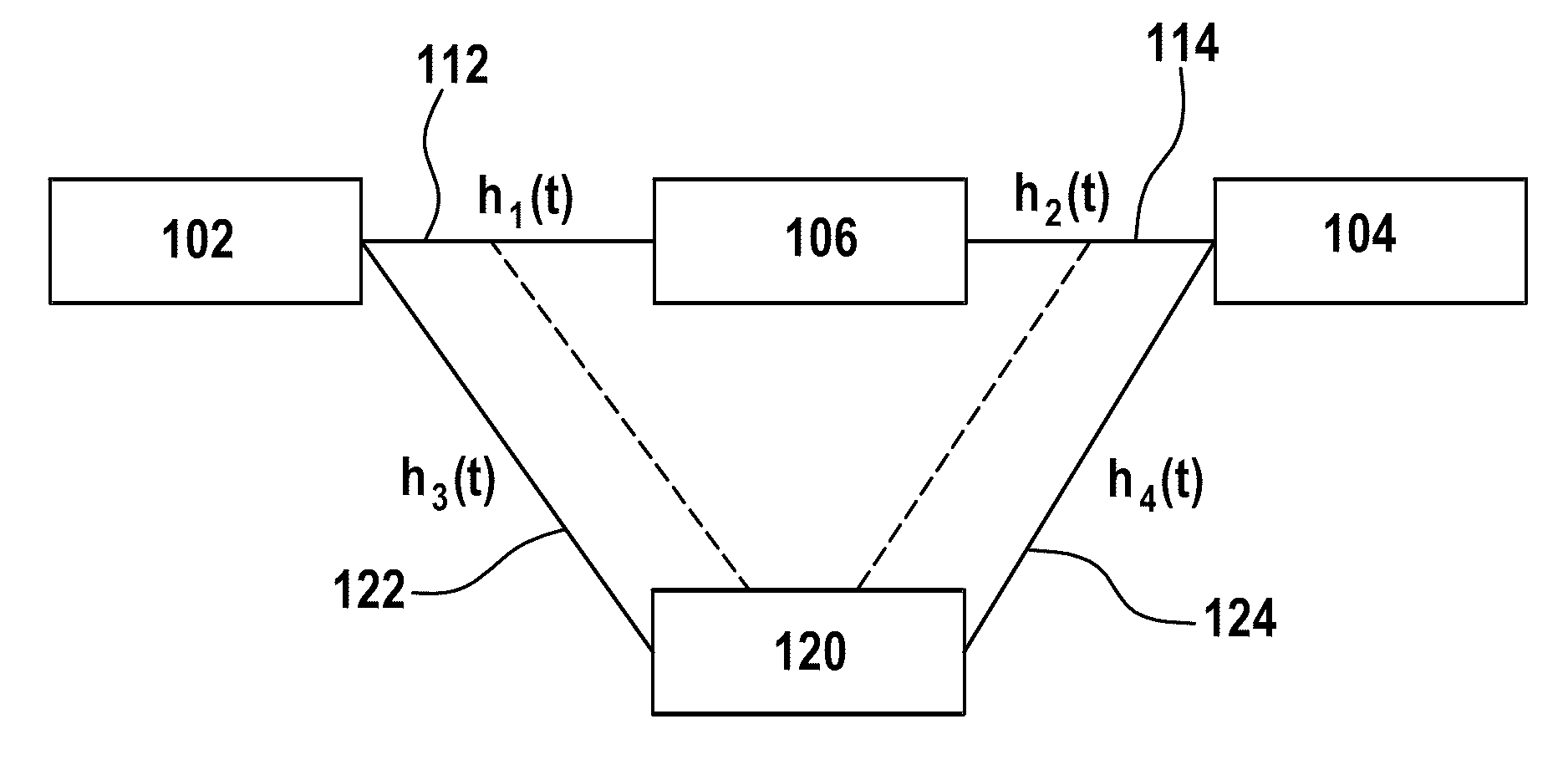
[0052] figure 1 A schematic diagram of a network according to an embodiment of the present invention is shown. A network with a first network element 102 , a second network element 104 and a network node 106 is shown. The first network element 102 is also denoted Alice, the second network element 104 is also denoted Bob and the network node 106 is also denoted Max. In general, network elements 102, 104 and network nodes 106 may also be generally referred to as nodes.
[0053]The first network element 102 can communicate with the network node 106 via the first transmission channel 112 , whereby data can be transmitted between the first network element 102 and the network node 106 via the first transmission channel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com