File renaming method and system
A technology of renaming and file, applied in the direction of file system, file system function, special data processing application, etc., can solve the problems of complicated operation, heavy workload, poor user experience, etc., to improve experience and reduce workload Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
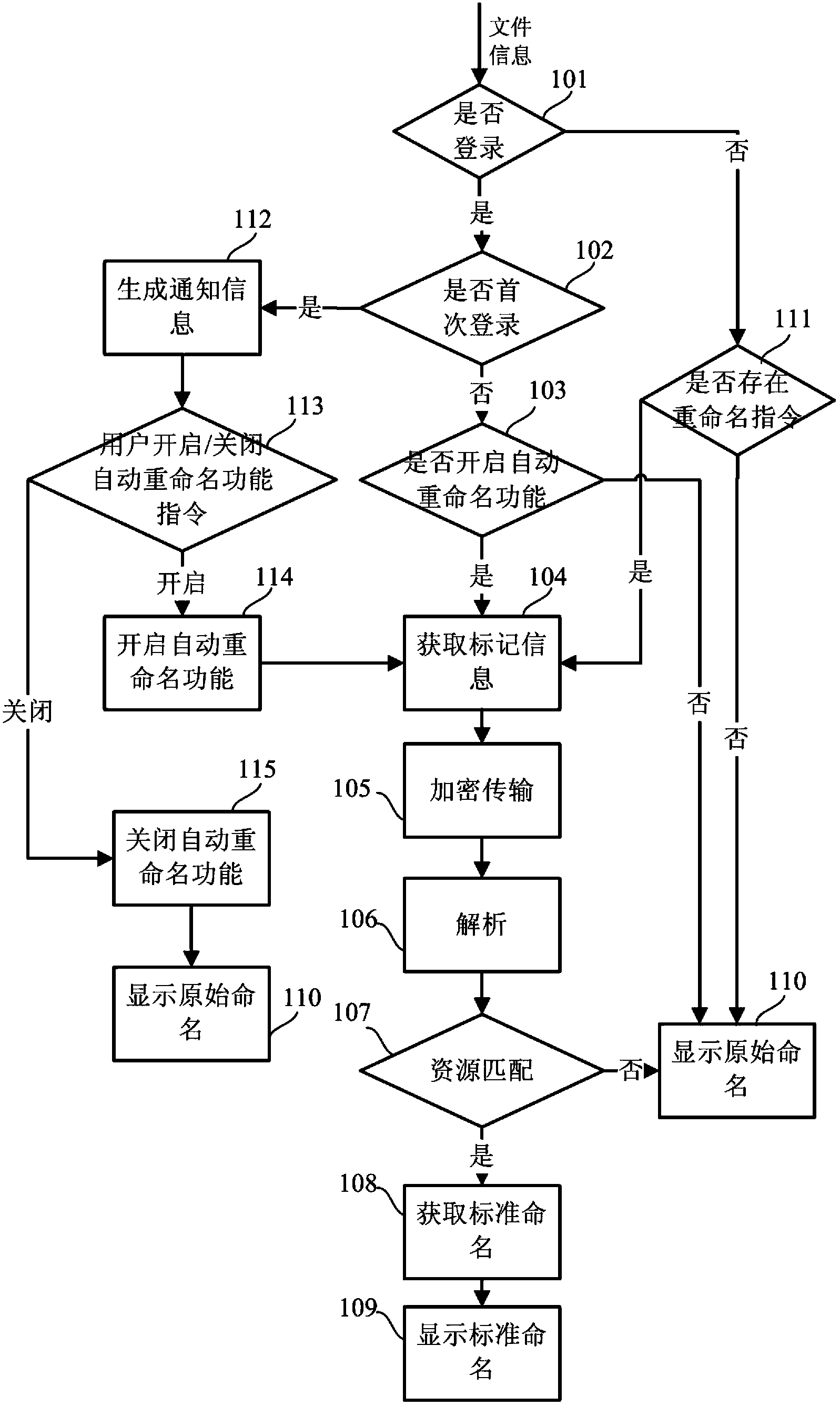
[0015] Please refer to figure 1 , the file renaming method provided by the present embodiment includes the following steps:
[0016] Step 101, judging whether there is the user's login information, the judging method may be that the client sends a query request for querying the user's login information to the server, and after the server receives the query request, if the user is in the login state, the user's login information is sent to the server. Return to the client. If the user is offline, that is, not in the login state, the query failure information will be returned to the client.
[0017] In step 102, after it is determined in step 101 that the user's login information exists, in step 102 continue to determine whether the user is in the first login state. The judging method can be that after the user logs in to the client, the client searches the local resources to see if there is any previous login information of the user. If it exists, it can be judged that it is n...
Embodiment 2
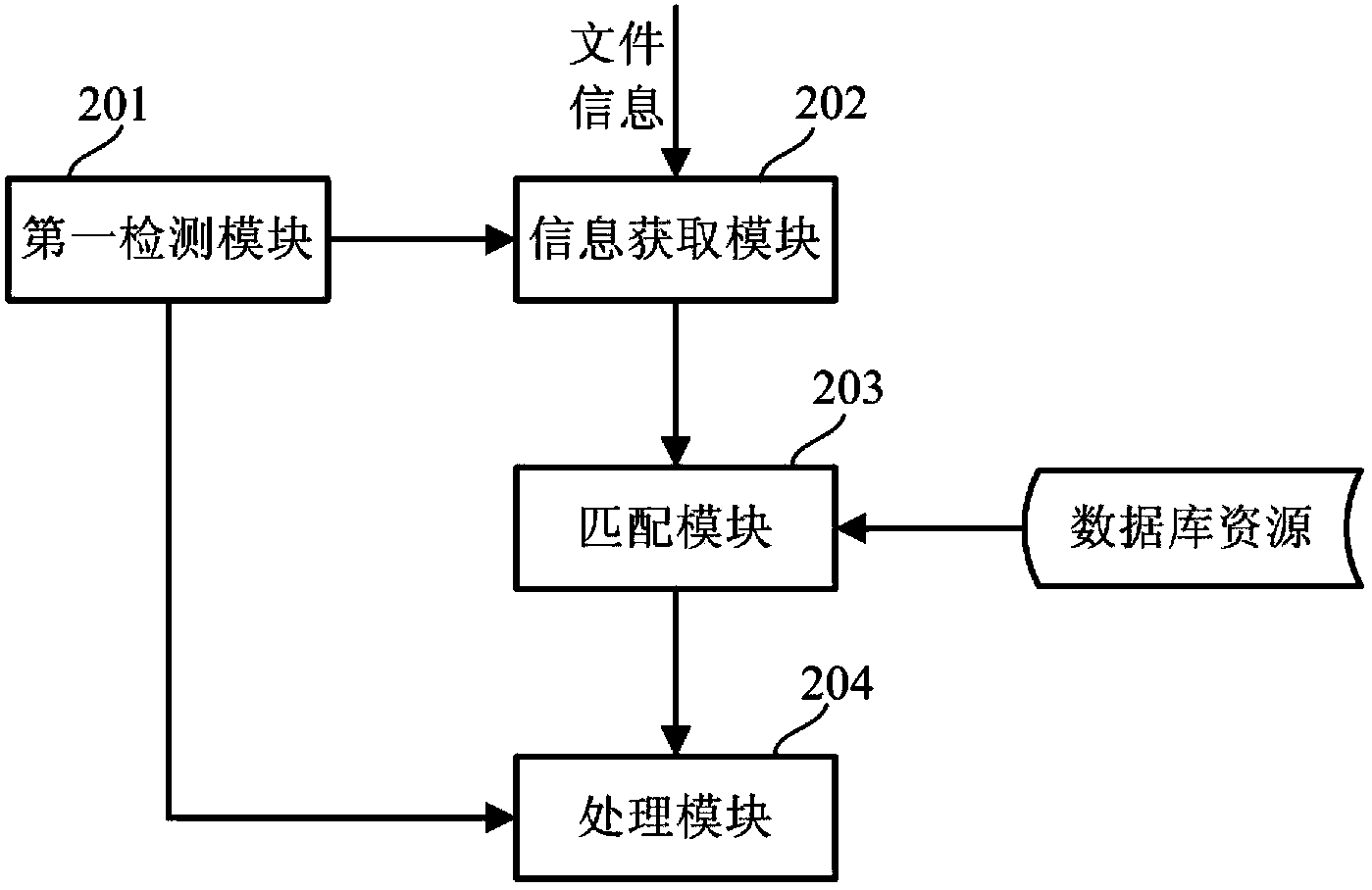
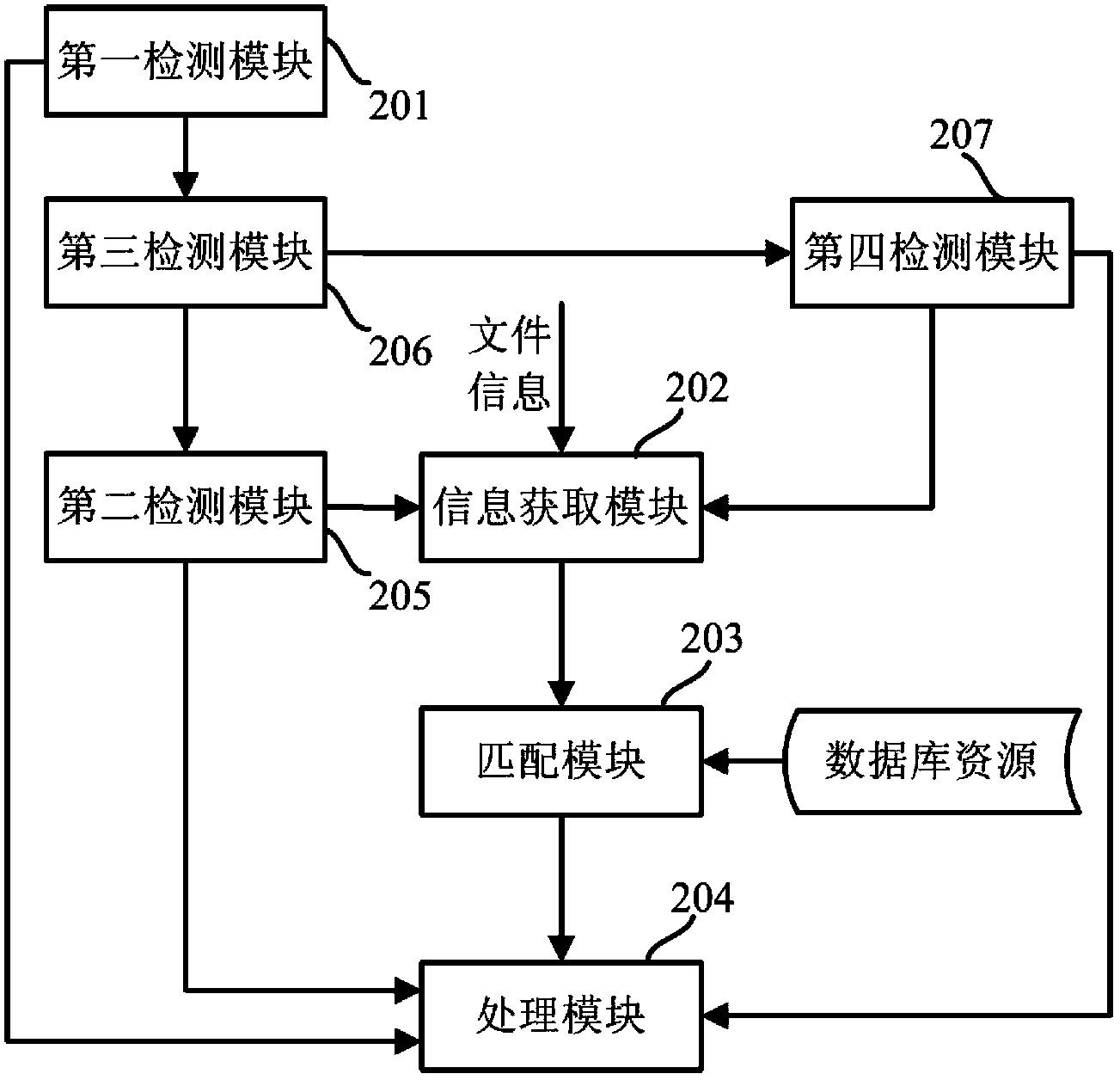
[0033] Please refer to figure 2 , the file renaming system provided in this implementation includes a first detection module 201 , an information acquisition module 202 , a matching module 203 and a processing module 204 .
[0034]The first detection module 201 is used to detect whether there is the login information of the user. The detection method may be that the first detection module 201 sends a query request for querying the user login information to the server. After the server receives the query request, if the user is in the login state , the user’s login information is returned to the first detection module 201, and if the user is offline, that is, not in the login state, the query failure information is returned to the first detection module 201. When the first detection module 201 detects that there is a user's login information, an instruction is sent to the information acquisition module 202. After the information acquisition module 202 acquires the instruction,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com