Virtual machine safety monitoring method based on behavior recognition
A security monitoring and virtual machine technology, applied in the field of virtual machine security, can solve problems such as difficult to achieve efficient application, incomplete, fuzzy security boundaries, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
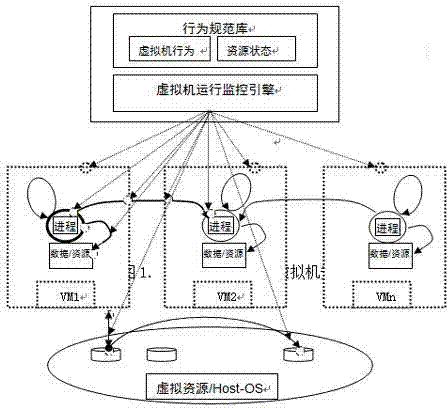
[0024] figure 1 A reference implementation scheme of the present invention is given, which mainly involves monitoring functional entities, including virtual machine operation monitoring engine and behavior characteristic specification library, virtual machine, virtual resources and underlying operating system Host-OS. Among them, the dotted circle represents the key monitoring point of behavior and the critical identification point of resource state, the line with the arrow represents the key access inside the virtual machine process and the access between virtual machines, and the line with the arrow represents the connection between the virtual machine and the underlying resource / operating system Access includes virtual machine migration. The hardware under the underlying main operating system Host-OS includes: servers, storage devices, networks, etc. are not shown.
[0025] The realization steps of this invention realization scheme are as follows:
[0026] 1) Build a virt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com