Privacy matching method based on exchange encryption in social network
A social network and privacy technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve the problems that multiple users cannot perform independent matching, cumbersome matching operations, time-consuming calculations, etc., to prevent frequent matching attacks, The effect of protecting privacy and reducing the amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] Example 1, both users perform privacy matching
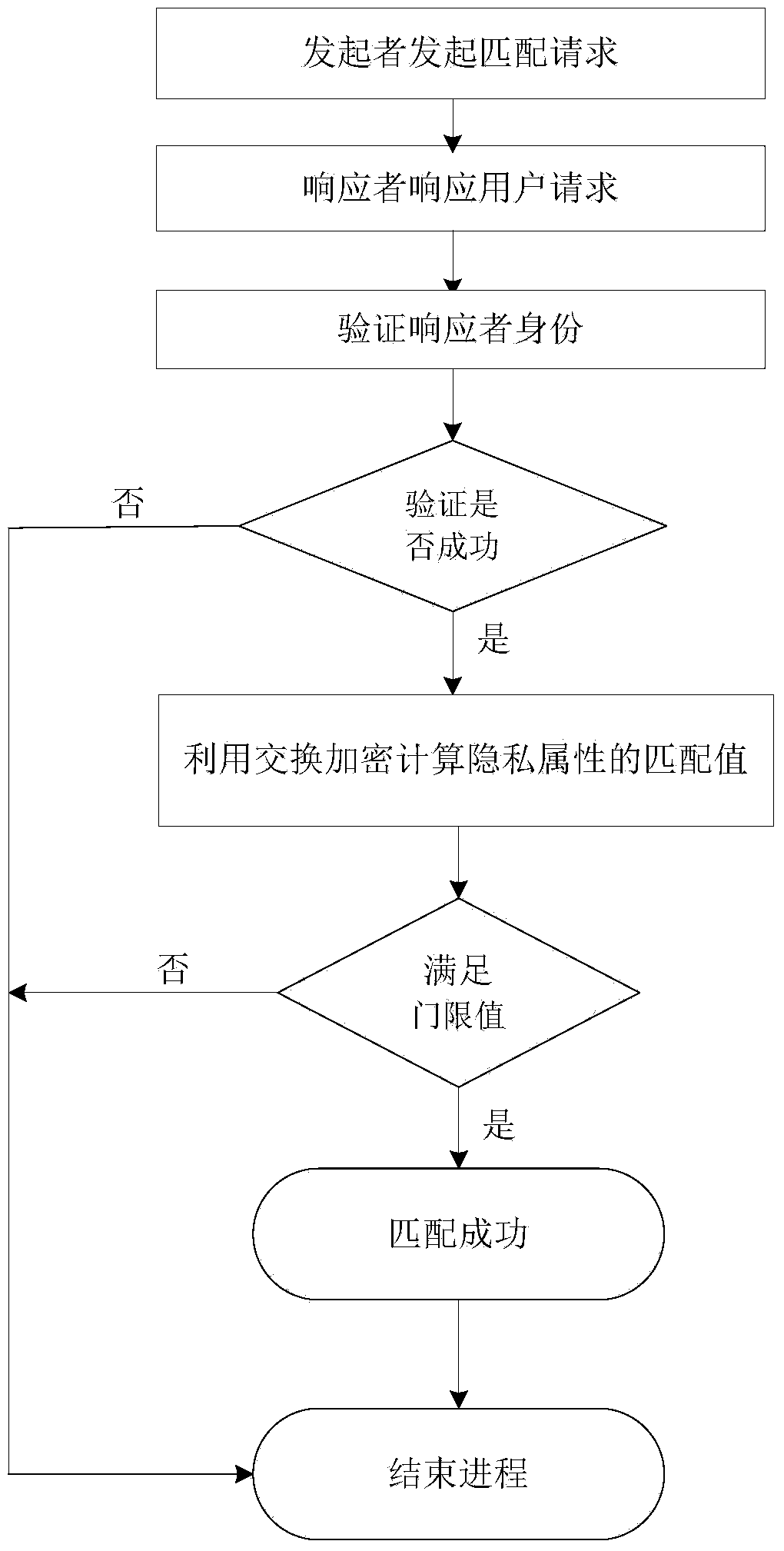
[0047] The realization of this embodiment includes the following two parts:
[0048] 1. Establish a communication system between the user and the identity authentication agency IDA.
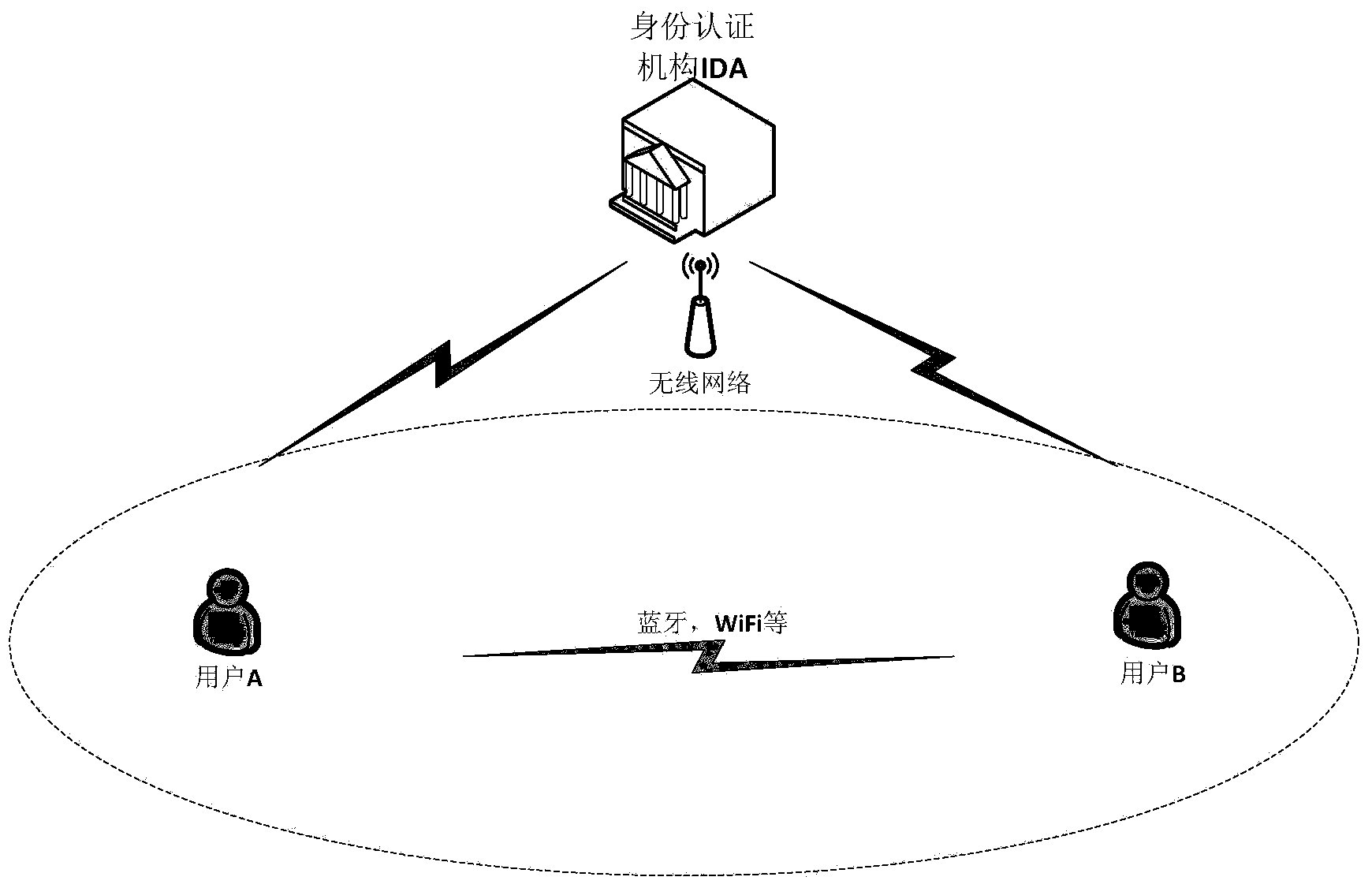
[0049] refer to figure 1 , the framework of the communication system established in this example is as follows figure 1 , which includes: user A and user B, and the identity authentication authority IDA. Among them, user A and user B communicate through Bluetooth or WiFi network, and the communication between the two users and the identity authentication agency IDA through 3G or 4G cellular network;
[0050] User A and user B enjoy privacy matching services through smart phones, tablet computers and other mobile devices, and the identity authentication agency IDA distributes dynamic identity IDs to user A and user B respectively A and ID B After that, user A and user B perform identity authentication and privacy matching with each other...
Embodiment 2
[0087] User A will match the similarity D(A,B) with the threshold τ A For comparison: if D(A,B)>τ A , user A terminates the matching process with user B, and refuses to be friends with user B; if D(A,B)≤τ A , then user A chooses user B to be his friend, and the two users can communicate formally, where, τ A Threshold value set for user A. Embodiment 2, multiple users perform privacy matching
[0088] The implementation of this embodiment includes two parts: establishing a communication system between multi-party users and identity authentication agencies and multi-party privacy matching. The implementation steps are as follows:
[0089] Step 1: Establish a communication system between multi-party users and the identity authentication agency IDA.
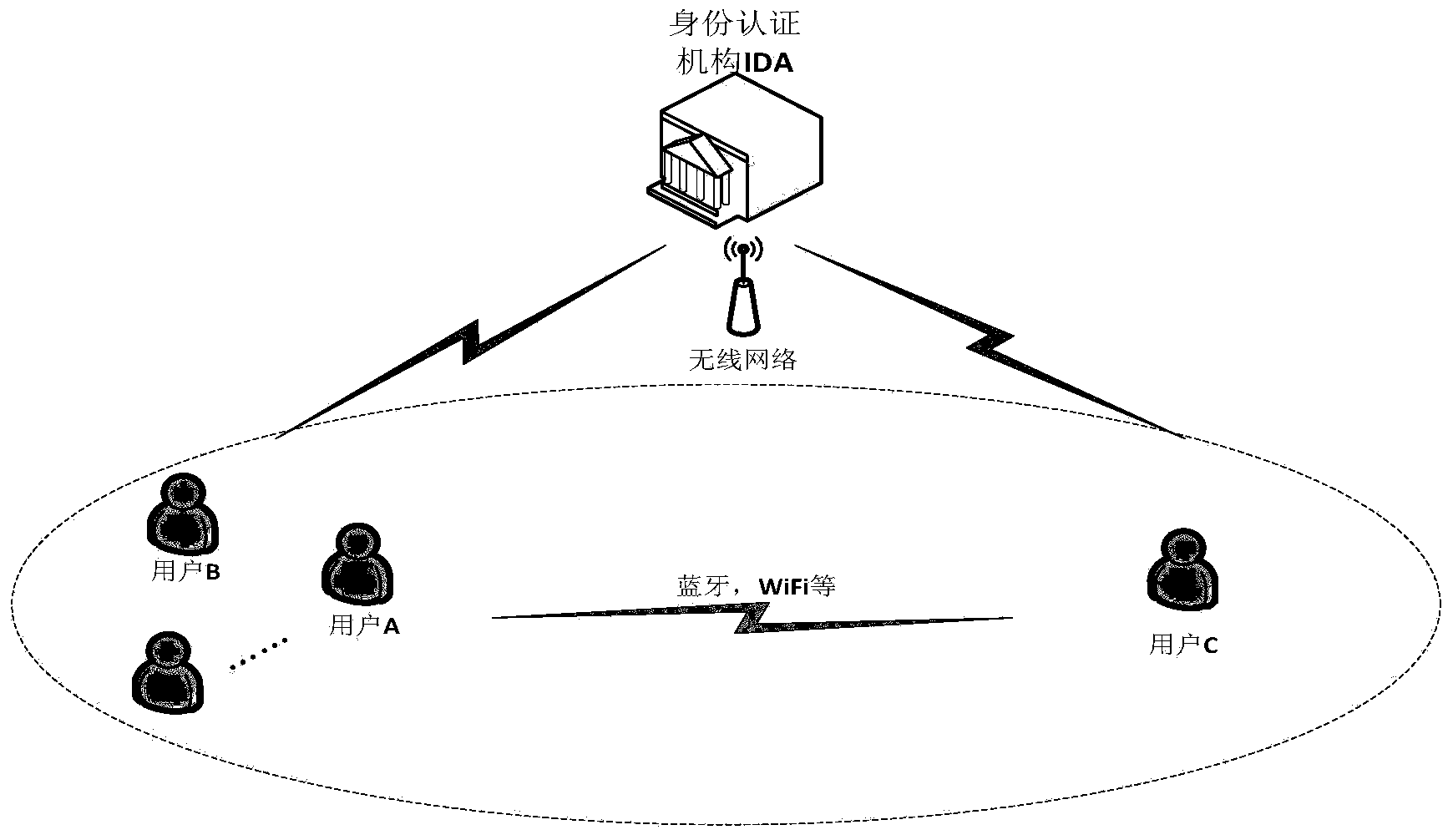
[0090] refer to image 3 , the framework of the communication system established in this example includes: user A, user C, other team members M t and Identity Authority IDA. in:
[0091] Communicate between users through Blu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com