Label verification method and terminal
A verification method and verification algorithm technology, applied in the electronic field, can solve problems such as inconvenient use and misjudgment, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
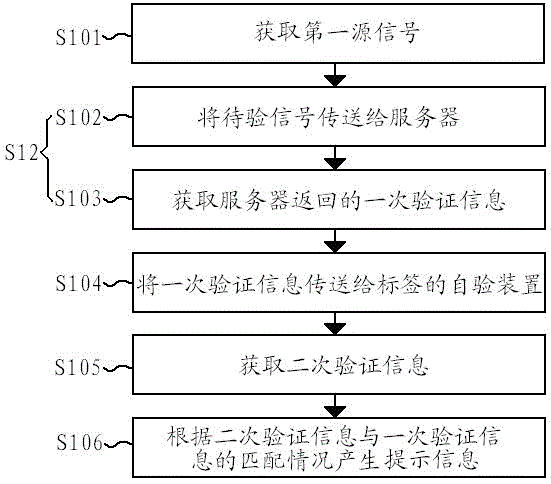
[0013] An implementation of the label verification method according to the present invention can refer to figure 1 , including the steps:
[0014] S101. Acquire a first source signal.
[0015] Wherein, the first source signal may come from electronic information, text information, audio information, video information or anti-counterfeiting marks recorded on the label. Electronic information may be information stored in a memory, electromagnetic waves of a specific frequency, or the like. Text information can be a character string or a sequence of numbers, etc. Anti-counterfeiting marks may include barcodes, two-dimensional codes or anti-counterfeiting patterns, etc. The anti-counterfeiting patterns can be, for example, laser anti-counterfeiting patterns, watermarks, plane or three-dimensional patterns printed with special ink, microtext and microdigits, and the like.
[0016] According to the type of information recorded on the label, the terminal can obtain the first sour...
Embodiment 2
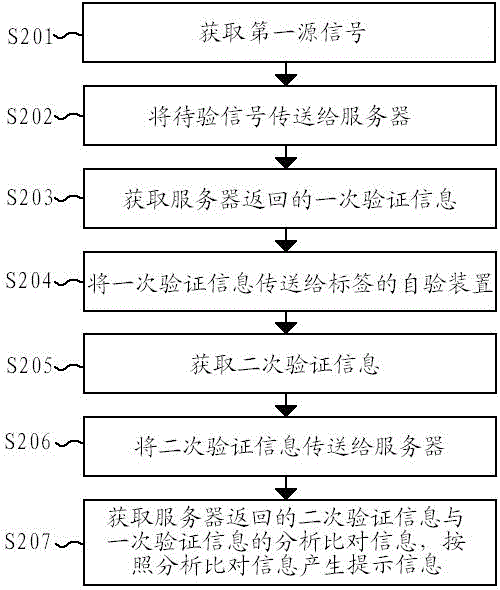
[0040] Another embodiment of the label verification method according to the present invention can refer to figure 2 , compared with embodiment 1, the main difference is that the server performs two analysis and comparison of verification information, and the method includes steps:
[0041] S201. Acquire a first source signal.
[0042] S202. Transmitting the pending signal to the server.
[0043] S203. Obtain one verification information returned by the server.
[0044] S204. Send the verification information once to the self-verification device of the label.
[0045] S205. Obtain secondary verification information.
[0046] The above steps S201-S205 can be performed with reference to the corresponding steps in S101-S105, and will not be repeated here.
[0047] S206. Send the secondary verification information to the server.
[0048] According to the type of the secondary verification information, the terminal can use various available transmission methods, for example, s...
Embodiment 3
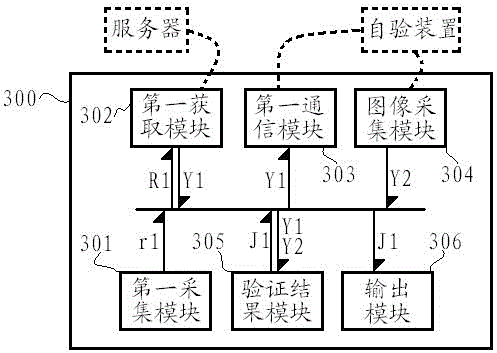
[0054] An embodiment of the terminal according to the present invention can refer to image 3 , the terminal 300 can be used to execute the label verification method in Embodiment 1, the terminal includes a first acquisition module 301, a first acquisition module 302, a first communication module 303, an image acquisition module 304, a verification result module 305, and an output module 306, in:
[0055] The first acquisition module 301 is configured to acquire the first source signal r1 from the tag.
[0056] The first obtaining module 302 is configured to obtain primary verification information based on the first source signal. In this embodiment, the first acquisition module is used to communicate with the server (shown by a dotted line in the figure) to acquire verification information once, specifically, to transmit the signal R1 to be verified to the server, and the signal to be verified is obtained by the first acquisition module 301 The first source signal r1 of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com