Virtual machine credibility guaranteeing method in cloud environment
A virtual machine and cloud environment technology, applied in the field of information security, can solve problems such as high pressure, reduce pressure, improve performance, and solve the problem of virtual machine migration.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
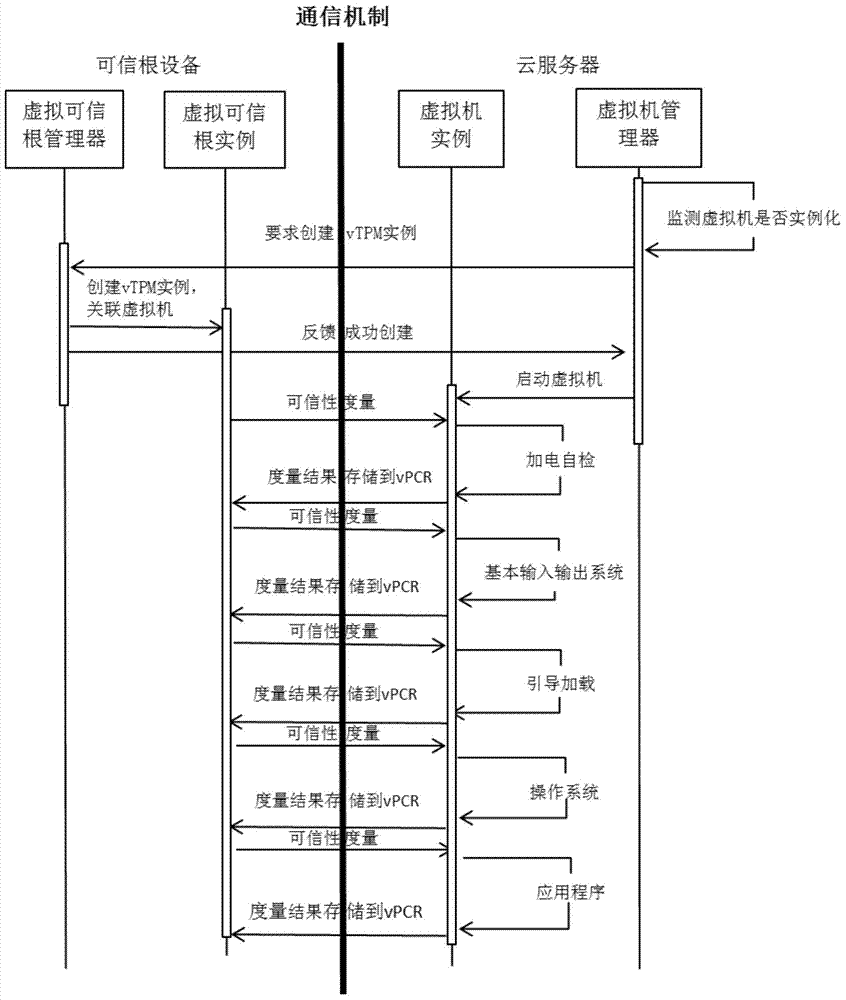
[0038]The main idea of the method for guaranteeing the trustworthiness of the virtual machine proposed by the present invention is to separate the virtual trusted root module in the cloud server from the virtual machine, set up a separate device, and use this device to complete the trustworthiness measurement of the virtual machine. The main content includes the communication mechanism between the root of trust device and the cloud server, and the method of virtual machine trustworthiness assurance—the establishment and transmission of the trust chain. The specific implementation will be explained according to the accompanying drawings:
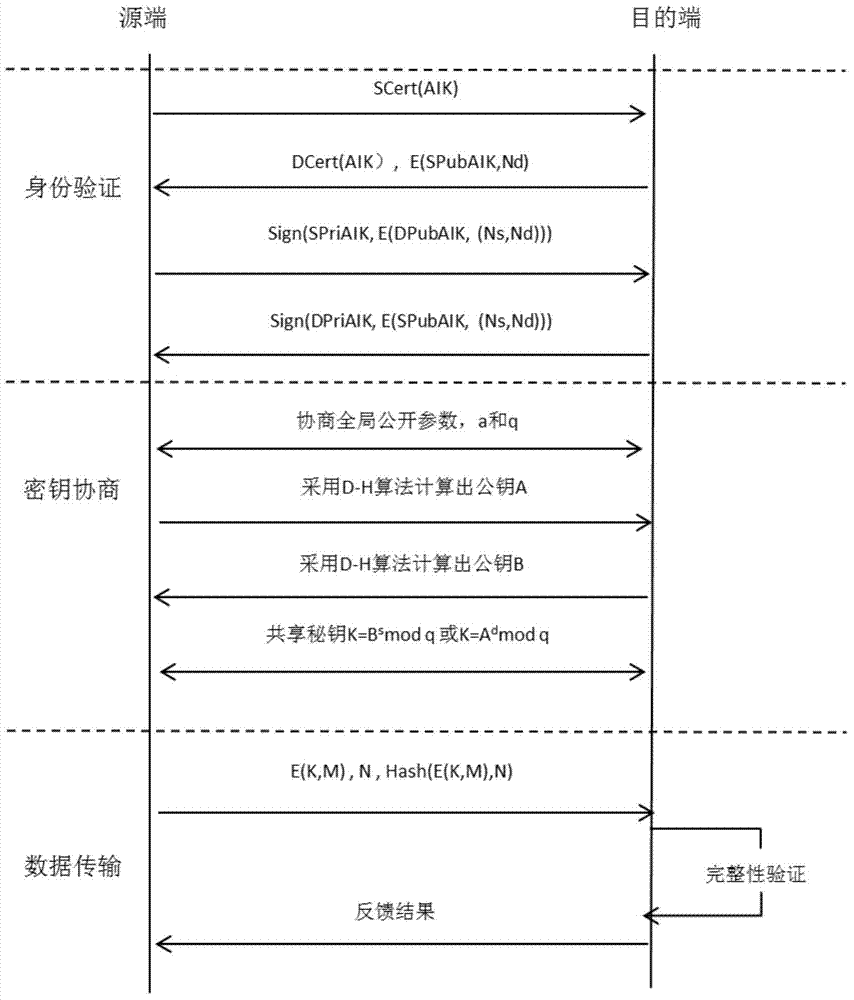
[0039] 1, figure 1 Introduce the communication mechanism between the root of trust device and the cloud server
[0040] Considering the safety problem of network transmission, the present invention designs a set of safe communication protocol. The communication protocol should guarantee the confidentiality, integrity and non-repudiation o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com