Improved RC5 encryption algorithm for secret key encryption
An encryption algorithm and key encryption technology, applied in the direction of encryption device with shift register/memory, etc., can solve the problem of large number of keys and low key confidentiality, and achieve less hardware resources, increase the difficulty of cracking, and eavesdropping. protective effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention is based on the following three number theory theorems.
[0017] Concept 1: It is a fact in number theory that it is easy to multiply two large prime numbers, but it is difficult to factor the resulting product.
[0018] Concept 2: Chinese Remainder Theorem: If the prime factors of N are P1*P2*...Pt, then the equation
[0019] wxya i =A i
[0020] There is only a unique solution X, X
[0021] Concept 3: In the set of integers Zn, if the following formula holds, the numbers a and b are additive inverses of each other and uniquely exist,
[0022] a+b≡0(modn)
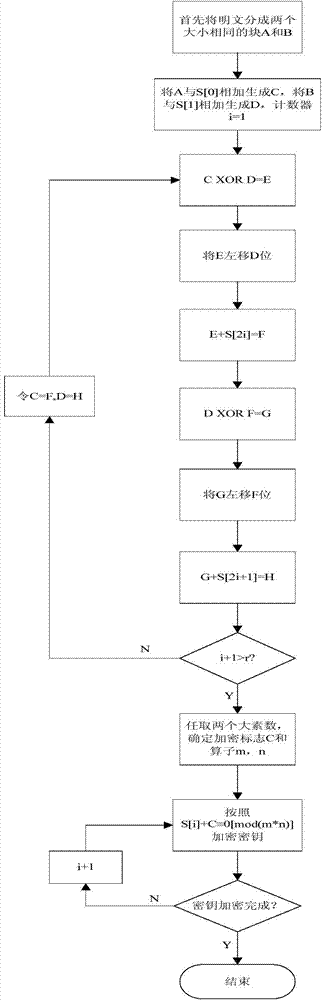
[0023] Such as figure 1 As shown, the binary number of the plaintext to be encrypted is divided into two parts A and B; S[] is the key array, and the elements in it are the subkeys for each encryption; add A and S[0] to get C , add B and S[1] to get D, and then start cyclic encryption, and the encryption times are r; the encryption process of each round is the sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com