Method for encrypting webmail information
An information encryption and mail technology, applied in the field of web mail information encryption, can solve the problems of low security, low public key security, low generality, etc. simple effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
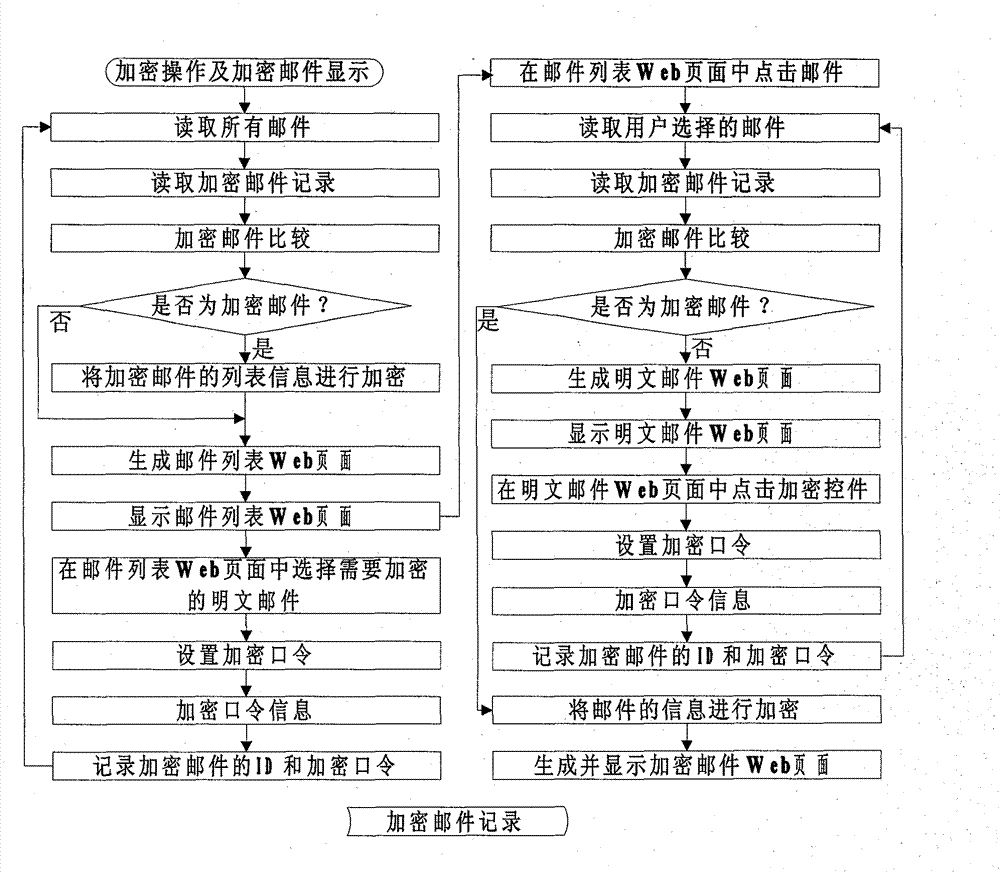
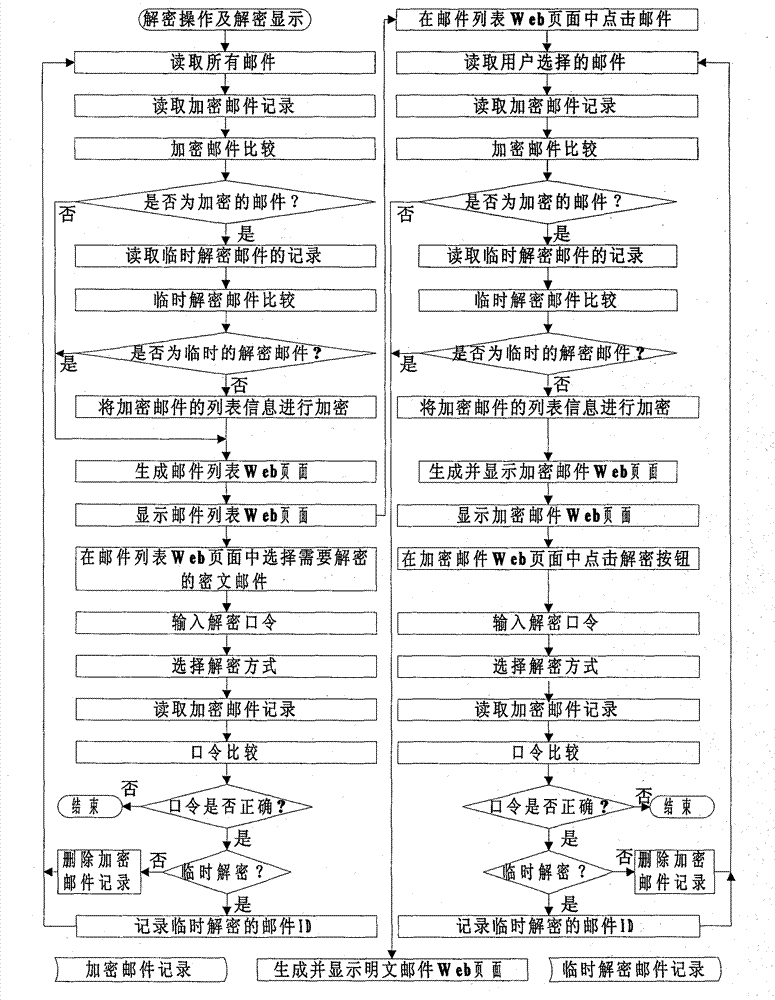
[0027] Embodiment: the present invention provides a kind of specific embodiment that the mail content of web mail (Webmail) is encrypted and protected, and it is used to solve the information confidentiality problem that the mail content of web mail is shown with clear text and occurs, and its method is specifically as follows:
[0028] 1. Encryption steps
[0029] from image 3 We can see that the encryption process of webmail and its display execution steps are as follows:
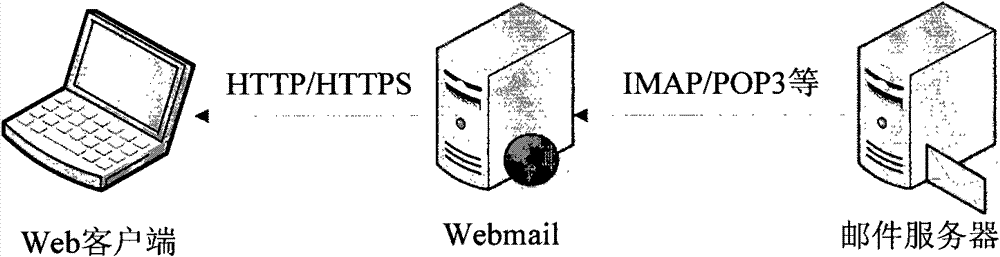
[0030] S1 After the user passes the user login authentication in the web mail system, first the web mail system (MUA) reads the mail information, that is, from the mail server through the mail communication protocol, such as POP3, IMAP and other communication protocols, but not limited to this, to obtain the mail All mails of users in the server, where the mail server is any third-party independent mail server.
[0031] S2 reads the local encrypted mail record, that is, reads the characteristic value (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com