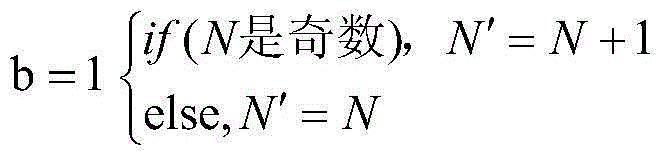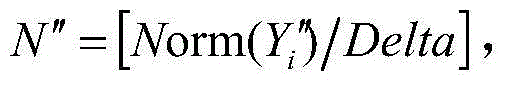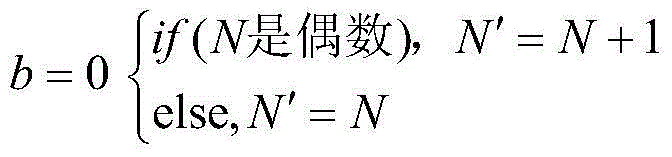DWT-SVD robust blind watermark method based on Zernike moments
A blind watermarking and robust technology, applied in the field of information security, can solve the problem of weak ability to resist geometric attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below in conjunction with embodiment the present invention is further described.
[0026] A DWT-SVD robust blind watermarking method based on Zernike moments includes watermark embedding and watermark extraction.
[0027] The specific implementation steps of the first part of watermark embedding are as follows:
[0028] Step1: Select Lena with 512×512 pixels as the original carrier image, perform one-level DWT transformation on the watermark embedding area X of the carrier image, and divide the low-frequency sub-band LL into a 4×4 matrix, A i Represents the i-th matrix block, and performs SVD decomposition on each block matrix Order Y i =[λ 1 ,λ 2 ,...λ r ],λ j Represents the singular value matrix S i The jth non-zero singular value of , where j=1,2,...r, r is the matrix A i The rank of i=1,2,...32×32.
[0029] Step2: Select the 32×32 pixel binary image "information security" as the watermark, denote it as W, and perform chaotic encryption on the watermark to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com