Neural Network Model Encryption Protection System and Method Involving Specified Frequency Band Encryption
A neural network model and protection system technology, which is applied in the field of neural network model encryption protection system to achieve the effects of improving security, improving concealment and anti-attack, and protecting rights and interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
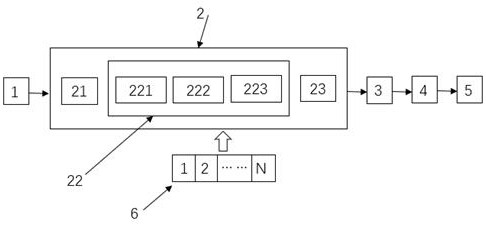
[0064] A system structure diagram of a neural network model encryption protection system 100 involving encryption of a specified frequency band is shown in the appendix of the description. figure 1 , for the encryption principle of the encryption module 2 of the encryption protection system 100, please refer to the appendix of the description. figure 2 , the encryption protection system 100 includes a data input module 1 , an encryption module 2 , an encrypted data input module 3 , an artificial neural network model module 4 and a data output module 5 . The data input module 1 is connected with the signal of the encryption module 2, the encryption module 2 is connected with the signal of the encrypted data input module 3, the encrypted data input module 3 is connected with the signal of the artificial neural network model module 4, and the artificial neural network model module 4 is connected with the signal of the data output module 5. connected.
[0065] Specifically, the ...
Embodiment 2
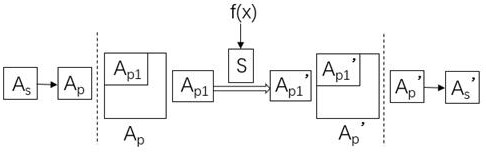
[0083] A method flow chart of a neural network model encryption protection method involving encryption of a specified frequency band is shown in the appendix of the specification. Figure 4 , the method includes the following steps:
[0084] Step S1. Provide original input data A s ;
[0085] Step S2. For the original input data A s Perform encryption processing to generate encrypted input data A s ’ ;
[0086] Step S3. Receive encrypted input data A s ’ , and input it into the artificial neural network model;
[0087] Step S4. The artificial neural network model encrypts the input data A s ’ carry out the calculation and obtain the calculation result;
[0088] Step S5. Output the calculation result.
[0089] Further, the step S2 includes the following steps:
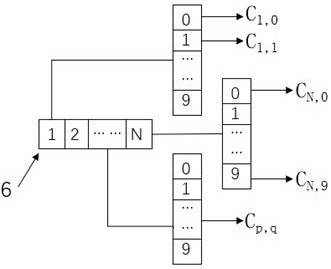
[0090] Step S21. The original input data A s Convert to a two-dimensional structure, and perform the structure-transformed original input data A s Domain transformation is performed to convert the original...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com