Access authentication method of terminals and access gateway
An access gateway and access authentication technology, applied in the field of communication, can solve the problems of high power consumption, complicated manual input, inoperability, etc., and achieve the effect of reducing power consumption, reducing complexity, and simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
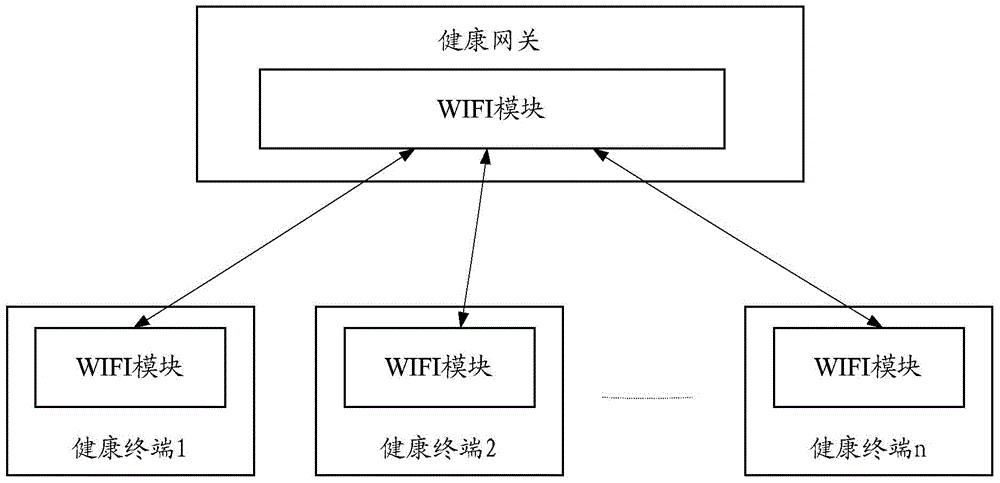
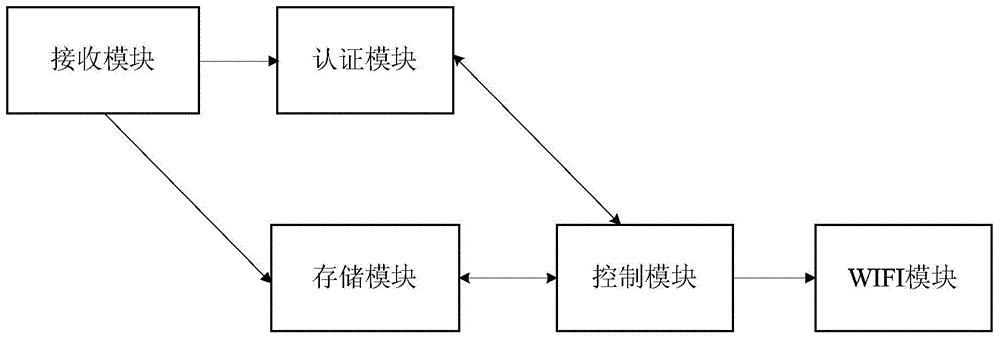
[0038] like figure 2 As shown, this embodiment provides an access gateway, including:
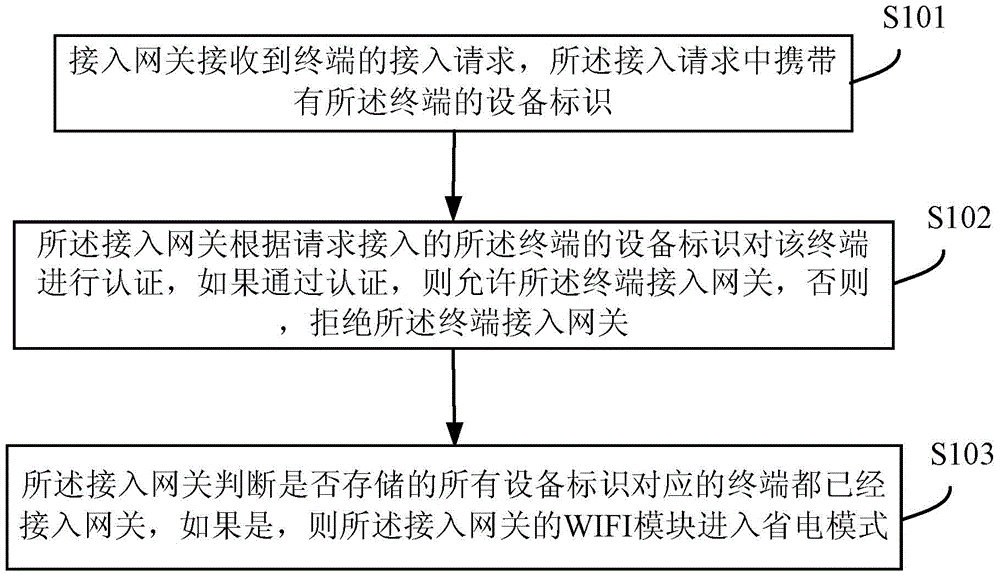
[0039] A receiving module, configured to receive an access request from a terminal, where the access request carries a device identifier of the terminal;
[0040] Wherein, in this embodiment, when the terminal leaves the factory, the device identification, such as IMEI (International Mobile Equipment Identification Number, International Mobile Equipment Identification Number), generates a two-dimensional code or marks it on the device; the terminal's device identification is used as the authentication mark .
[0041] The authentication module is configured to authenticate the terminal requesting access according to the device identifier of the terminal, and if the authentication is passed, allow the terminal to access the gateway; otherwise, deny the terminal to access the gateway.
[0042] The access gateway also includes a storage module connected to the receiving module and the authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com