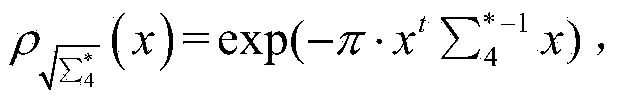Signature verification method based on Gaussian sampling
A technology for signature verification and signed message, applied in the field of information security, which can solve the problems of low execution efficiency, short running time and occupying storage space, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings.
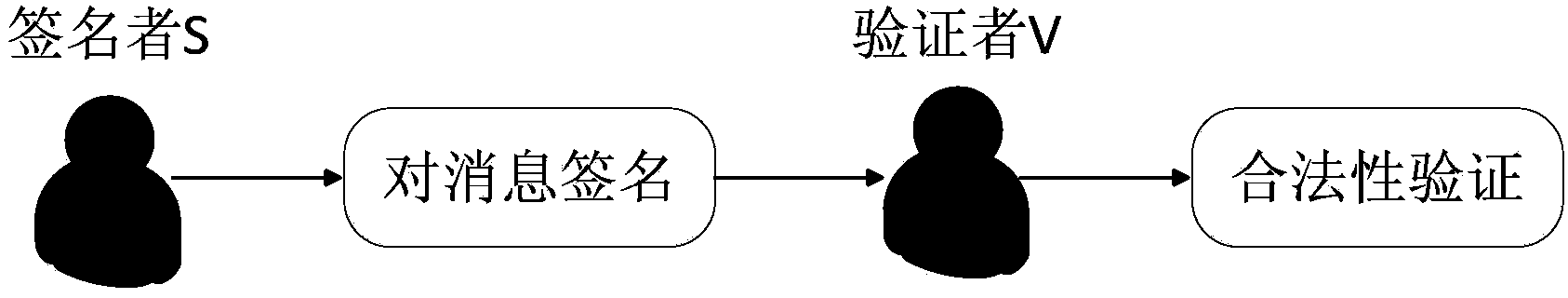
[0029] like figure 1 As shown, the signer S in the scenario signs the message M that needs to be signed, and the verifier V verifies the validity of the signature.
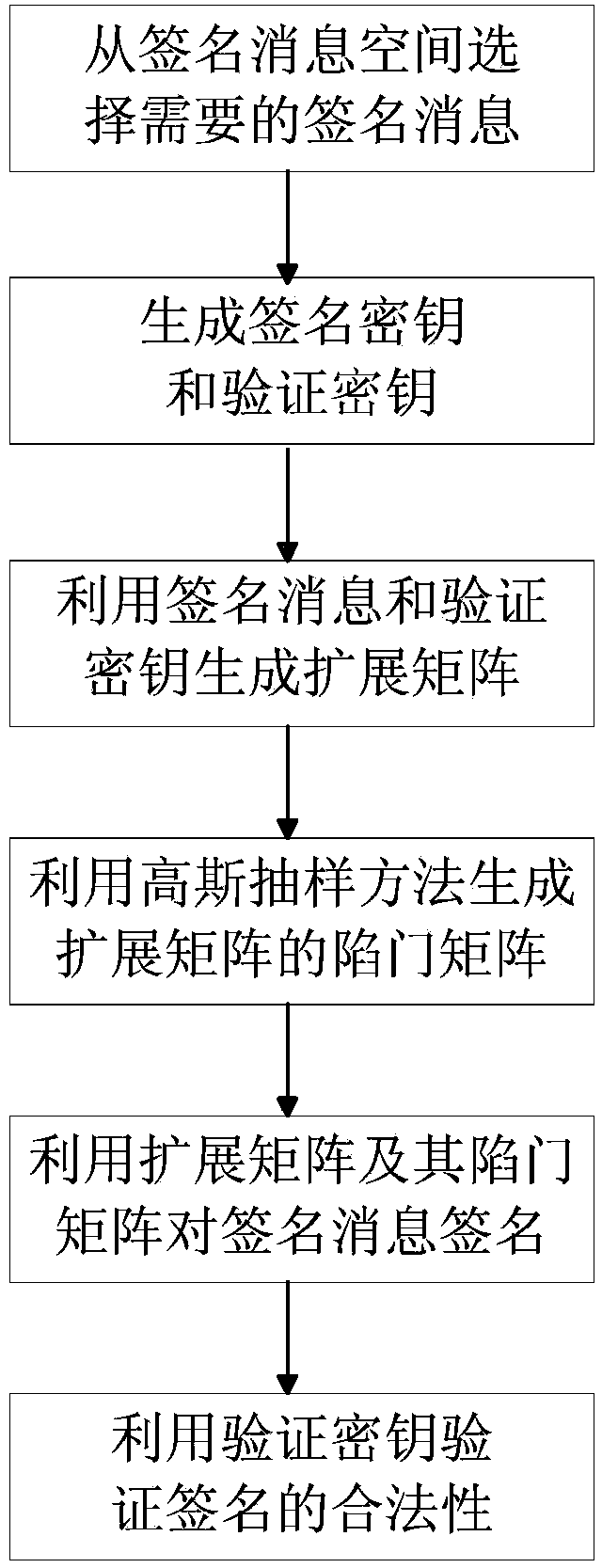
[0030] refer to figure 2 , the invention is figure 1 The steps to sign in the scene are as follows:
[0031] Step 1, the signer S selects the parameters and uses the key generation algorithm to generate the signature key sk and the verification key vk.
[0032] (1a) From the signature message space {0,1} l Select the required signature message M, where l is the length of the signature message, satisfying the inequality l≤(p-1)? n, where p is the smallest prime factor of q, q is a modulus and not a power of 2, and n is a security parameter;
[0033] (1b) Select generator matrix make each element subject to Uniform distribution on , choose the trapdoor matrix Make each element of the trapdoor ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com