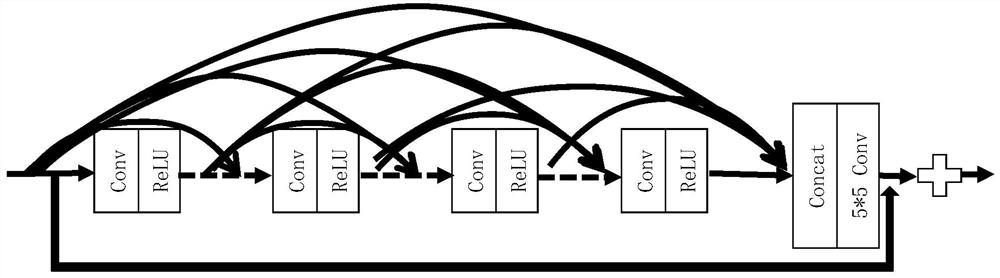
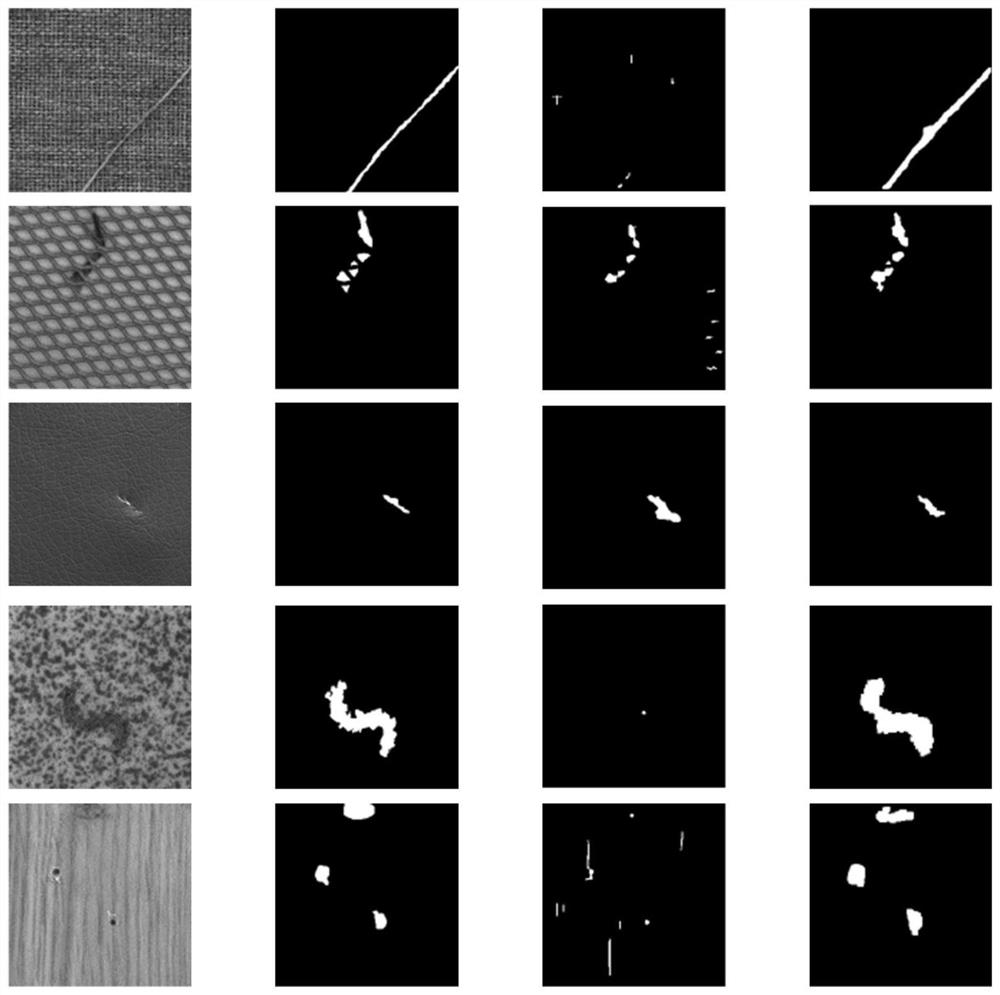
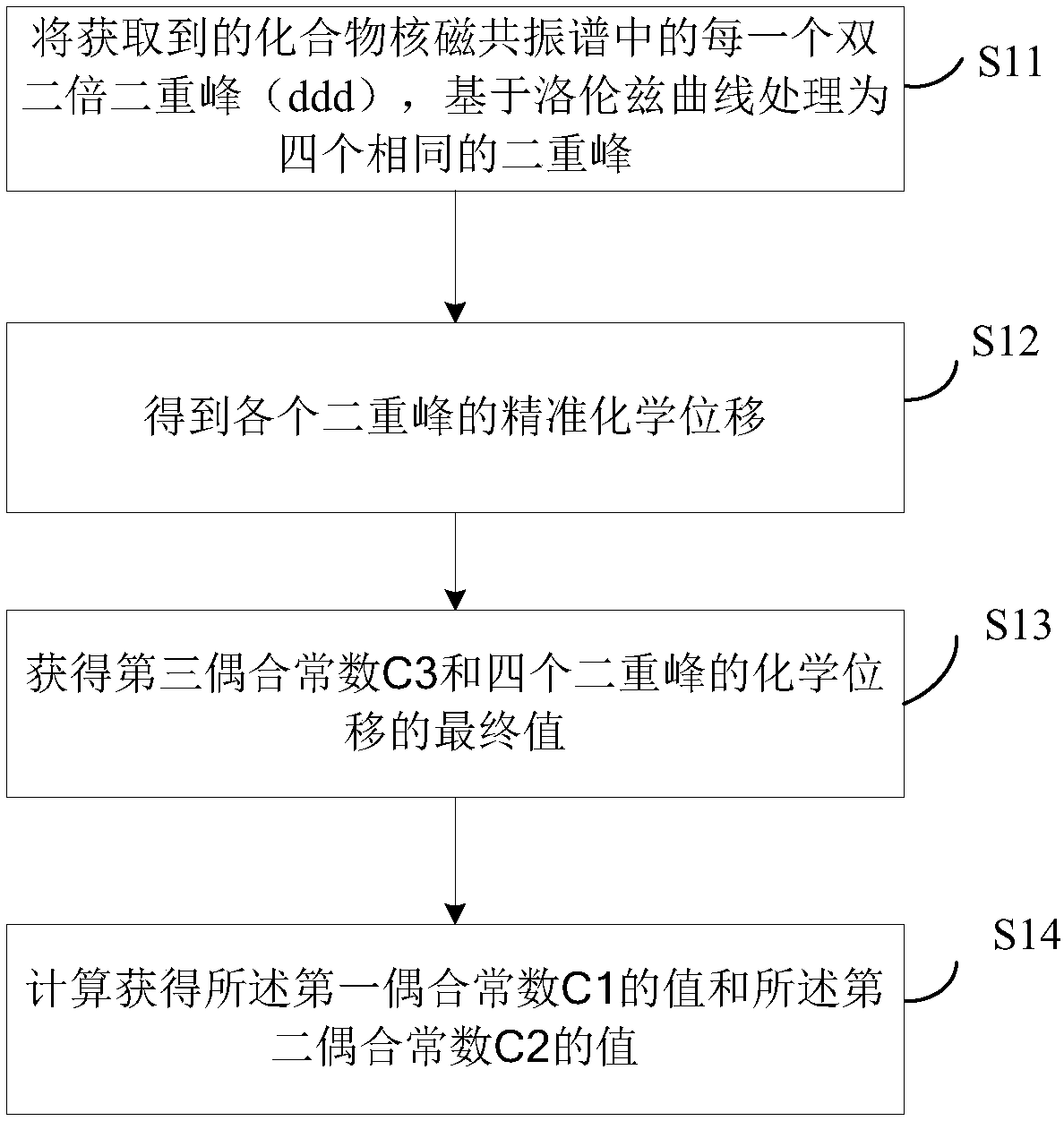
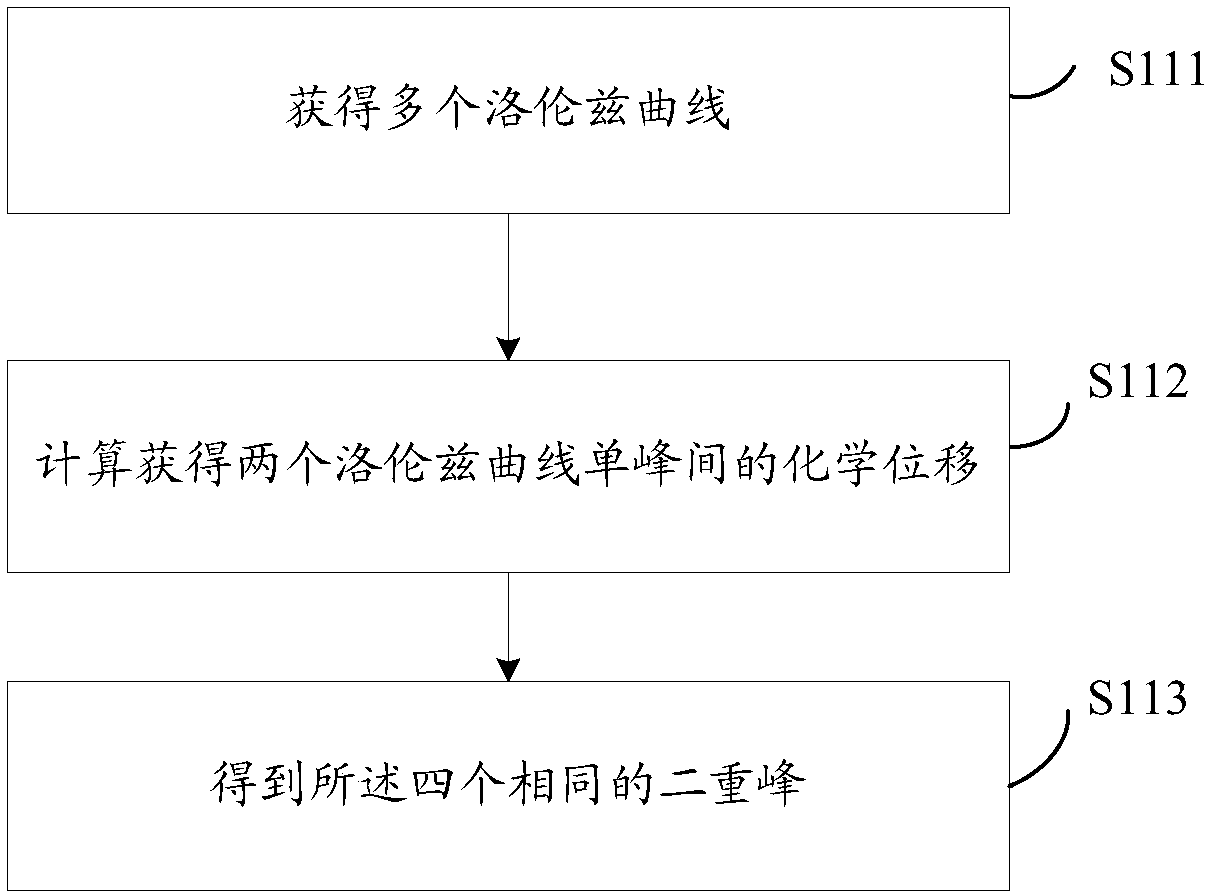
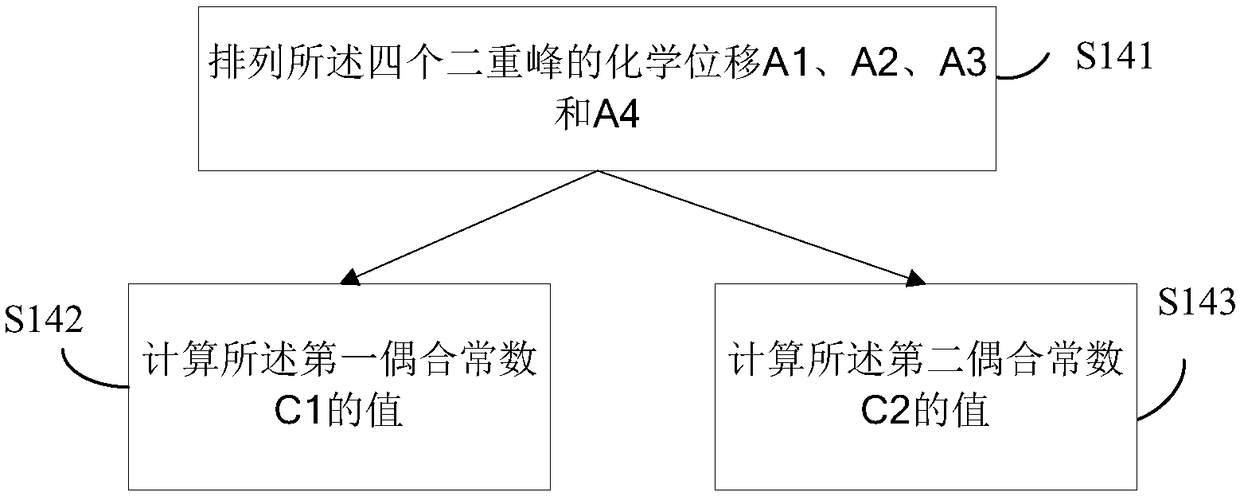
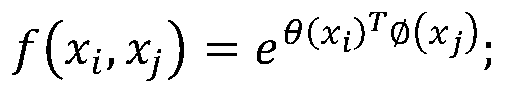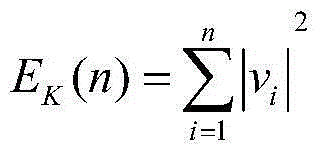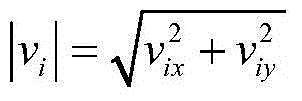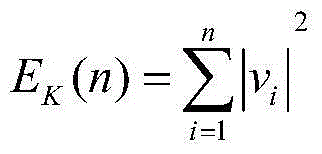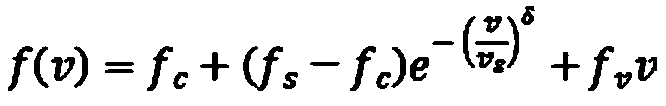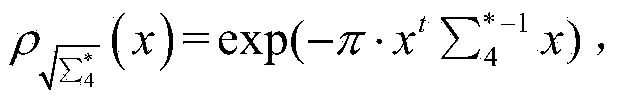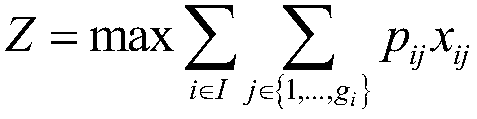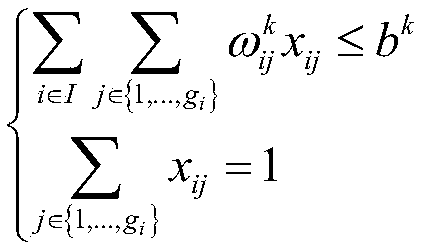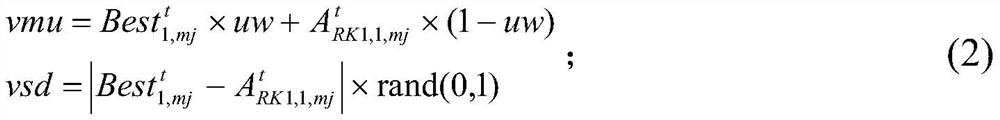Patents
Literature
47 results about "Gaussian sampling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
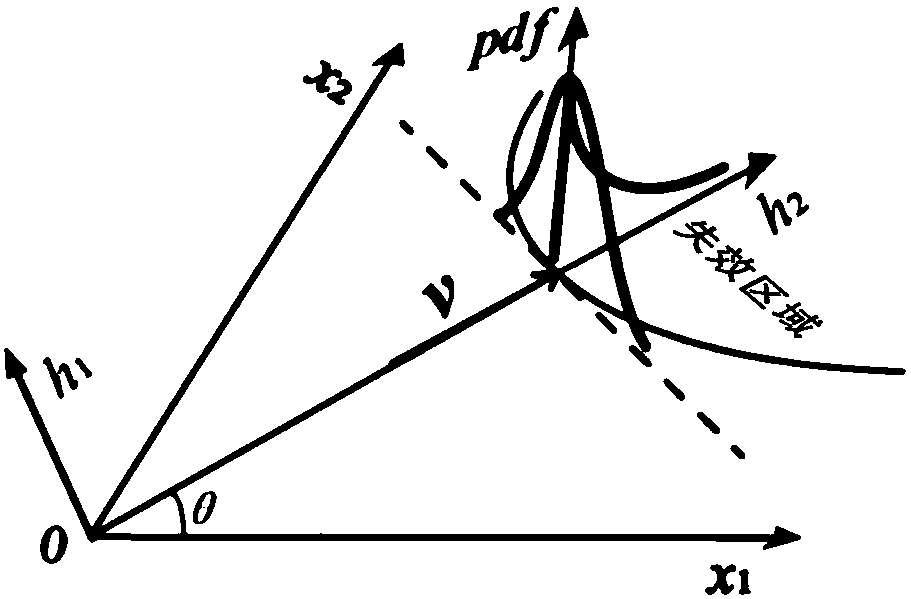
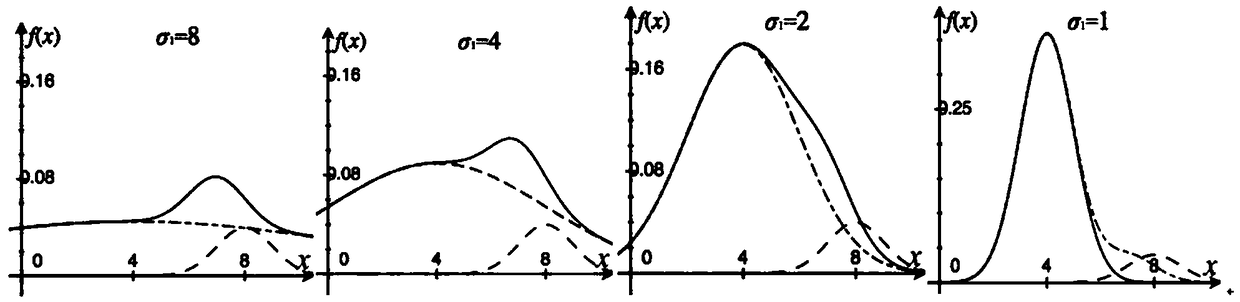
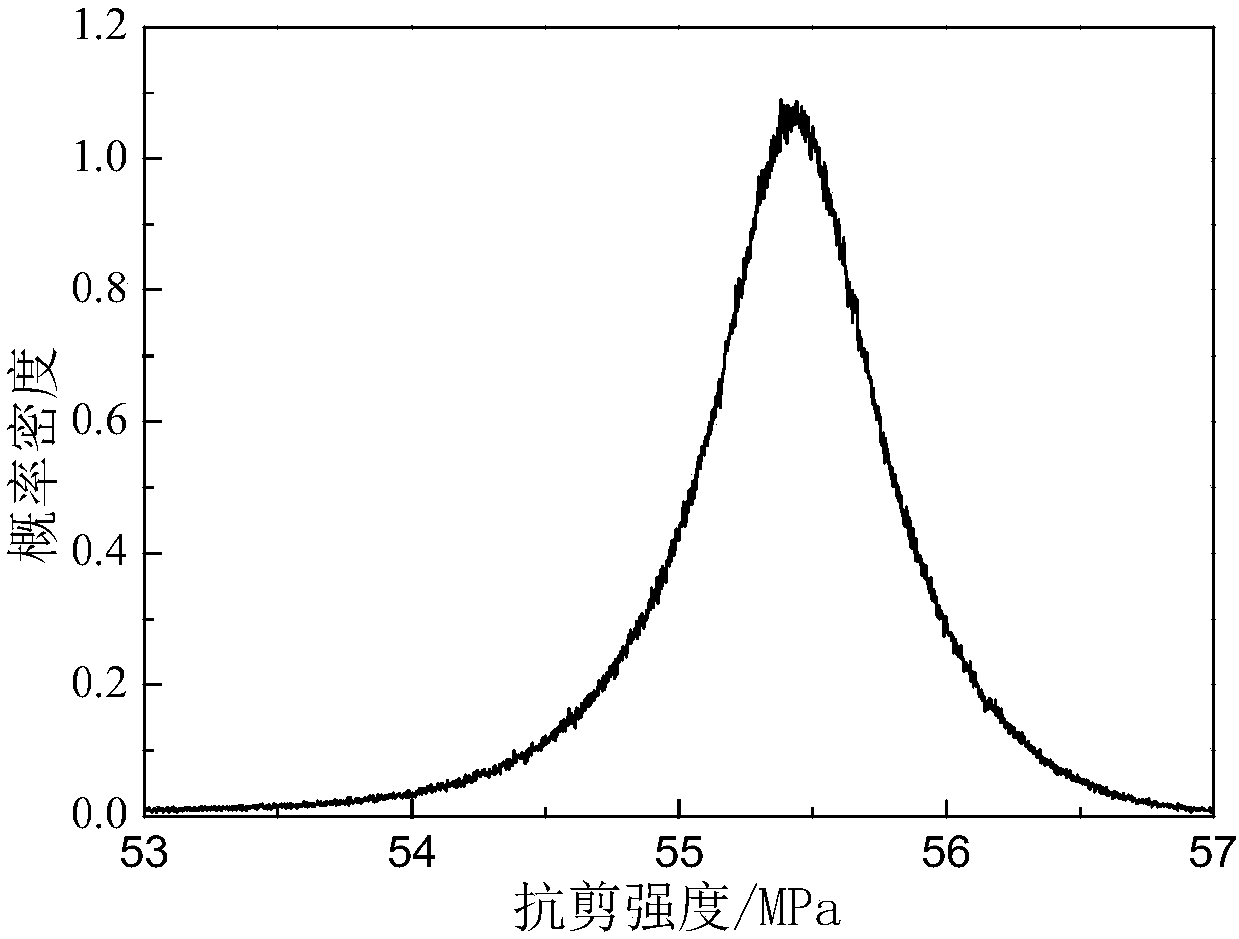
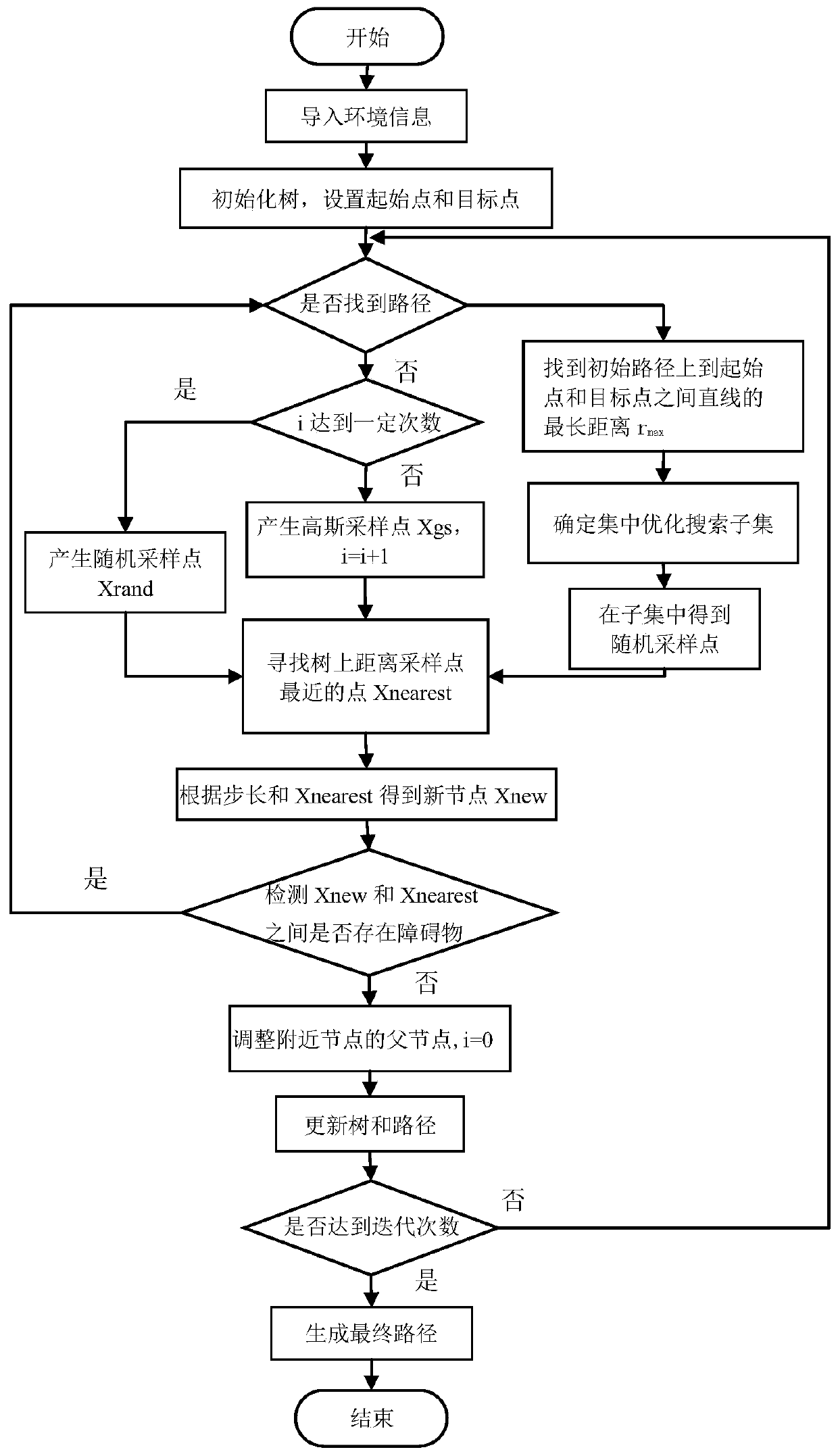
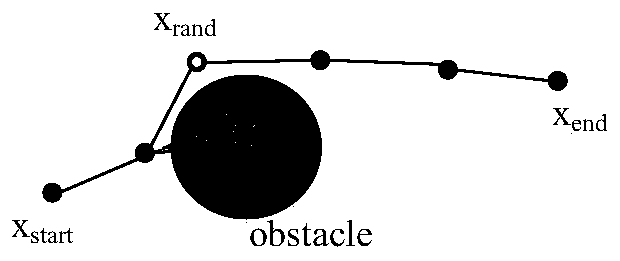
The Gaussian sampling strategy follows some of the same motivation for sampling on the boundary. In this case, the goal is to obtain points near by using a Gaussian distribution that biases the samples to be closer to , but the bias is gentler, as prescribed by the variance parameter of the Gaussian.
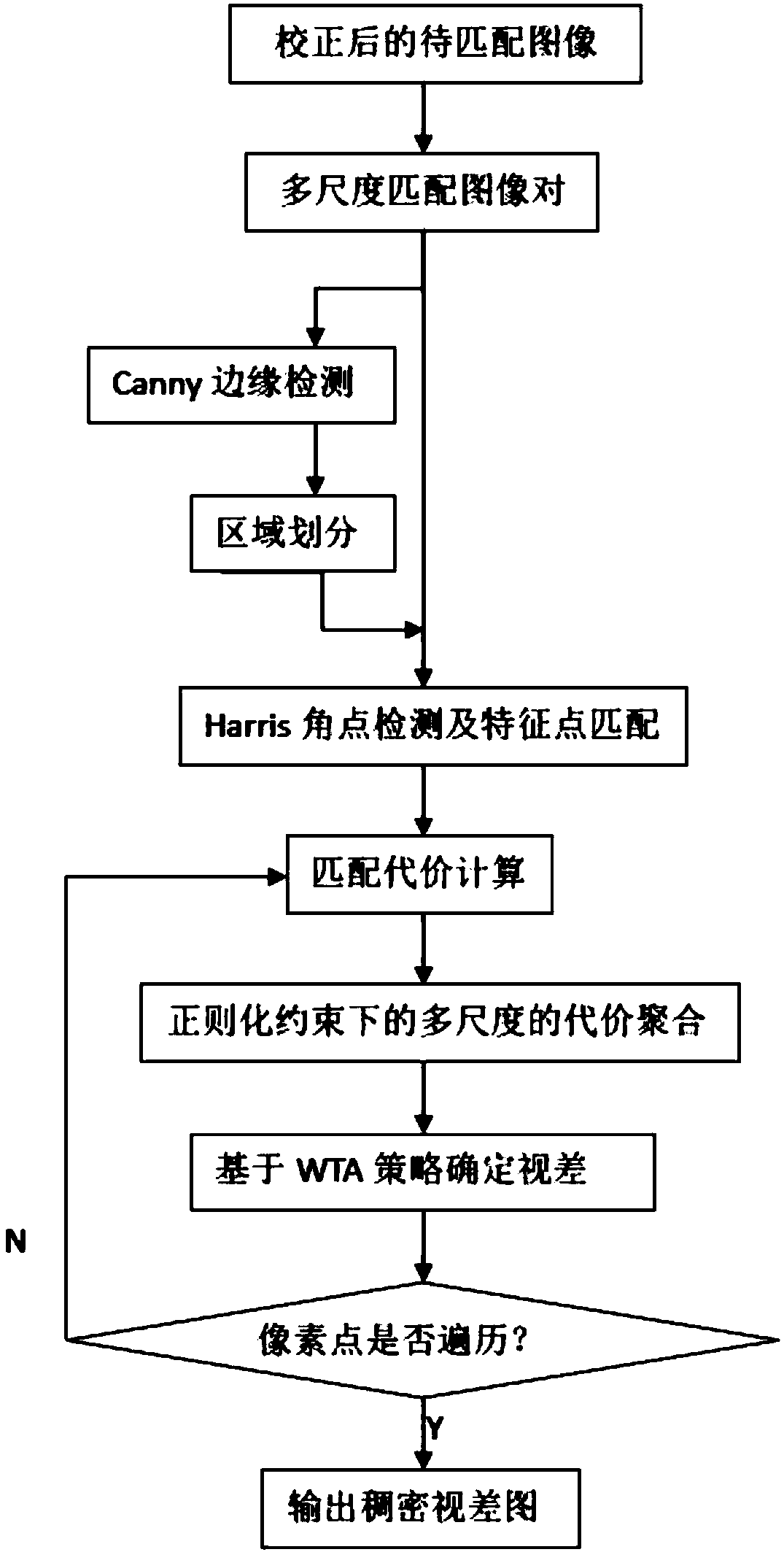
Binocular stereo matching method based on edge information
PendingCN111833393AHigh precisionExact disparity mapImage enhancementImage analysisParallaxColor transformation
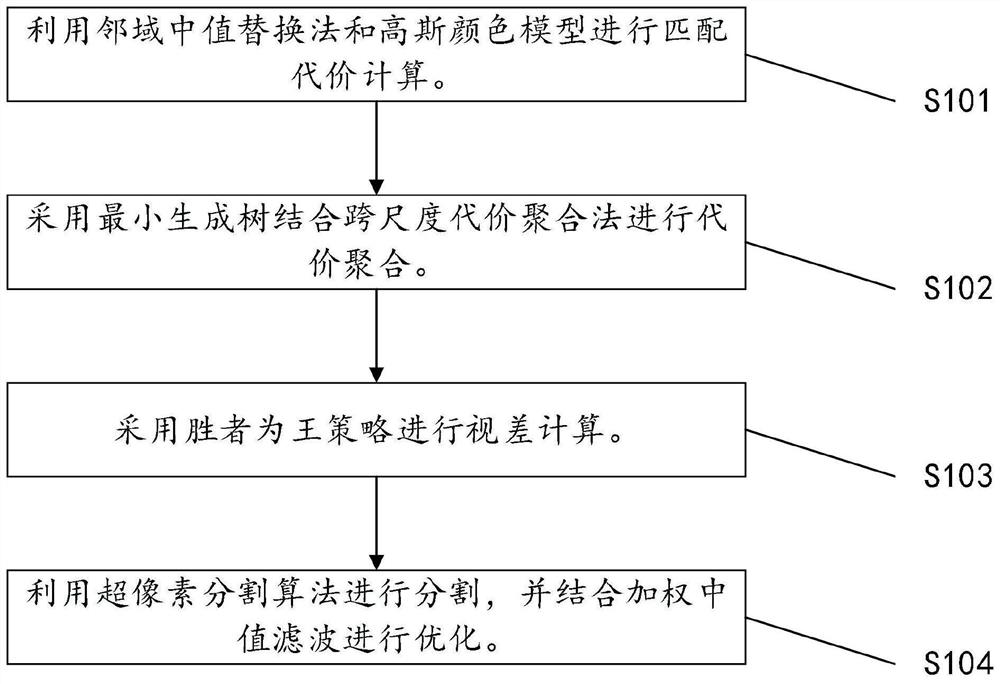
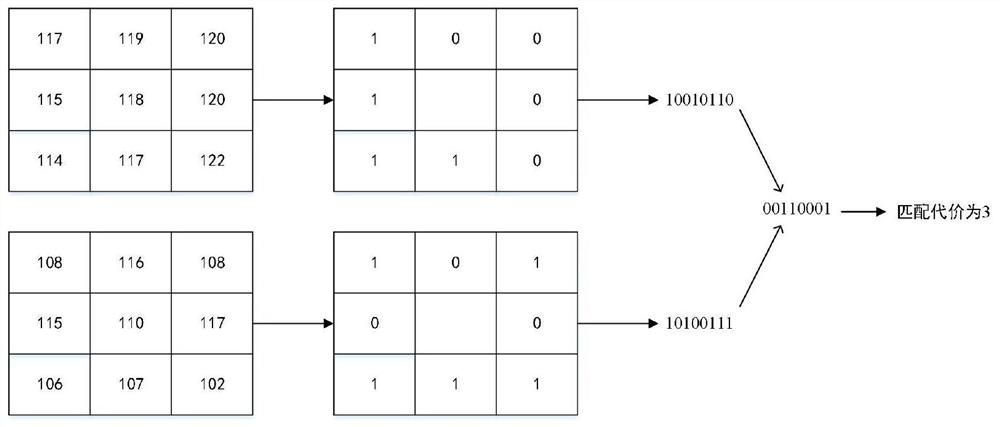
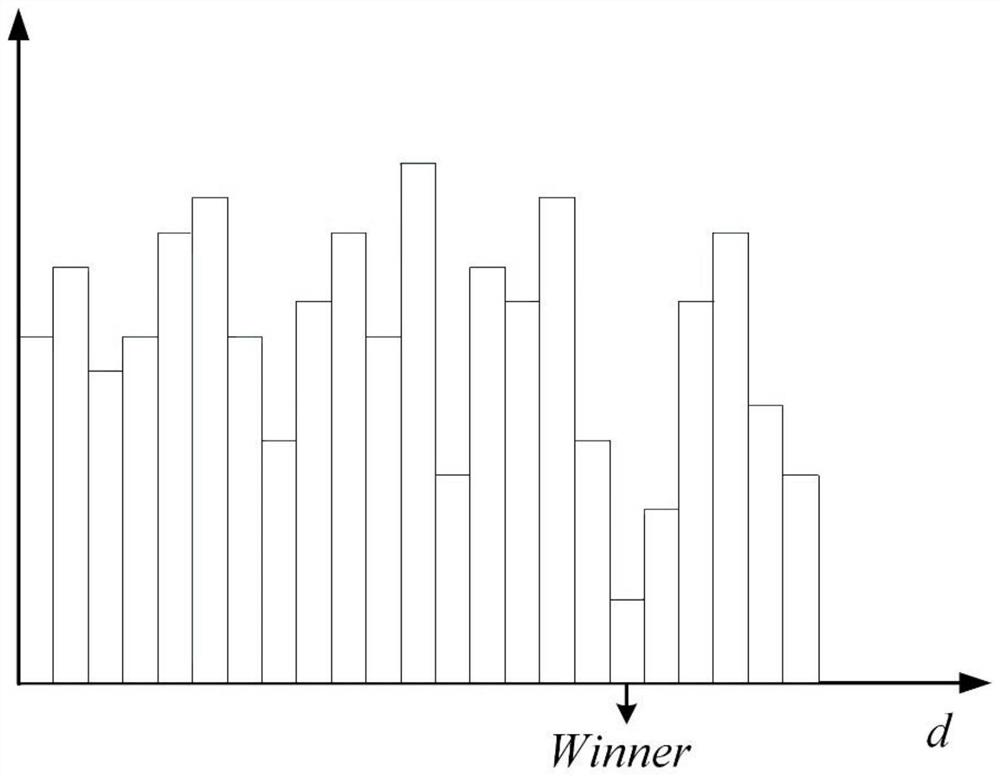
The invention discloses a binocular stereo matching method based on edge information. Firstly, performing color conversion on a left image and a right image acquired by Gaussian sampling through a Gaussian color model, introducing gradient information, using a neighborhood median as a threshold to replace a central pixel of a window, and counting the number of different corresponding bits in a Census transform value by using a Hamming distance so as to obtain a matching cost amount; secondly, converting the acquired image into an undirected graph, performing gradient operation by using a weighting function, constructing a minimum spanning tree, and performing cost aggregation by combining a cross-scale cost aggregation method to obtain a parallax value; generating a disparity map accordingto the obtained disparity value by using a winner-king strategy; and finally, carrying out region division on the pixel points by utilizing a super-pixel segmentation algorithm, and carrying out optimization processing on the disparity map by combining weighted median filtering, so that disparity information with relatively high precision can be obtained, and particularly, a relatively accurate disparity map can be obtained in an occlusion region and an edge information discontinuous region.
Owner:GUILIN UNIV OF ELECTRONIC TECH
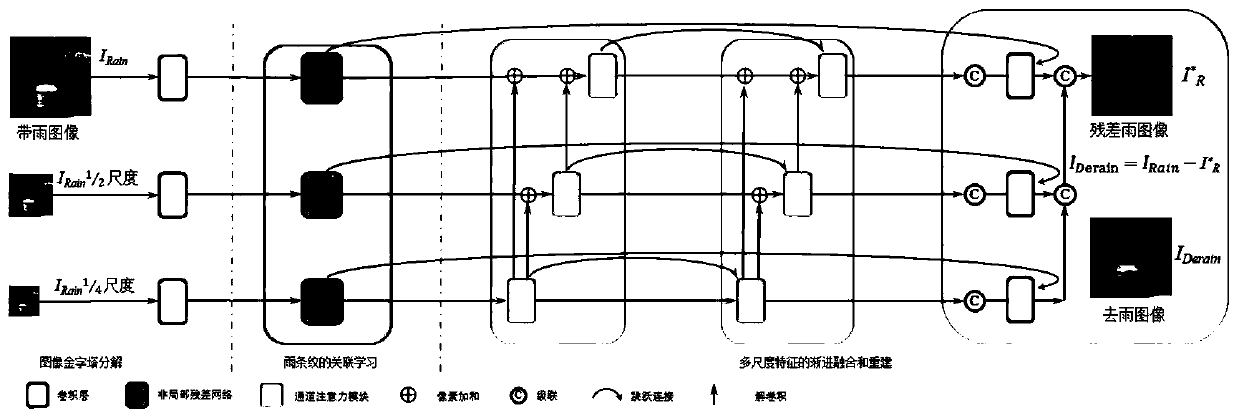
Image rain removing method based on multi-scale progressive fusion
ActiveCN111340738AImplement extractionAchieve integrationImage enhancementImage analysisPattern recognitionDecomposition
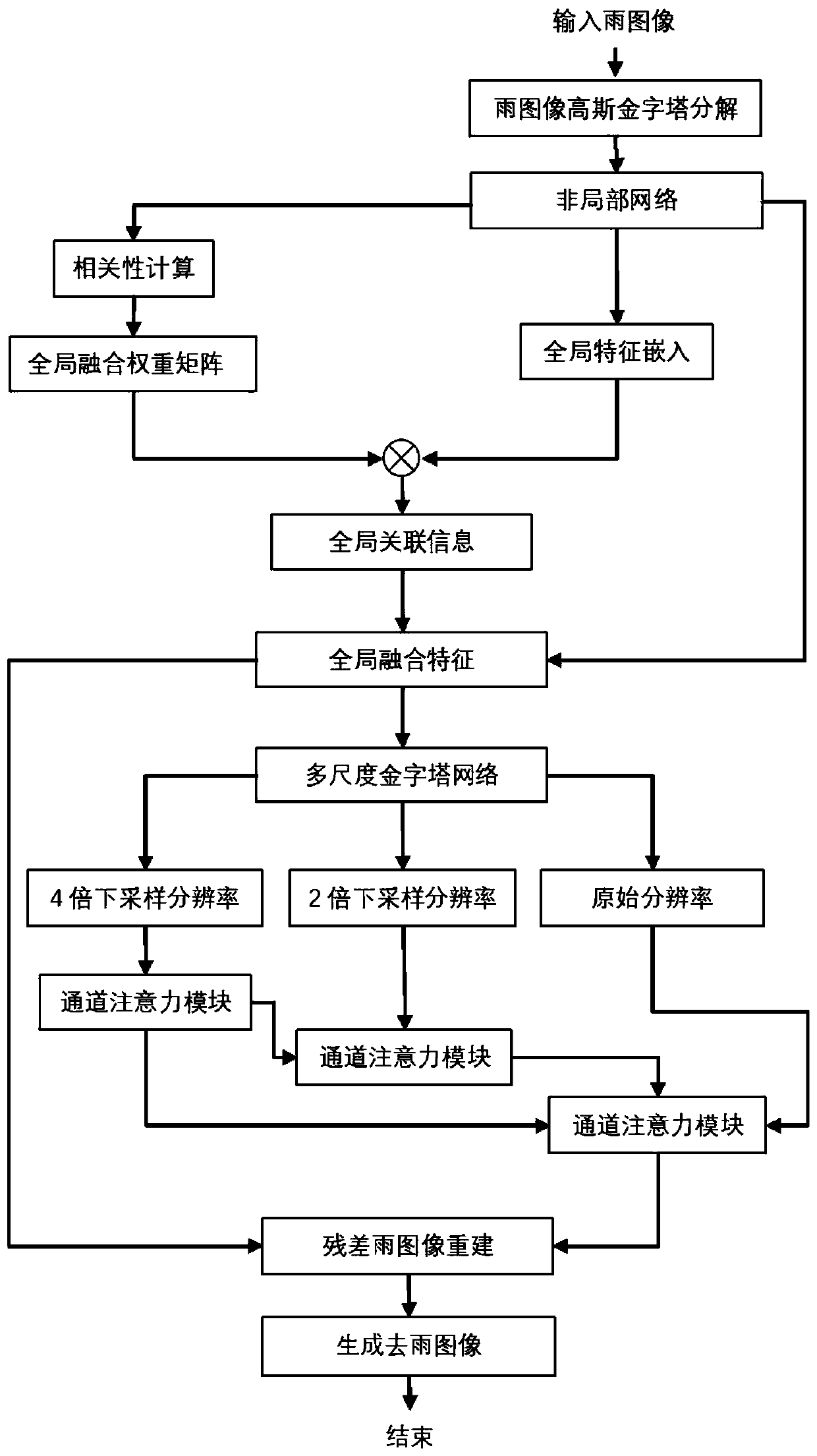
The invention discloses an image rain removal method based on multi-scale progressive fusion. The method comprises pyramid decomposition of a rain image, relevance learning of rain stripes, and progressive fusion and reconstruction of multi-scale features. In the pyramid decomposition process of the rain image, Gaussian sampling operators of different scales are utilized to perform sampling decomposition on the original rain image; in the correlation learning process of the rain stripes, learning global texture feature correlation is learned by using a non-local network; in the progressive fusion and reconstruction process of the multi-scale features; the multi-scale pyramid network is used for processing the features of the corresponding scales, and meanwhile, the multi-scale rain stripeinformation is gradually fused to assist the feature expression of the highest pyramid layer, so that the multi-scale fusion of the rain stripe information is realized, the residual rain image is reconstructed, and the residual image is subtracted from the rain image to obtain the rain-free image. According to the method, tThe correlation between the rain stripes in the same-scale image and the rain stripes in different-scale images is effectively utilized, the rain stripes are more accurately modeled, and a better rain removal effect is achieved.
Owner:WUHAN UNIV
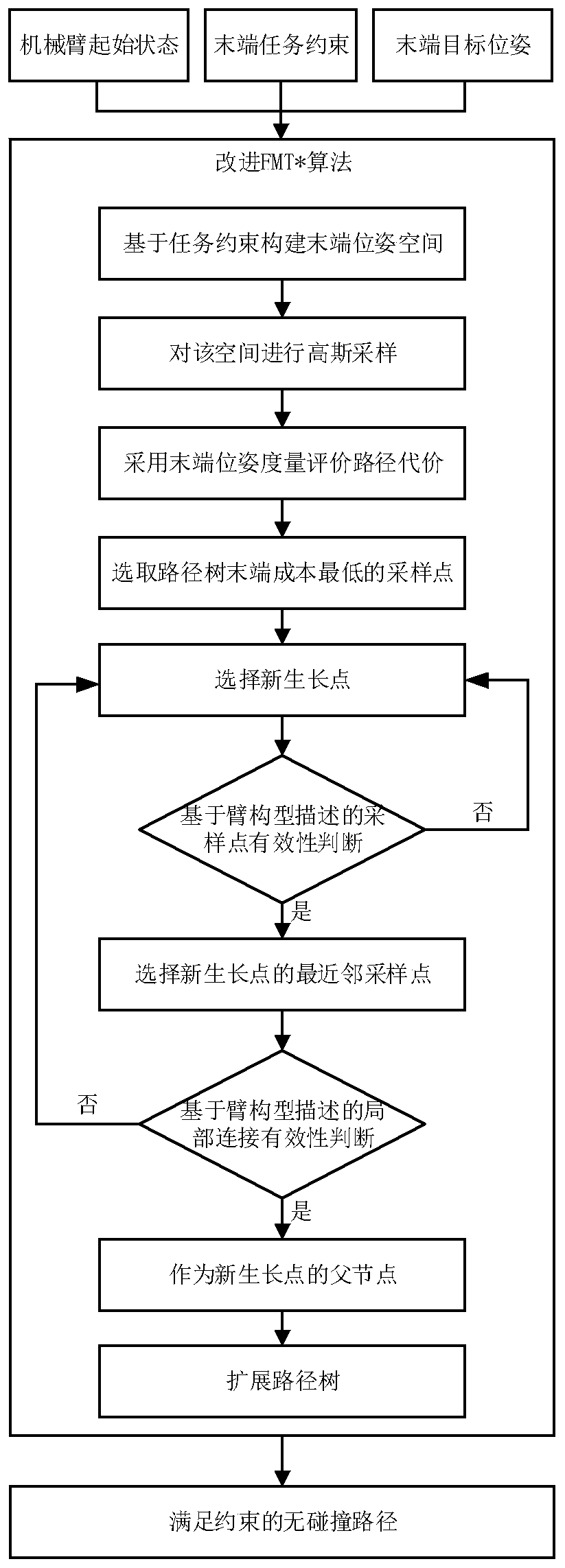
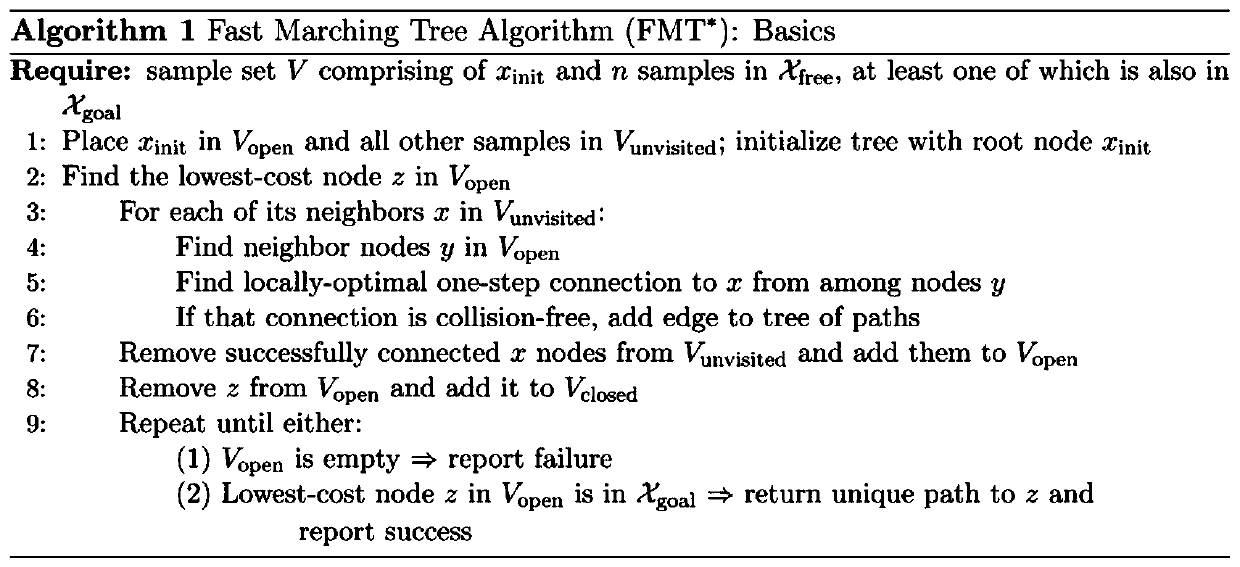
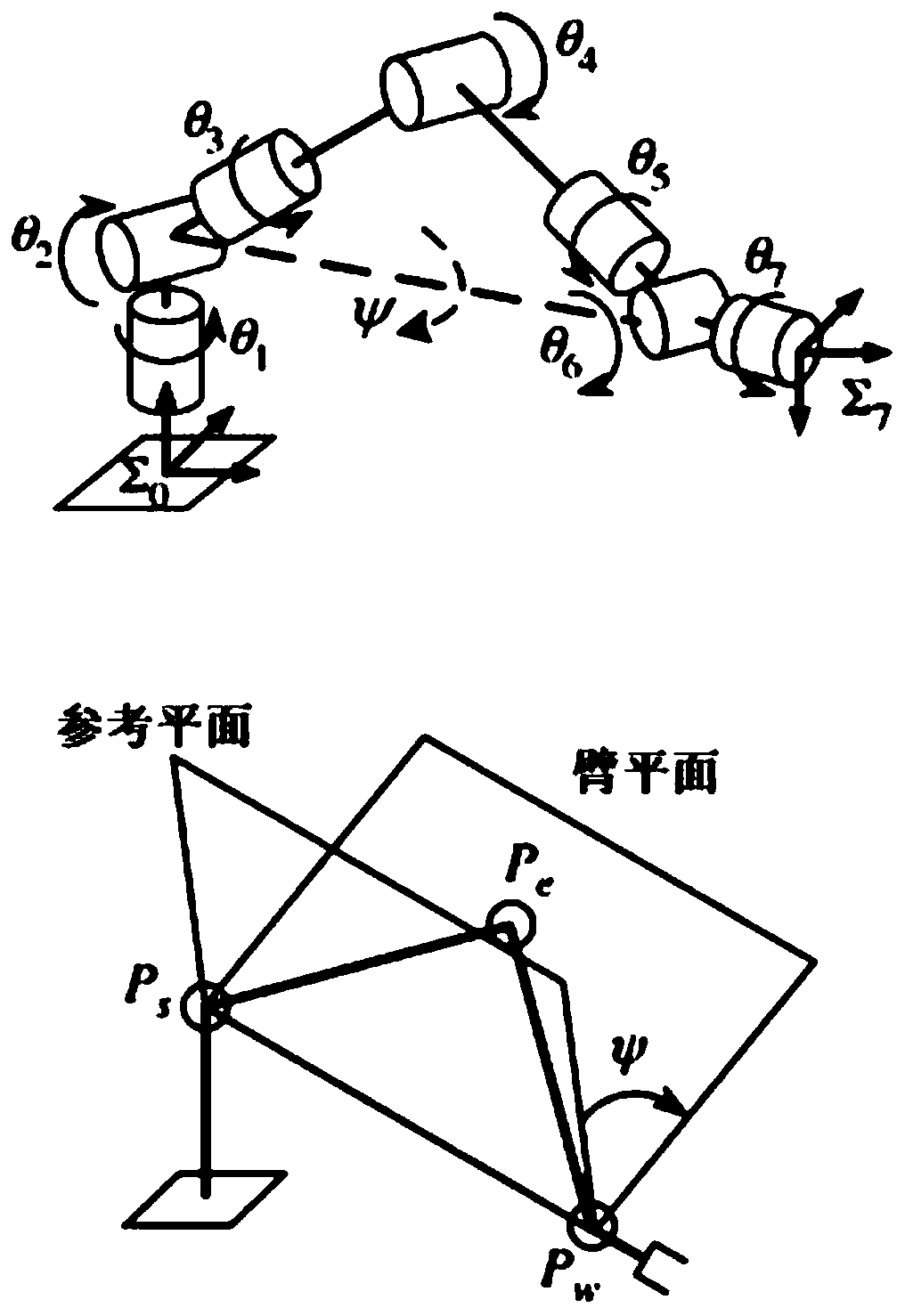
Seven-degree-of-freedom redundancy mechanical arm task constraint path planning method under Descartes space
ActiveCN110653805ASolve the problem that the optimization of the terminal trajectory cannot be guaranteedProgramme-controlled manipulatorJointsSimulationControl theory
The invention provides a seven-degree-of-freedom redundancy mechanical arm task constraint path planning method under a Descartes space, and relates to a redundancy mechanical arm task constraint pathplanning technology. A collision-free path is planned for a seven-degree-of-freedom mechanical arm end executor in the Descartes space for achieving task constraint, and the problem that an existingplanning method is mostly and only suitable for joint space planning, but can not ensure optimization of the end track is solved. According to the seven-degree-of-freedom redundancy mechanical arm task constraint path planning method under the Descartes space, an improved FMT* planning algorithm is adopted in the Descartes space, and the end collision-free path meeting the task constraint is planned out for a mechanical arm, so that the optimization of the end track is achieved, and the movement reasonability of the mechanical arm is ensured. The method comprises the steps that a description method of a mechanical arm end constraint position space based on a task function under the Descartes space is provided, Gaussian sampling is used for replacing a sampling scheme of an original algorithm, distance measurement based on the previous constraint position space is put forward, and the effectiveness of a sampling point and the effectiveness of local connection are judged with the adoption of a mode based on arm configuration description.
Owner:XIAN UNIV OF SCI & TECH
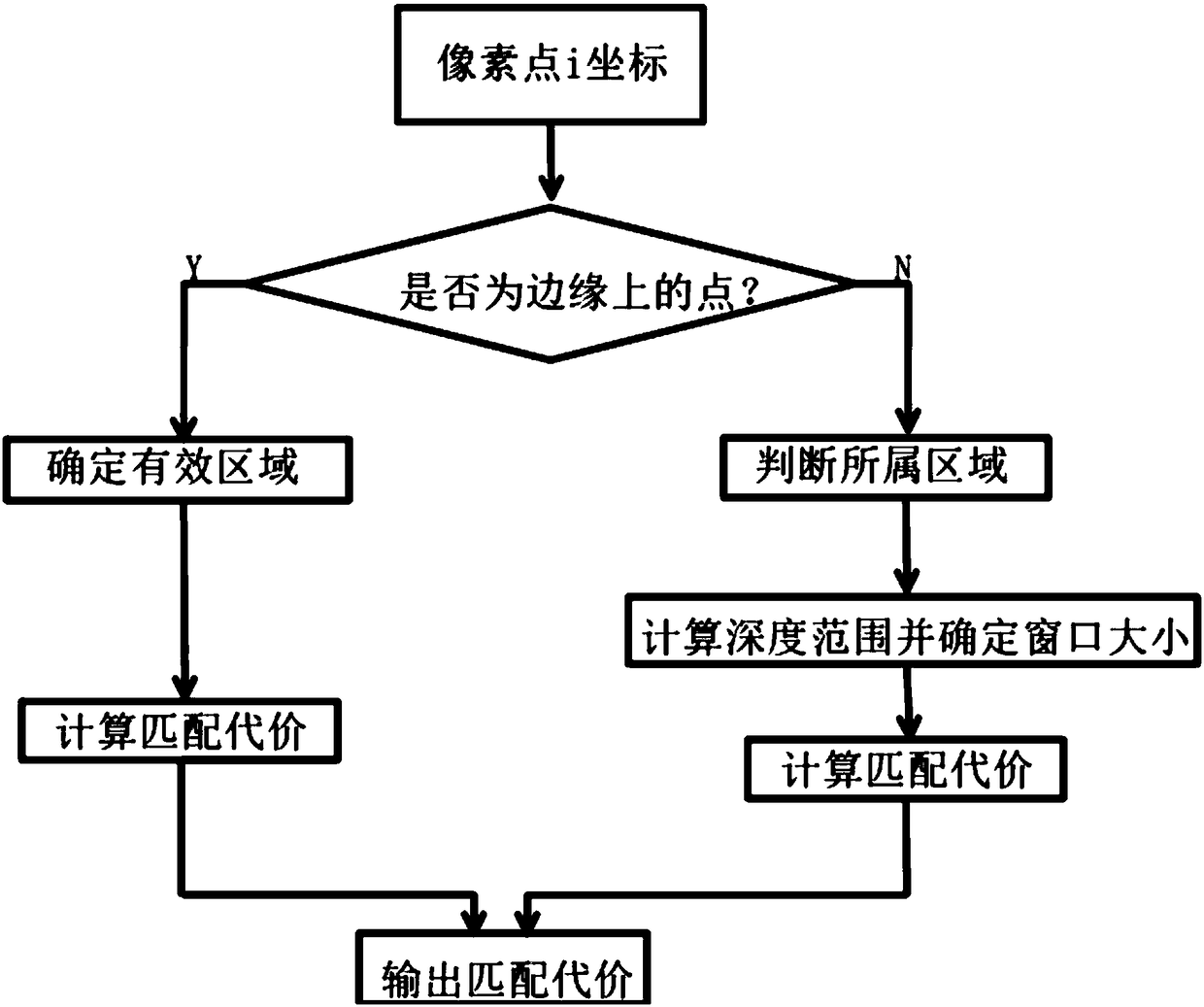
Stereo matching algorithm for weak texture region
ActiveCN108596975AImprove accuracyReasonable Parallax Range EstimationImage analysisParallaxCost aggregation
The invention discloses a stereo matching algorithm for a weak texture area. Firstly, Gaussian sampling is performed on an input image to construct to-be-matched image pairs at different scales; and then, the canny algorithm is used for performing edge detection on an original image to detect the edge of the object and mark off a low texture area; a smaller cost aggregation window is set for the edge area; for the low texture area, the constrained consistency of the same pixel between different scales is emphasized; the improved sliding window method is used for calculating the image pixel pair matching cost at each scale; the feature point matching result is used for delimiting the parallax search range; the aggregate matching cost corresponding to each parallax value in the parallax range is calculated through a multi-scale cost aggregation function; and the parallax value corresponding to the minimum cost is selected as a pixel parallax value; and a dense parallax map is obtained bytraversing the original image pixel. The stereo matching algorithm for a weak texture area in the invention has high matching precision for the low texture area and can effectively reduce mismatching.
Owner:SOUTH CHINA UNIV OF TECH
STDF (standard test data format) feature based human behavior recognition algorithm
The invention discloses an STDF (standard test data format) feature based human behavior recognition algorithm. The algorithm includes: according to a concept that strenuous exercise areas provide more discrimination information in behavior recognition, determining human exercise salient areas by means of depth information of video images, calculating optical flow features in areas to obtain an energy function for measuring area activeness, subjecting the exercise salient areas to Gaussian sampling according to the energy function to enable sample points to distribute in the exercise salient areas, taking the acquired sample points as action low-level features to describe human behaviors, and adopting an SVM (support vector machine) classifier for recognition of the behaviors by the aid of a BoW bag-of-word model. According to experimental data, average behavior recognition accuracy rate of the STDF feature based human behavior recognition algorithm reaches 92% in SwustDepth datasets.
Owner:SOUTHWEAT UNIV OF SCI & TECH
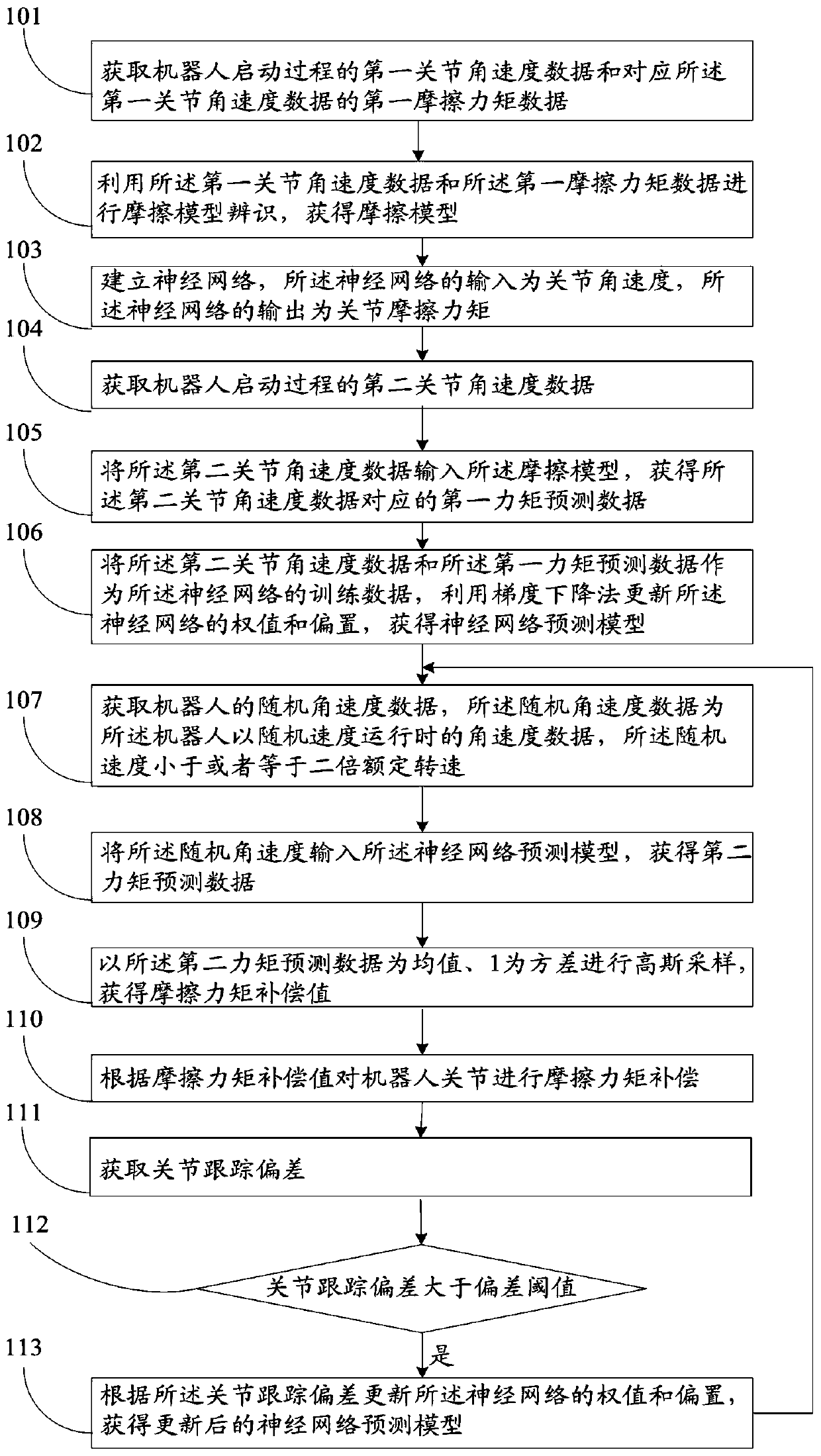
Robot joint friction torque compensation method and system
ActiveCN109732605AHigh training and learning process efficiencyImprove tracking speedProgramme-controlled manipulatorLocal optimumFriction torque
Owner:XIAMEN UNIV
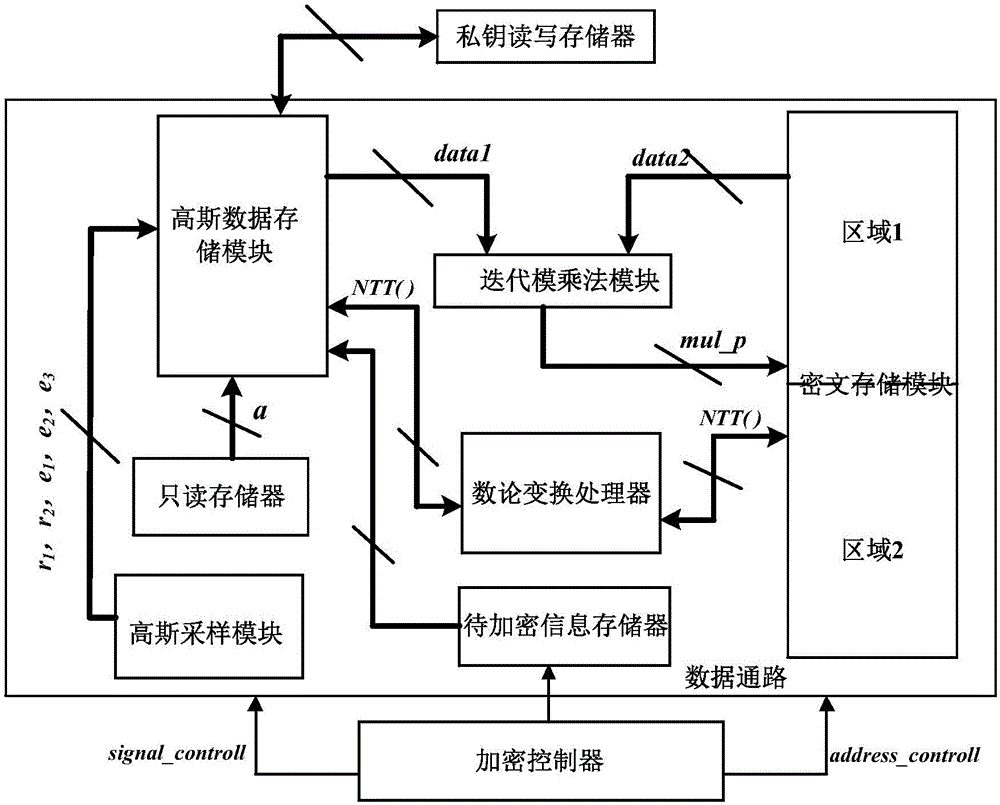
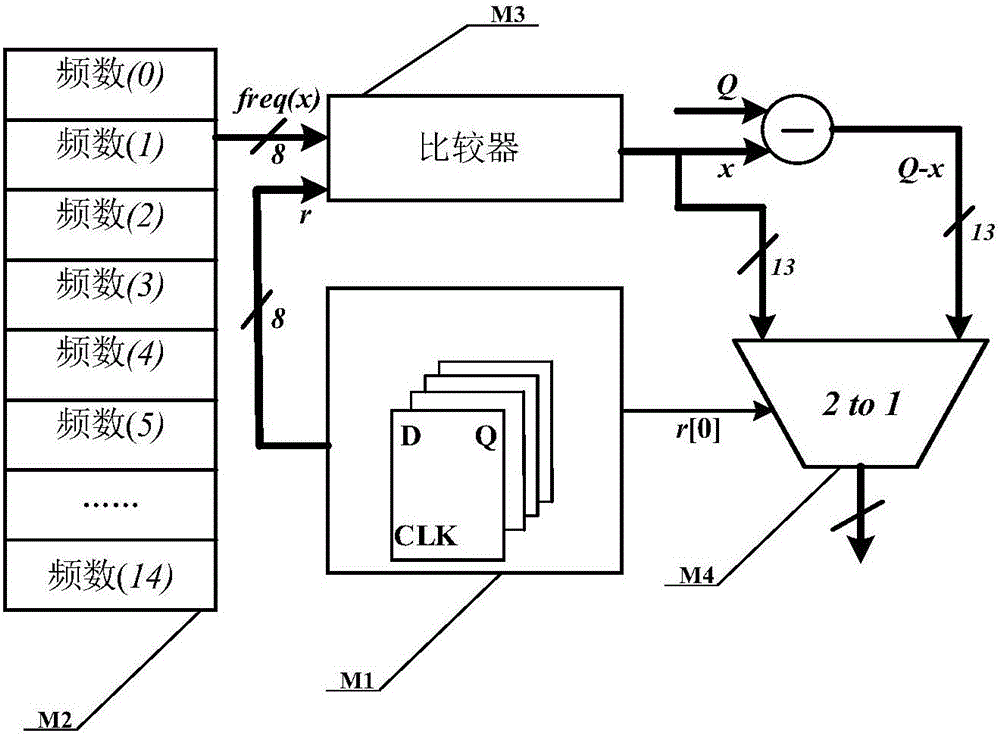
Encryption method for error learning problem in ring domain and circuit
ActiveCN106685663ASave resourcesLow costKey distribution for secure communicationPublic key for secure communicationCiphertextComputer science
The invention discloses an encryption method for an error learning problem in ring domain and a circuit. The method comprises the following steps: sampling a polynomial and a noise polynomial and performing the number-theory transformation; operating the result after the number-theory transformation, obtaining a public key and a ciphertext, and completing the encryption of the to-be-encrypted information. The invention also discloses a circuit to realize the method and the circuit comprises: an encryption controller, a to-be-encrypted information storage device, a Gaussian sampling module, a read-only storage device, a Gaussian data storage module, a number-theory conversion processor, an iterative modular multiplication module and a ciphertext storage module. The Gaussian sampling module samples and generates a polynomial and a noise polynomial; the number-theory conversion processor is used to perform the number-theory transformation to the polynomial, the noise polynomial and the constant polynomial and to generate the ciphertext after operations on the to-be-encrypted information, the noise polynomial and the public key. The method and the circuit of the invention greatly increase the operational efficiency of the circuit, reduce the loss of the circuit, and ease the realization cost of an encryption circuit for the error learning problem in ring domain.
Owner:HUAZHONG UNIV OF SCI & TECH
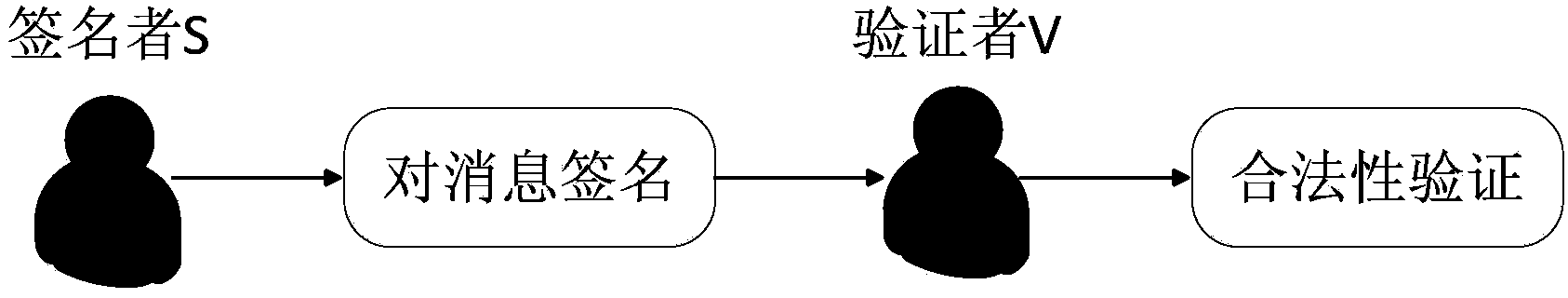
Signature verification method based on Gaussian sampling
ActiveCN104038347AImprove execution efficiencySmall amount of calculationUser identity/authority verificationGaussian samplingCipher
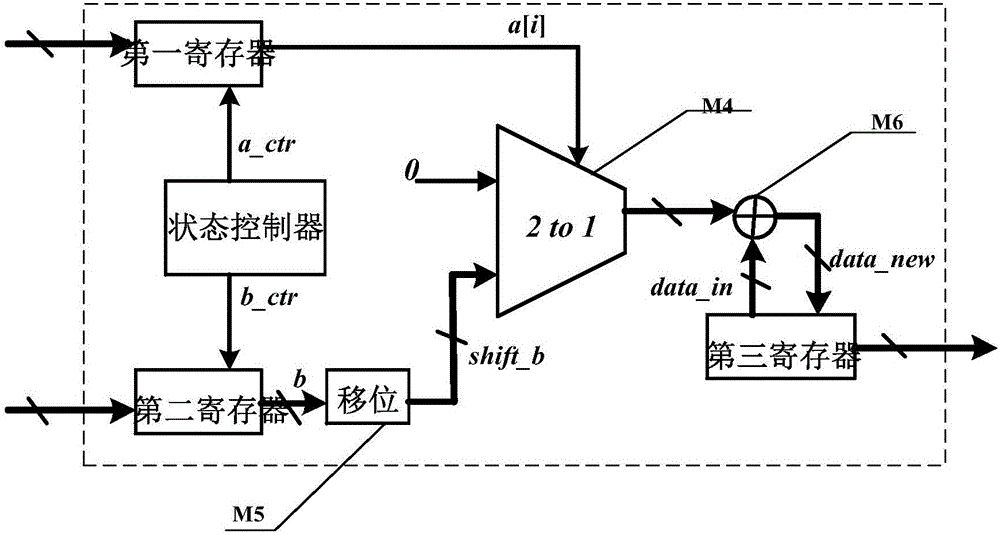
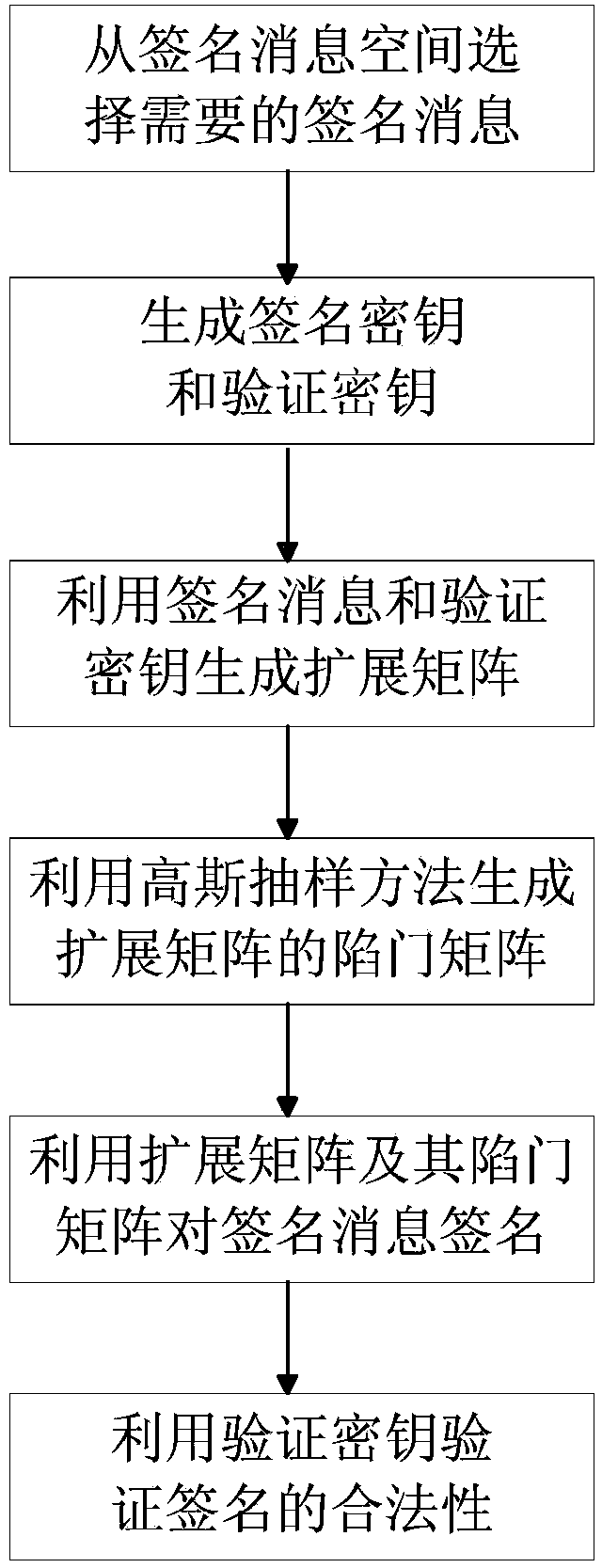
The invention discloses a signature verification method based on Gaussian sampling. The problem that an existing signature technology based on Gaussian sampling is low in execution efficiency when the modulus is not the power of two is mainly solved. The signature verification method based on Gaussian sampling comprises the steps that (1) parameters are selected, a key production algorithm is used for generating a signature key sk and a verification key vk; (2) the signature key sk is used for generating a trap door matrix R' of an expanding matrix AM; (3) the trap door matrix R' of the expanding matrix AM is used for signing a selected signature message M to obtain the signature sign; (4) the verification key vk is used for verifying the validity of the signature sign. According to the signature verification method, the calculated amount of the signature verification method based on Gaussian sampling is greatly reduced through an aspherical basic Gaussian sampling algorithm, and the signature verification method can be used for generation of signature in public key codes based on grids and personal private keys in encryption based on identities.
Owner:XIDIAN UNIV
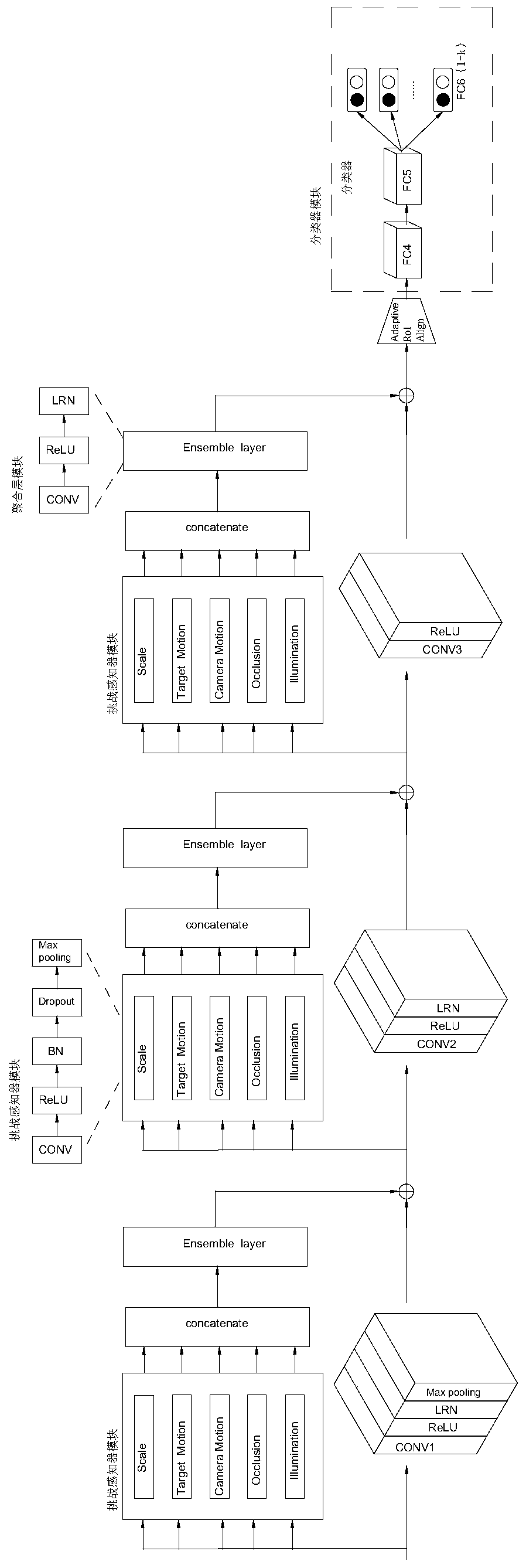
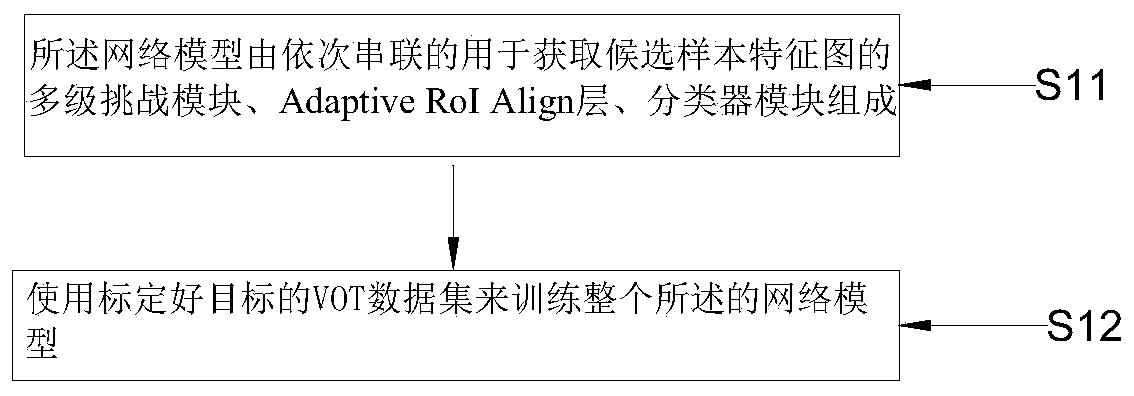
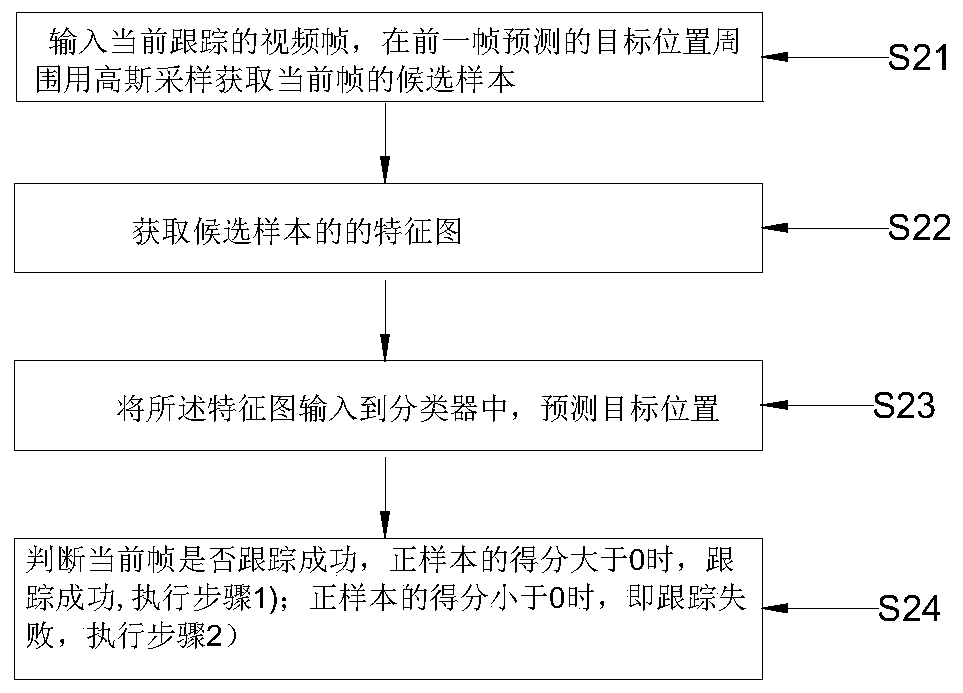
Training and tracking method based on multi-challenge perception learning model
ActiveCN110929848AIncrease diversityImprove feature extractionNeural architecturesNeural learning methodsPattern recognitionData set
The invention relates to a training and real-time tracking method based on a multi-challenge perception learning model, and the method sequentially comprises two parts: a model training process and atracking process carried out through a pre-trained model. The method comprises the following steps: S11, constructing a network model, S12, training the whole network model through employing a VOT data set with a calibrated target; S21, inputting a currently tracked video frame, and obtaining candidate samples of the current frame around the predicted target position of the previous frame by Gaussian sampling; S22, obtaining a feature map of the candidate sample; S23, inputting the feature map into a classifier module, and predicting a target position; S24, judging whether the current frame istracked successfully or not; according to the method, the richness of feature expression can be effectively increased, the tracking robustness is improved, and the real-time tracking performance is achieved.
Owner:ANHUI UNIVERSITY
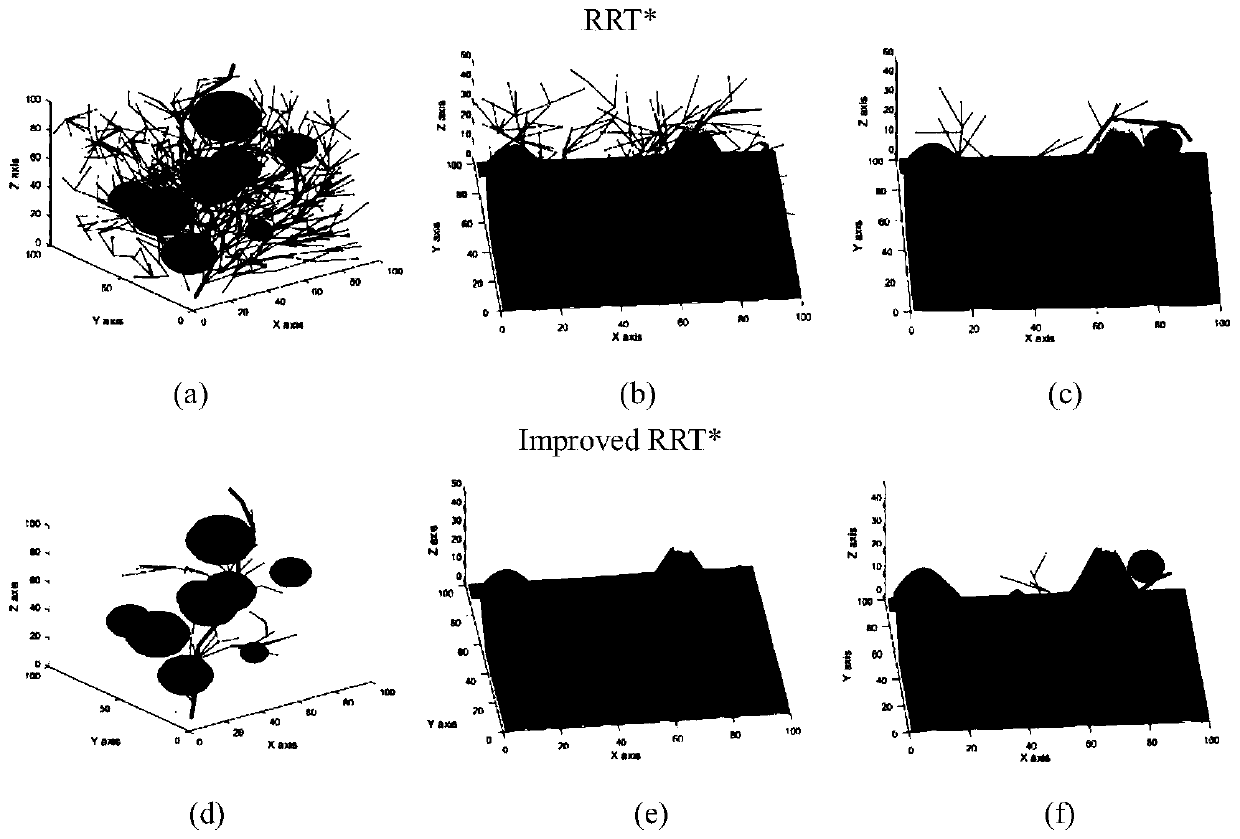
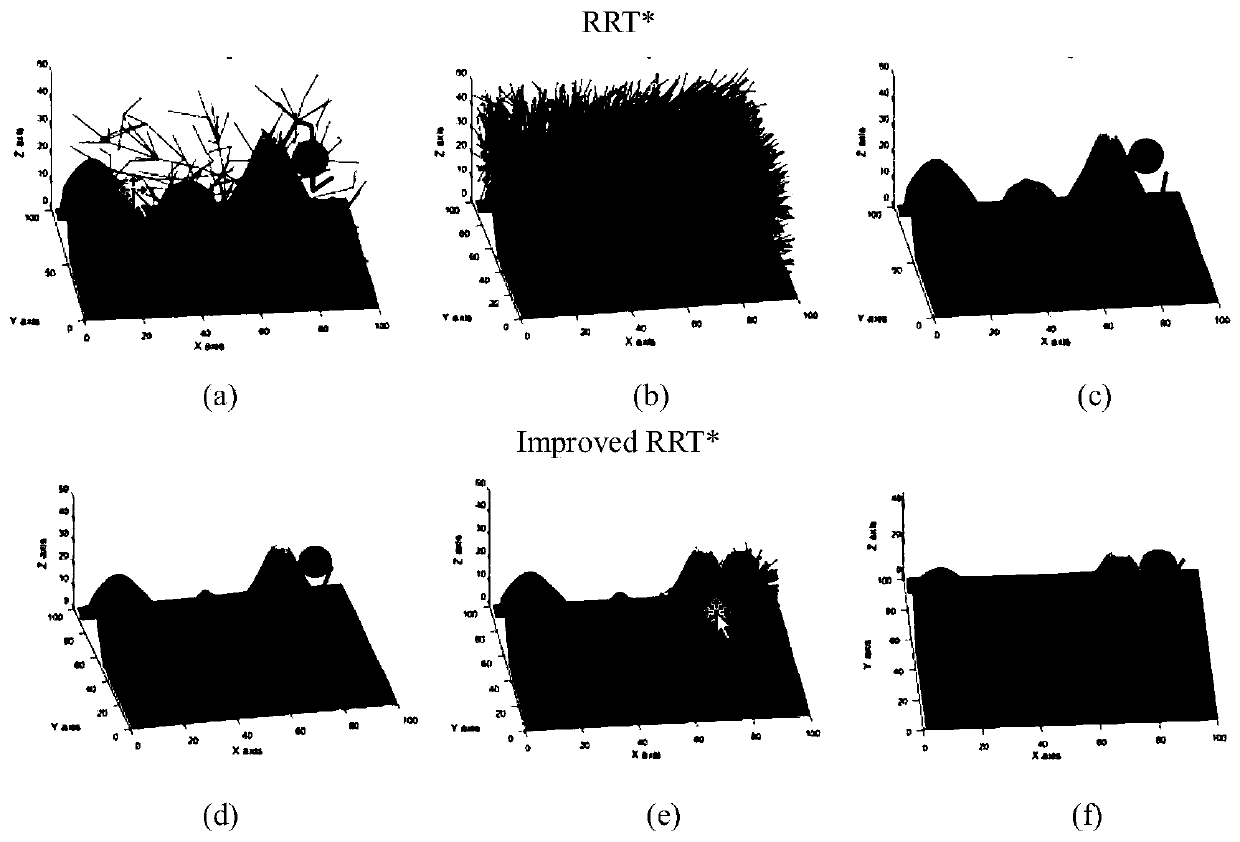
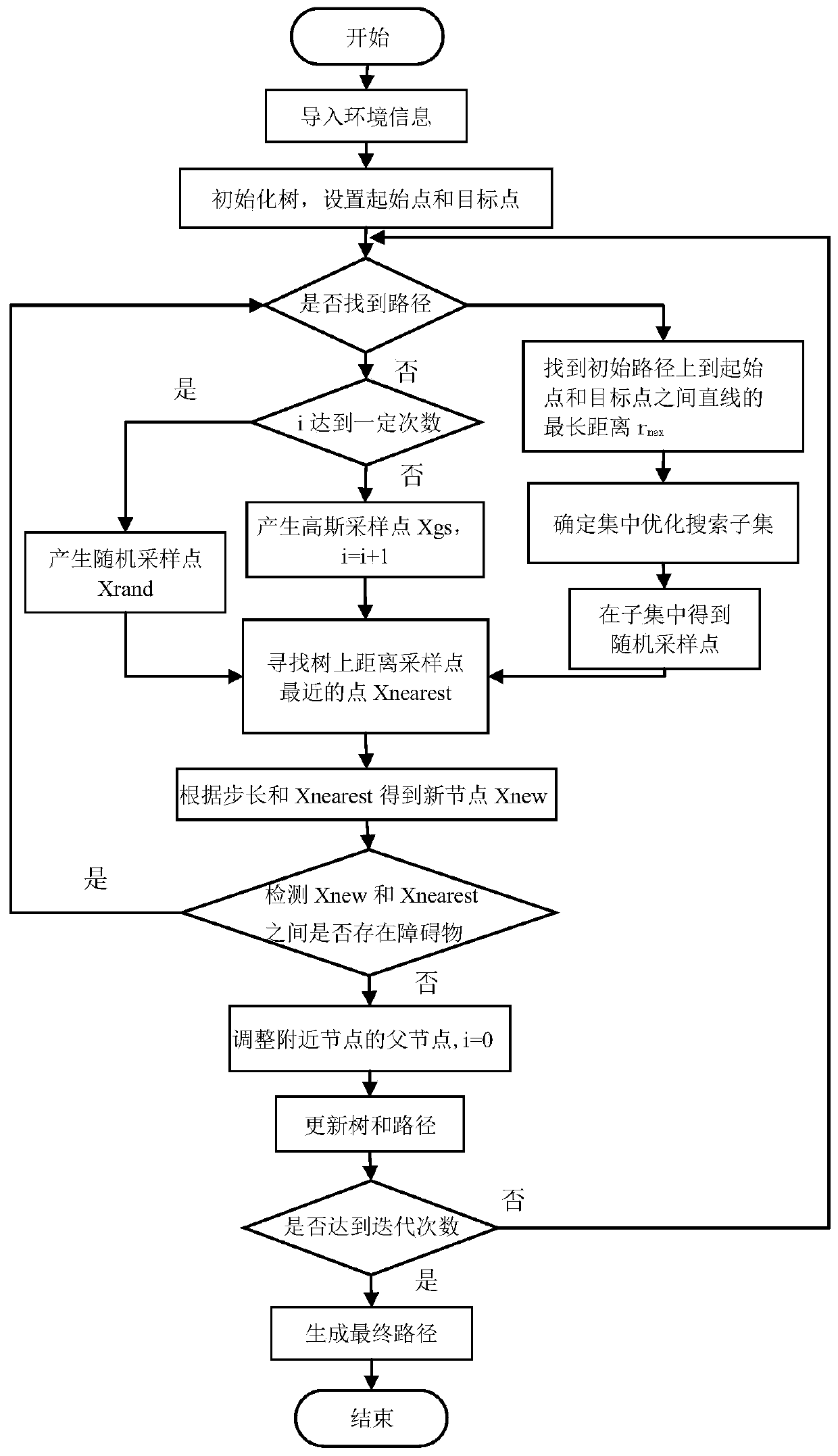
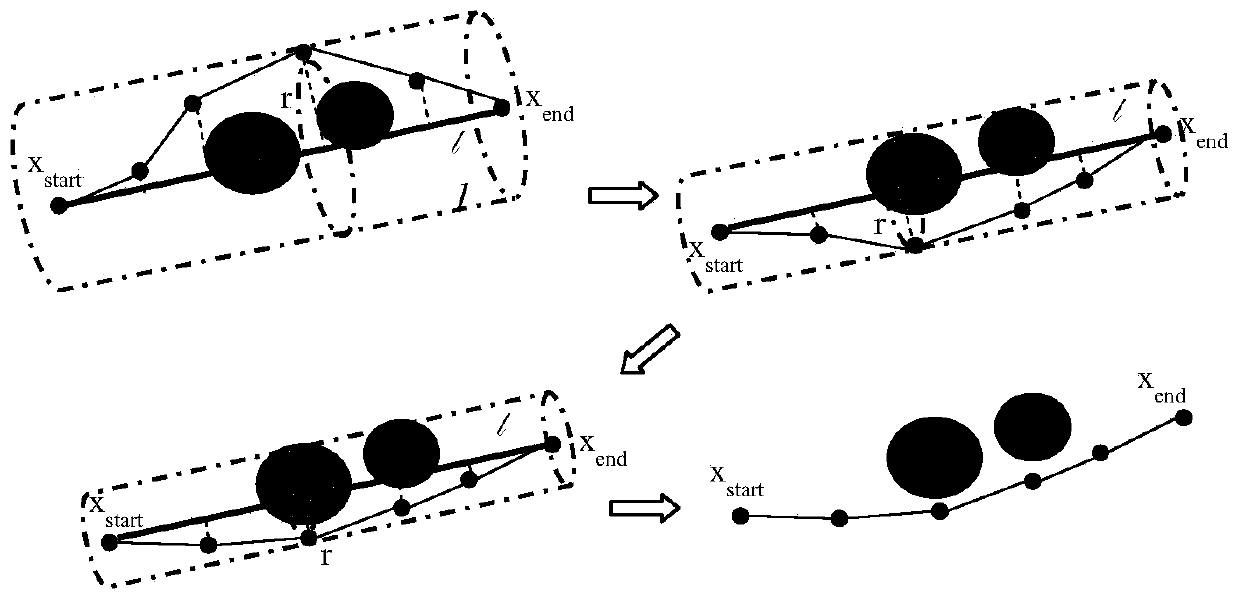
Fast underwater robot three-dimensional path planning method with target-oriented centralized optimization
ActiveCN110196602AReduce randomnessQuality improvementPosition/course control in three dimensionsAlgorithmImproved method
The invention discloses a fast underwater robot three-dimensional path planning method with target-oriented centralized optimization. A target-oriented Gaussian sampling strategy is introduced in an RRT* path planning method, thereby reducing the randomness of sampling points when underwater obstacle distribution is scarce; random disturbance is combined for sampling, a random tree can be reasonably away from an obstacle area, falling into the local minimum is avoided, and search is quickly orientated to the target; and a centralized optimization search strategy is used to perform path optimization processing on the initial path acquired in the invention, the optimization convergence rate and the path quality are improved, and progressive optimization is realized. Compared with the traditional RRT* method, the improved method disclosed in the invention plans a better initial path, the path optimization speed is quicker, and consumption of time and memory is greatly reduced.
Owner:HOHAI UNIV
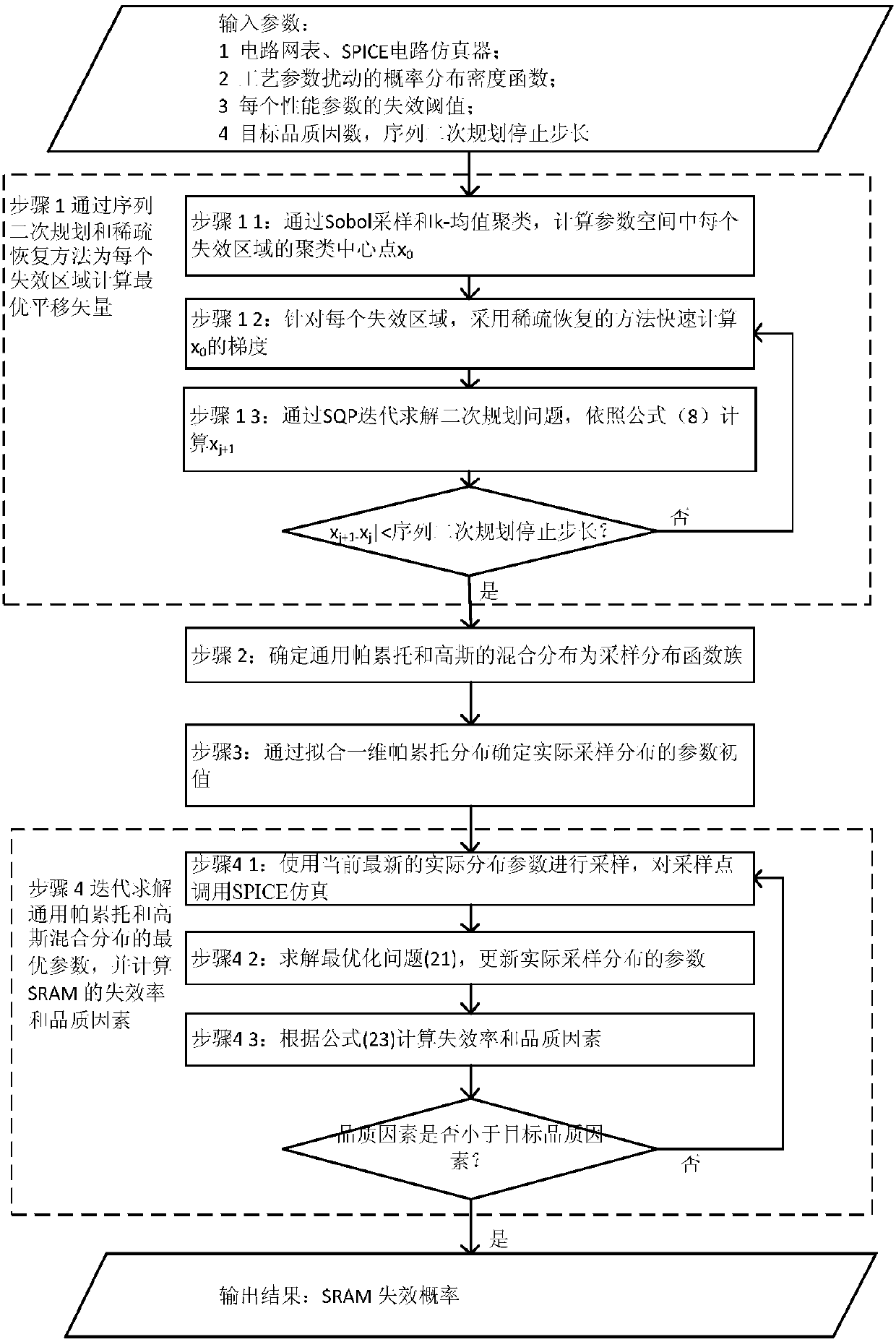
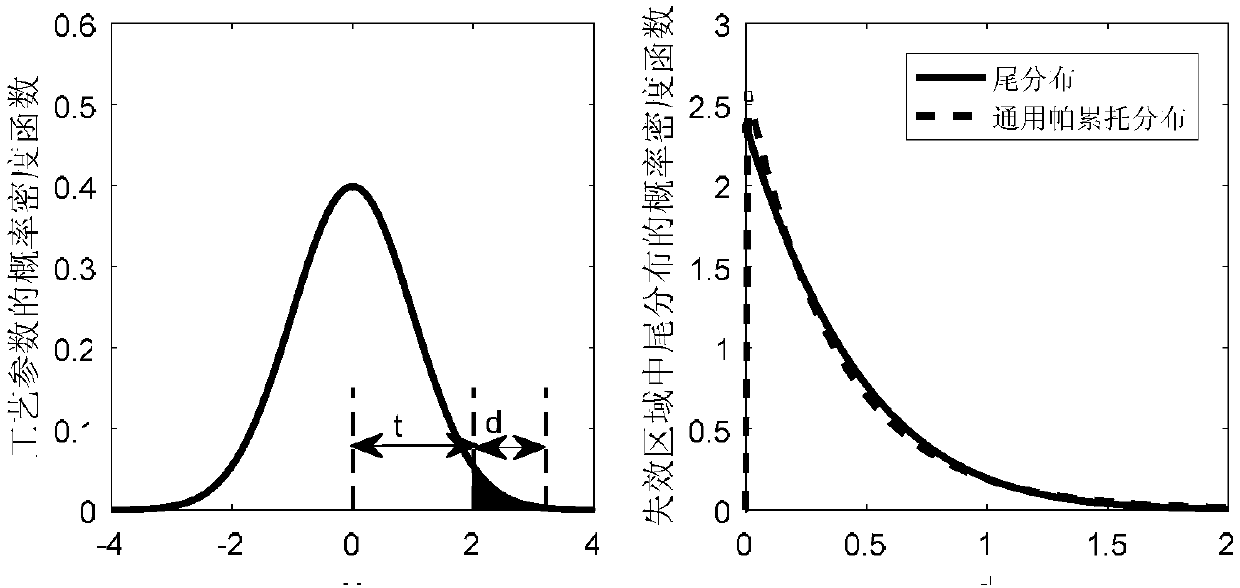
SRAM circuit yield analysis method based on non-Gaussian sampling
PendingCN110046365AFit closelySmall amount of calculationDesign optimisation/simulationCAD circuit designFailure rateStatic random-access memory
The invention belongs to the field of static random access memory circuit yield analysis in integrated circuit manufacturability design, and particularly relates to a method for obtaining an optimal actual sampling distribution parameter by adopting general Pareto and Gaussian joint distribution as an actual sampling distribution function family and minimizing cross entropy between actual samplingdistribution and ideal sampling distribution. The optimized actual sampling distribution is used for sampling and calculating the SRAM failure rate, so that the number of sampling points can be greatly reduced, and the sampling efficiency is improved. The key point of the invention lies in that general Pareto and Gaussian mixture distribution is adopted as a sampling distribution function family;aiming at the distributed parameter optimization problem, an iteration strategy is provided, sampling is continuously carried out, actual distribution parameters are updated, and the failure rate iscalculated until the failure rate meets the precision requirement. Experimental results show that the method provided by the invention is obviously superior to a method in the prior art.
Owner:FUDAN UNIV
NTRU encryption method based on R-LWE and security certification method thereof
InactiveCN110545179AAddresses the lack of strict security proofsImprove securityKey distribution for secure communicationPublic key for secure communicationEngineeringEncryption decryption
The invention discloses an NTRU encryption method based on R-LWE and a security certification method thereof. The NTRU ring structure is properly modified, the defect that NTRU lacks strict security certification is overcome through parameter definition, key pair acquisition through Gaussian sampling, encryption and decryption, and the proven NTRU encryption method based on the R-LWE problem is further verified by certifying the security of the NTRU encryption method. According to the R-LWE-based NTRU encryption method and the security certification method thereof, the security of the encryption method can be effectively certified, a screening function is added when a key pair is generated, and a lattice attack is effectively avoided.
Owner:中芯昊月(深圳)科技控股有限公司
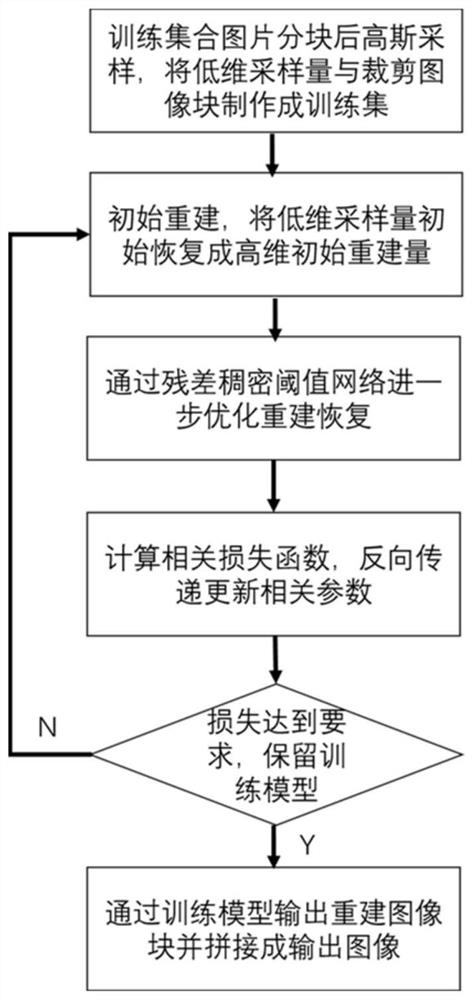
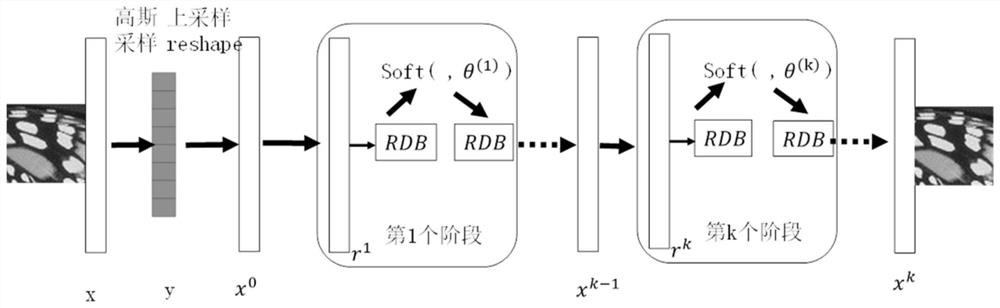
Image compressed sensing reconstruction method based on residual dense threshold network
PendingCN112991472AImprove interpretabilitySolve the reconstruction effect needs to be improvedGeometric image transformationImage codingReconstruction methodEngineering
The invention discloses an image compressed sensing reconstruction method based on a residual dense threshold network, and the method comprises the steps: carrying out the partitioning of an original natural image, carrying out the sampling through a Gaussian sampling matrix, and making a training set through the low-dimensional sampling amount and cut image blocks; recovering the low-dimensional sampling amount into a high-dimensional initial reconstruction image block through linear convolution; further optimizing and reconstructing the initial reconstructed image through the built residual dense threshold network; calculating a corresponding loss function, reducing loss through an optimizer, and carrying out back propagation on corresponding parameters; retaining the corresponding training model when the loss meets the requirement; and outputting the reconstructed image blocks through the training model and splicing the reconstructed image blocks into a final output image. Compared with an existing compressed sensing reconstruction method, the method has obvious advantages in reconstruction quality and reconstruction time.
Owner:SOUTH CHINA UNIV OF TECH
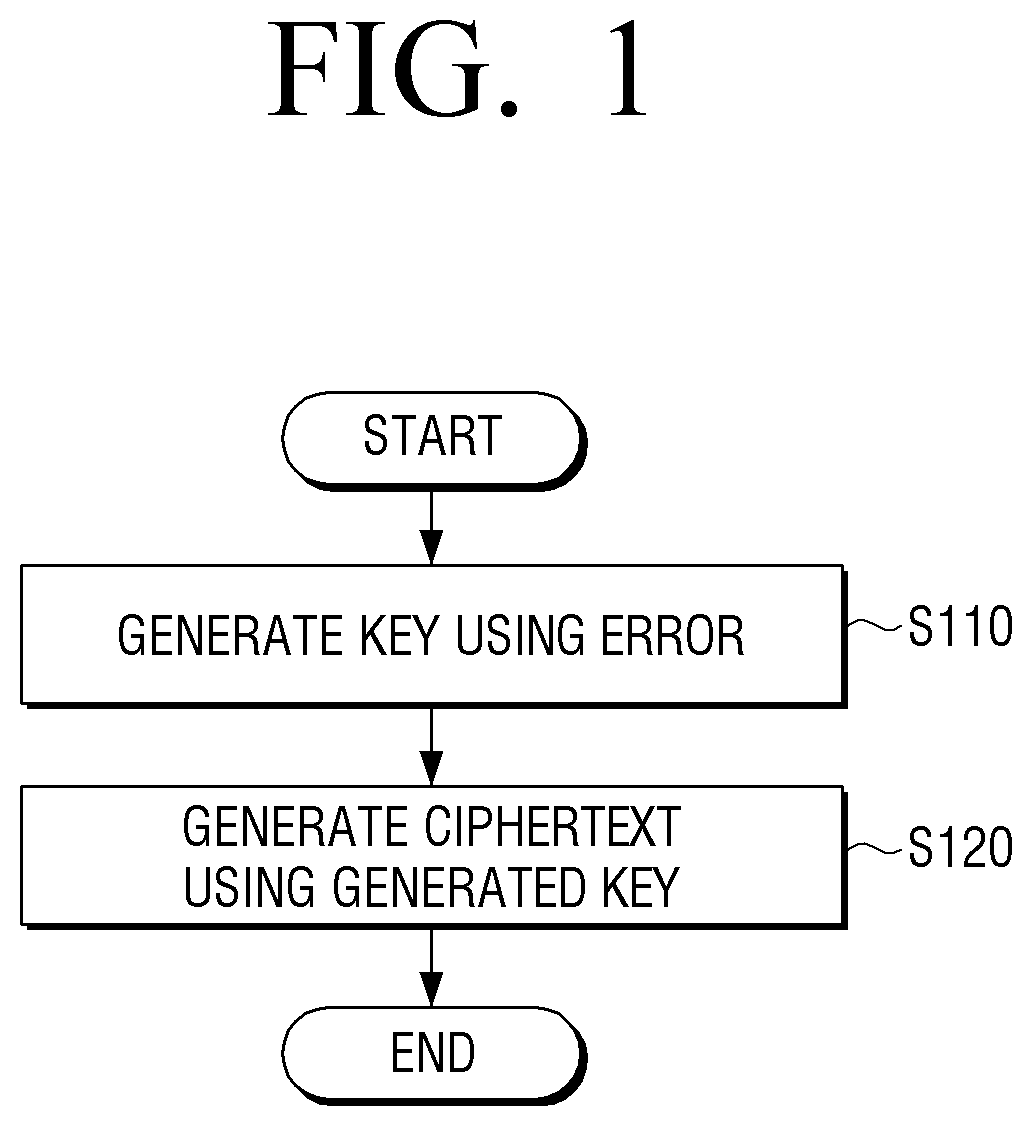
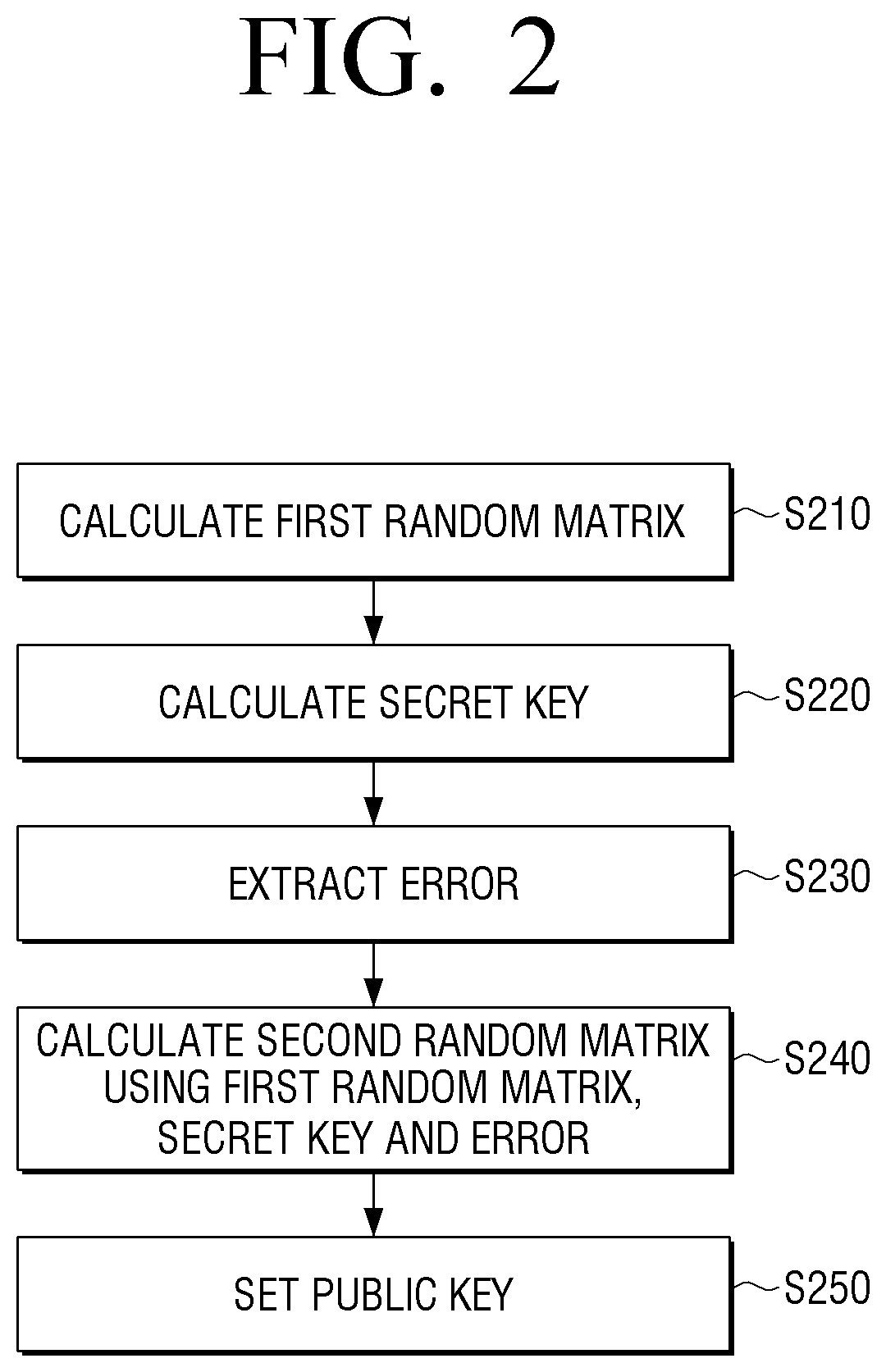
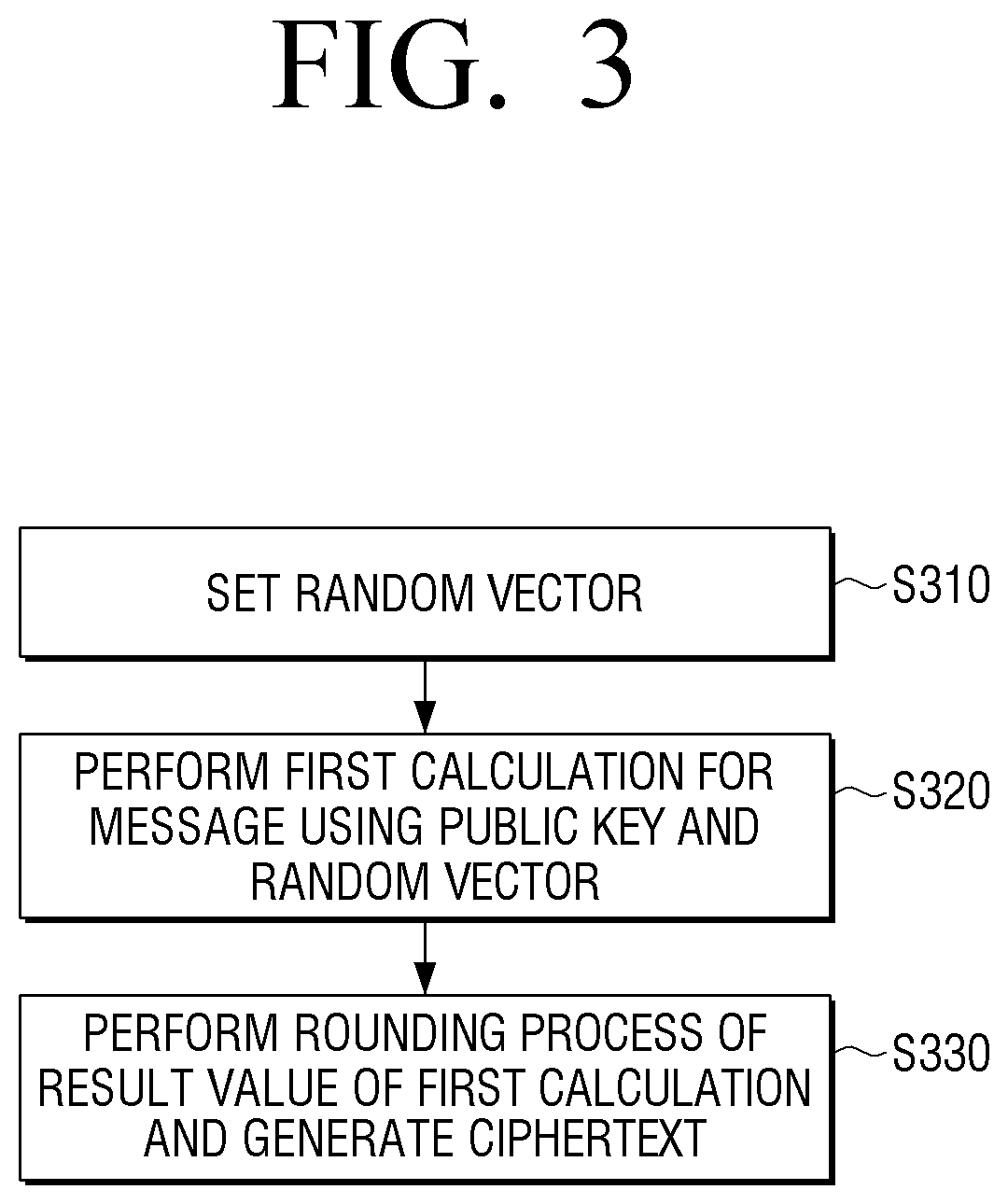
Calculation device for encryption using public key and encryption method thereof
ActiveUS20200169384A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesAlgorithmCiphertext
An encryption method includes: calculating a second random matrix using a first random matrix and a secret key, and generating a ciphertext corresponding to a message using the second random matrix. The generating of the ciphertext includes: performing a rounding process for sending the generated ciphertext to a smaller modulus area. The generating of the ciphertext includes performing message encryption without Gaussian sampling.
Owner:CRYPTO LAB INC
Long-time target tracking method based on depth detection
ActiveCN111274917AAlleviate the problem of imbalance between positive and negative samplesInternal combustion piston enginesCharacter and pattern recognitionInformation processingAlgorithm
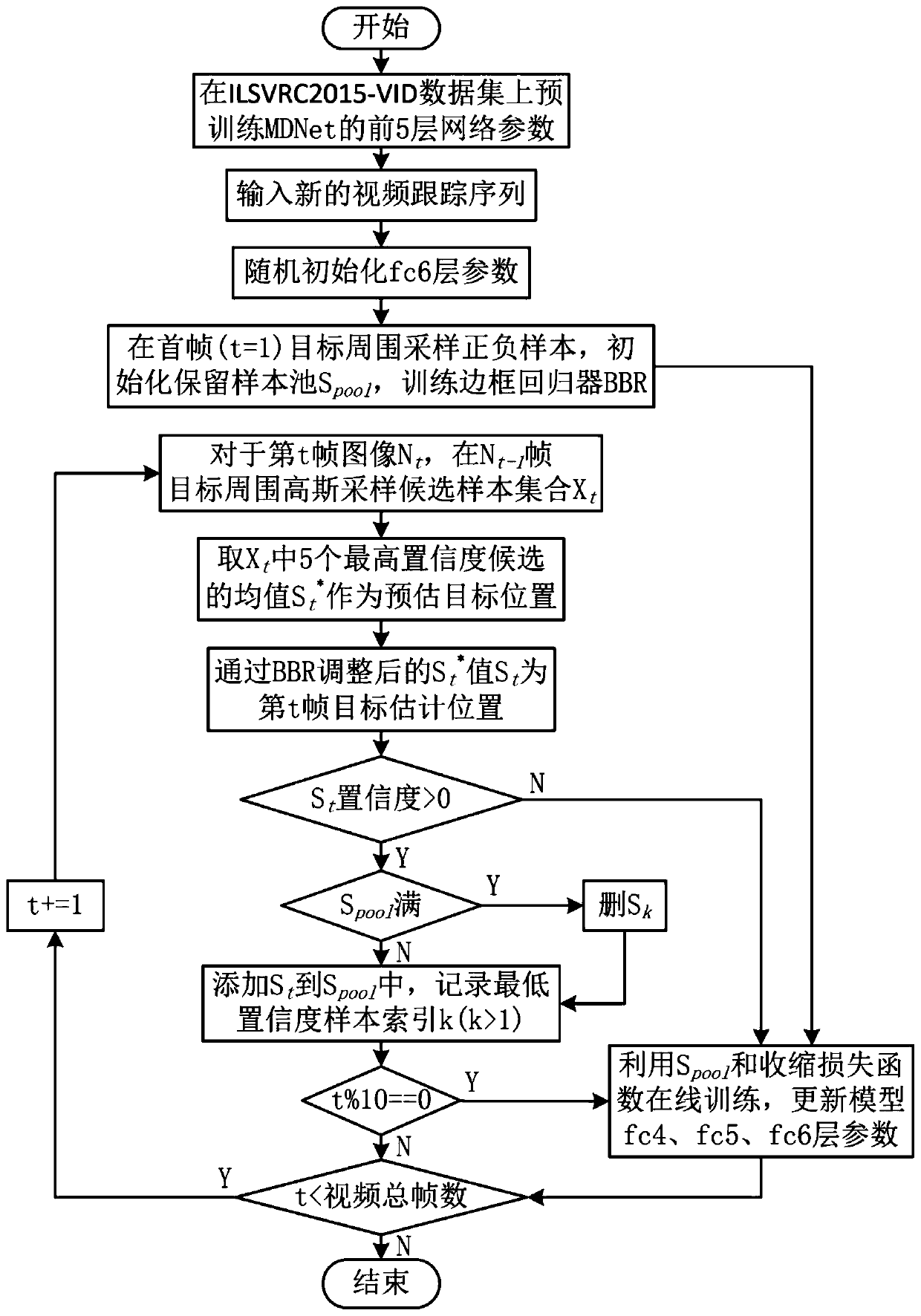
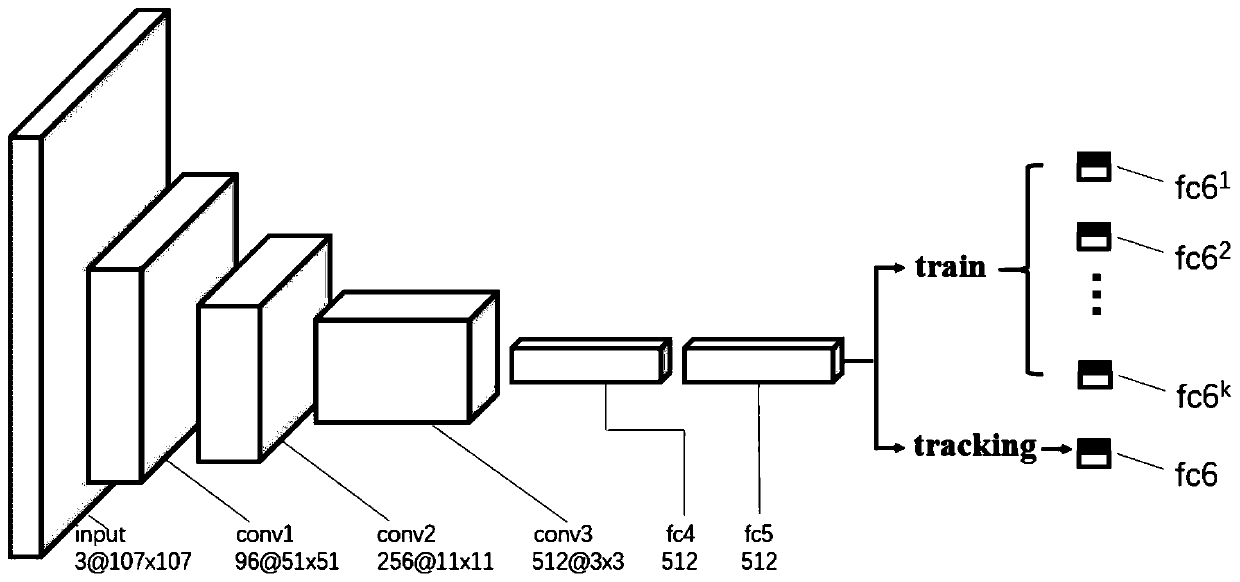
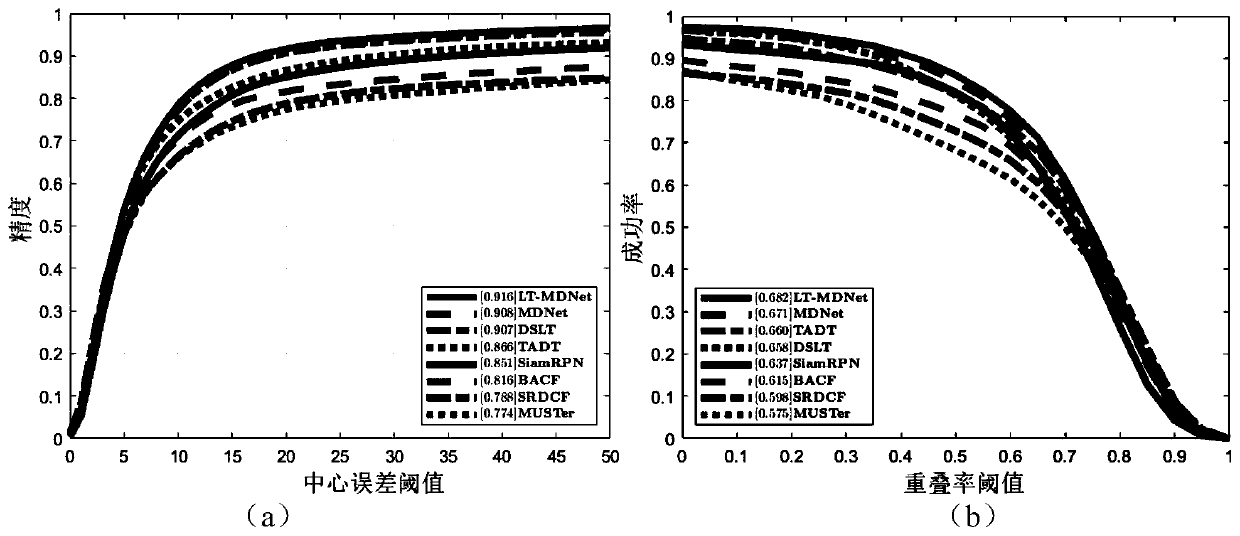
The invention discloses a long-time target tracking method based on depth detection, and belongs to the field of pattern recognition and intelligent information processing. According to the method, anMDNet depth detection tracking framework is adopted, and the problem of imbalance of positive and negative samples during sampling is solved by improving a shrinkage loss function on the basis of difficult-to-separate sample mining; designing and maintaining a high-confidence reserved sample pool during online tracking, reserving a first-frame target and high-confidence result sample characteristics, and performing online training by utilizing the reserved sample pool to update model parameters; and finally, calculating confidence coefficients of candidate samples obtained by Gaussian sampling around the target position of the previous frame through the model so as to track the position of the moving target and maintain the robustness of the model through effective updating. According tothe method, excellent tracking precision and success rate are kept in a complex long-term tracking environment, the target position can be accurately positioned when the target is shielded and reappears after the view, and the design requirement of an actual engineering system is met.
Owner:JIANGNAN UNIV
Mobile robot path planning method for improving probabilistic roadmap method
ActiveCN110411454AReduce the number of pathsImprove securityNavigational calculation instrumentsCharacter and pattern recognitionSimulationMobile robots path planning
The invention relates to a mobile robot path planning method for improving a probabilistic roadmap method, and relates to the field of robot navigation. On the basis of the probabilistic roadmap method (PRM), an actual path planning function of a mobile robot is achieved. According to the specific technical scheme, an actual environment map is converted into a binary map, self-adaptive sampling and Gaussian sampling are combined in a sampling stage, the number of sampling points in difficult areas (such as narrow channels) is increased, so that the binary map has stronger adaptability to complex maps; in a query phase, by changing the distance connecting the sampling points, unreasonable paths are reduced, thereby effectively increasing the planning speed. The mobile robot path planning method has a simple procedure and a high calculation speed, effectively improves the shortcomings of an original algorithm, and greatly improves the work efficiency of self-mobile robot path planning.
Owner:XIAN TECHNOLOGICAL UNIV
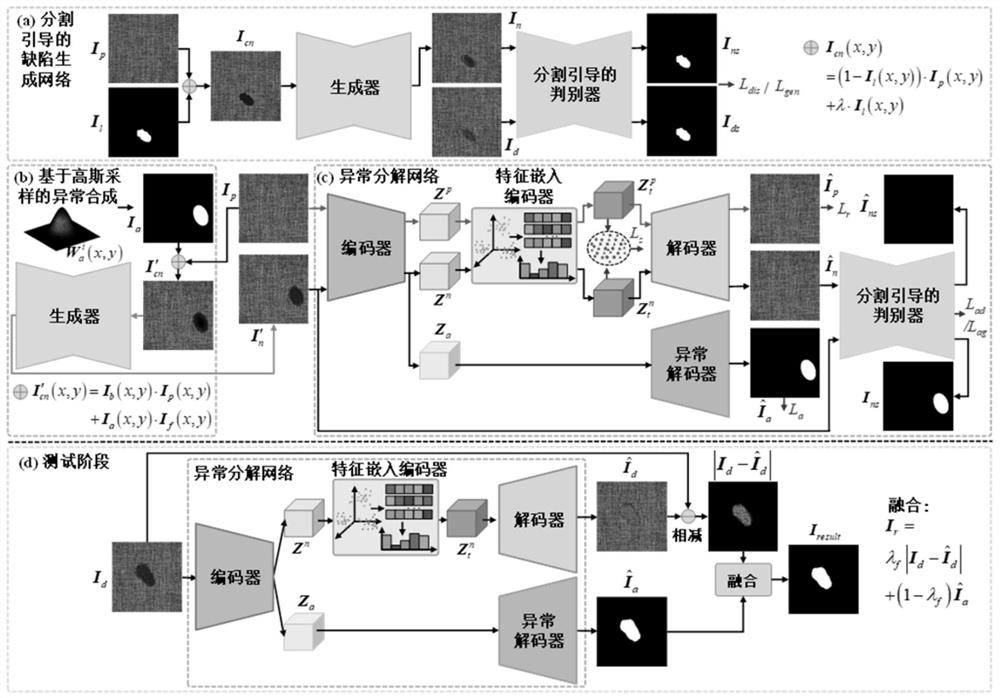
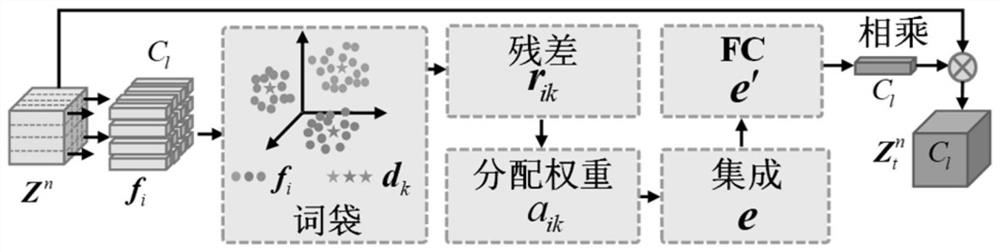
Texture surface defect detection method and system based on abnormal synthesis and decomposition
ActiveCN112700432ASolve the problem of small defect sample sizeImprove defect detection accuracyImage enhancementImage analysisImaging processingRadiology
The invention discloses a texture surface defect detection method and system based on abnormal synthesis and decomposition, and belongs to the field of image processing. According to the method, a segmentation-guided defect generation network is constructed, a large number of defect samples similar to real defects can be generated by using a small number of real defect training samples, and meanwhile, an anomaly synthesis method based on Gaussian sampling is provided, and anomaly negative samples can be randomly synthesized by using defect-free positive samples, so that the problem of small quantity of defect samples in industry can be solved; the defect detection precision is further improved; according to the method and system, the abnormal negative sample is decomposed into the texture background image and the abnormal mask image by adopting the abnormal decomposition network, so that defects can be effectively prevented from being reconstructed into the texture background, the texture background reconstruction precision is improved, the defect area can be accurately segmented, and the residual image and the abnormal segmentation image are fused; therefore, the defect detection rate is improved, and the defect over-detection rate is reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
Multi-scale quantum resonance solving algorithm for multi-choice multi-dimensional knapsack problem
InactiveCN109272121ALarge number of samplesAvoid falling intoComputing modelsKnapsack problemTrust region
The invention discloses a classical combinatorial optimization problem in the field of operational research, i.e., the multi-scale quantum resonance solving algorithm for a multi-choice and multi-dimensional knapsack problem, firstly, the Lagrange relaxation dual model is established for the original problem model, which greatly reduces the constraint conditions and evaluates the value of the items in the group by using Lagrange value. On this basis, the MMKP approximate kernel problem is introduced, which is heuristic to find the optimal solution and reduces the scale of the problem. In addition, based on the approximate kernel problem, a mixed Gaussian sampling model is constructed to guide the algorithm to intensify the search in the trusted region and to uniformly search in the untrusted region, which improves the solution accuracy and convergence speed.
Owner:CHENGDU UNIV OF INFORMATION TECH
Self-adaptive super-resolution method based on meta transfer learning
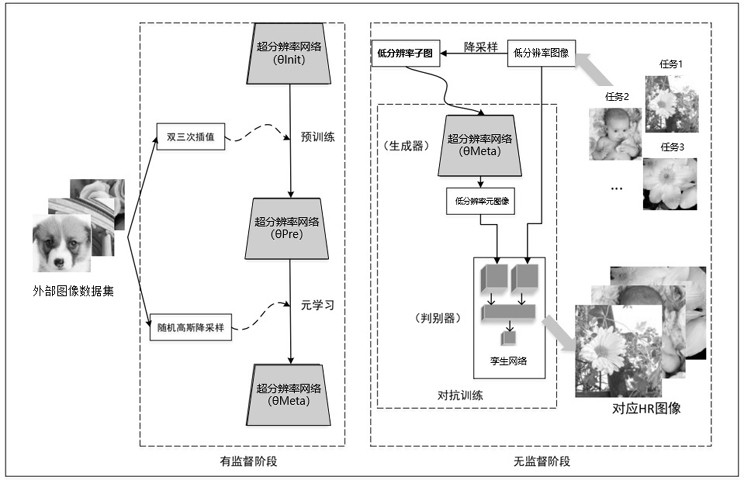
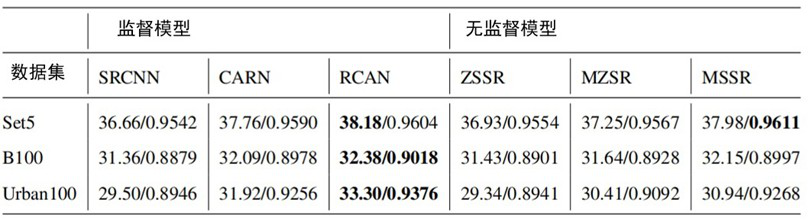
PendingCN113487482APromote reconstructionImprove generalization abilityImage enhancementImage analysisPattern recognitionData set
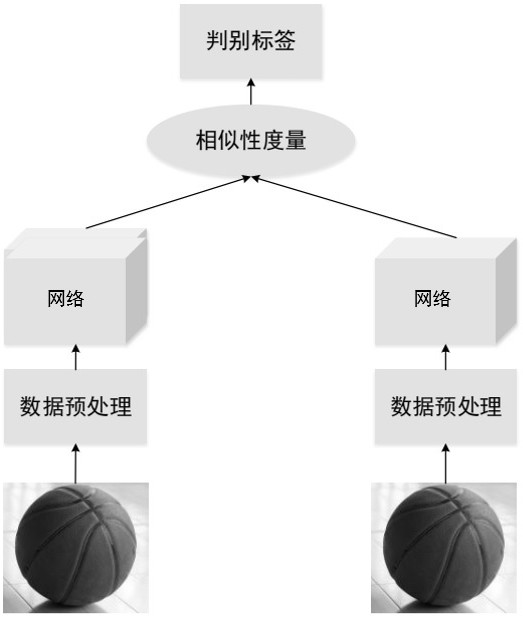
The invention provides a self-adaptive super-resolution method based on meta transfer learning, which comprises the following steps: pre-training a self-adaptive super-resolution model based on meta transfer learning through an external image data set, so that the model can learn prior information of image reconstruction; performing random parameter down-sampling on images in the external image data set through a random Gaussian sampling method, so that training data in a meta transfer learning process contains multi-task information; performing down-sampling on a to-be-reconstructed target low-resolution image to obtain a low-resolution sub-image, and training the model by taking the low-resolution image and the low-resolution sub-image as training data; performing adversarial training by means of a twin neural network and the model, and adjusting model parameters by comparing the difference between a low-resolution image and a low-resolution sub-image to complete model training; and applying the model to a target image to reconstruct and generate a super-resolution image. According to the method, the image reconstruction quality can be improved, and the generalization ability of the super-resolution model is enhanced.
Owner:WEIHAI POWER SUPPLY COMPANY OF STATE GRID SHANDONG ELECTRIC POWER COMPANY
Circle detection method based on ternary Gaussian differential evolution algorithm
ActiveCN108665451AIncrease search areaImprove detection efficiencyImage enhancementImage analysisPattern recognitionDigital image
The invention discloses a circle detection method based on a ternary Gaussian differential evolution algorithm. The circle detection method based on the ternary Gaussian differential evolution algorithm applies the ternary Gaussian differential evolution algorithm to search for a parameter of a circle in a digital image. In the ternary Gaussian differential evolution algorithm, Integrating a meaninformation and a random individual of a population into a Gaussian sampling operator to improve a search area of the algorithm, and improving a local search ability of the algorithm by using an information of the best individual in the population; thereby speeding up the convergence. According to the circle detection method based on the ternary Gaussian differential evolution algorithm, the efficiency of the circle detection in the digital image can be improved.
Owner:JIANGXI UNIV OF SCI & TECH
Weak and small target joint detection and tracking system and method based on random finite set
ActiveCN112215146AReduce computational complexityEffective trackingScene recognitionComputational physicsSmall target
The invention provides a weak and small target joint detection and tracking system and method based on a random finite set, and the system comprises: an infrared image measurement module which is usedfor obtaining an infrared measurement image of a ground environment and a target, thereby obtaining a target measurement domain; the target prediction module that is used for calculating a target measurement domain to obtain a target prediction state and a target prediction track label, and performing Gaussian sampling; the target updating module that is used for calculating a likelihood function, and calculating to obtain an updating state of the target and a target updating track label according to the likelihood function; and a hypothesis cost function associated with the target and measurement is built, and a hypothesis corresponding to the maximum weight is selected according to the hypothesis weight to obtain a target state and a track estimation value at the current moment. According to the invention, on the basis of obtaining target infrared measurement in a complex environment, effective detection and tracking of an infrared weak and small target in a complex noise environment are realized through measurement difference, self-adaptive extraction of a new target and optimal track allocation.
Owner:XI AN JIAOTONG UNIV
Hardware implementation method for ORB feature point extraction with good real-time performance
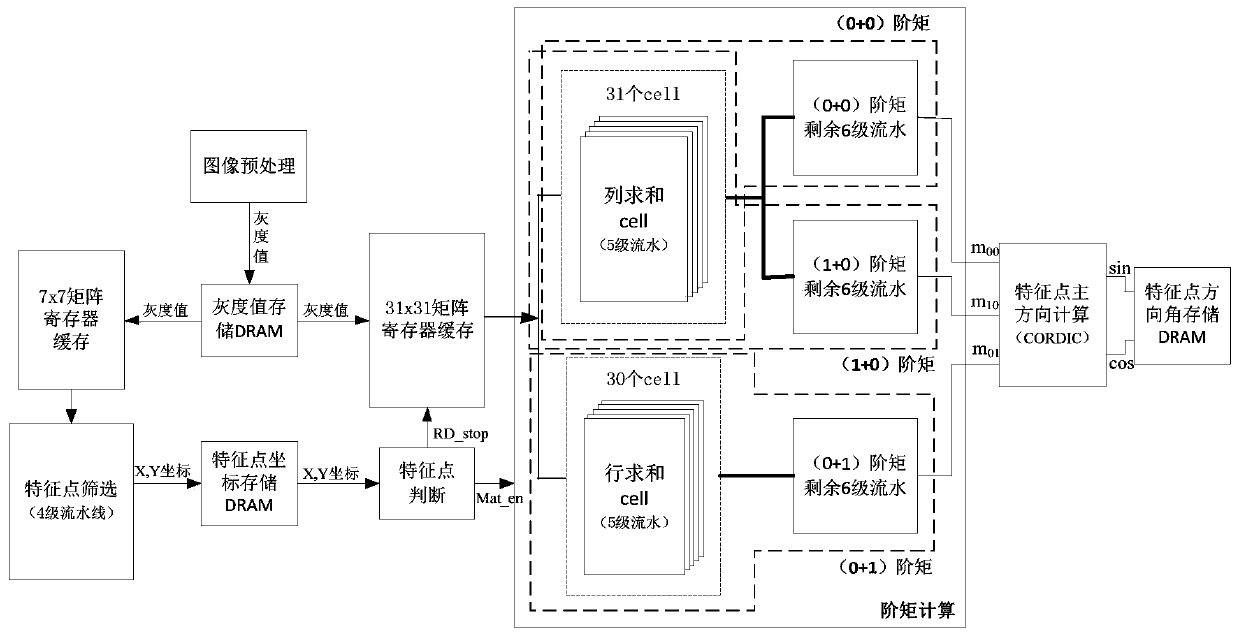
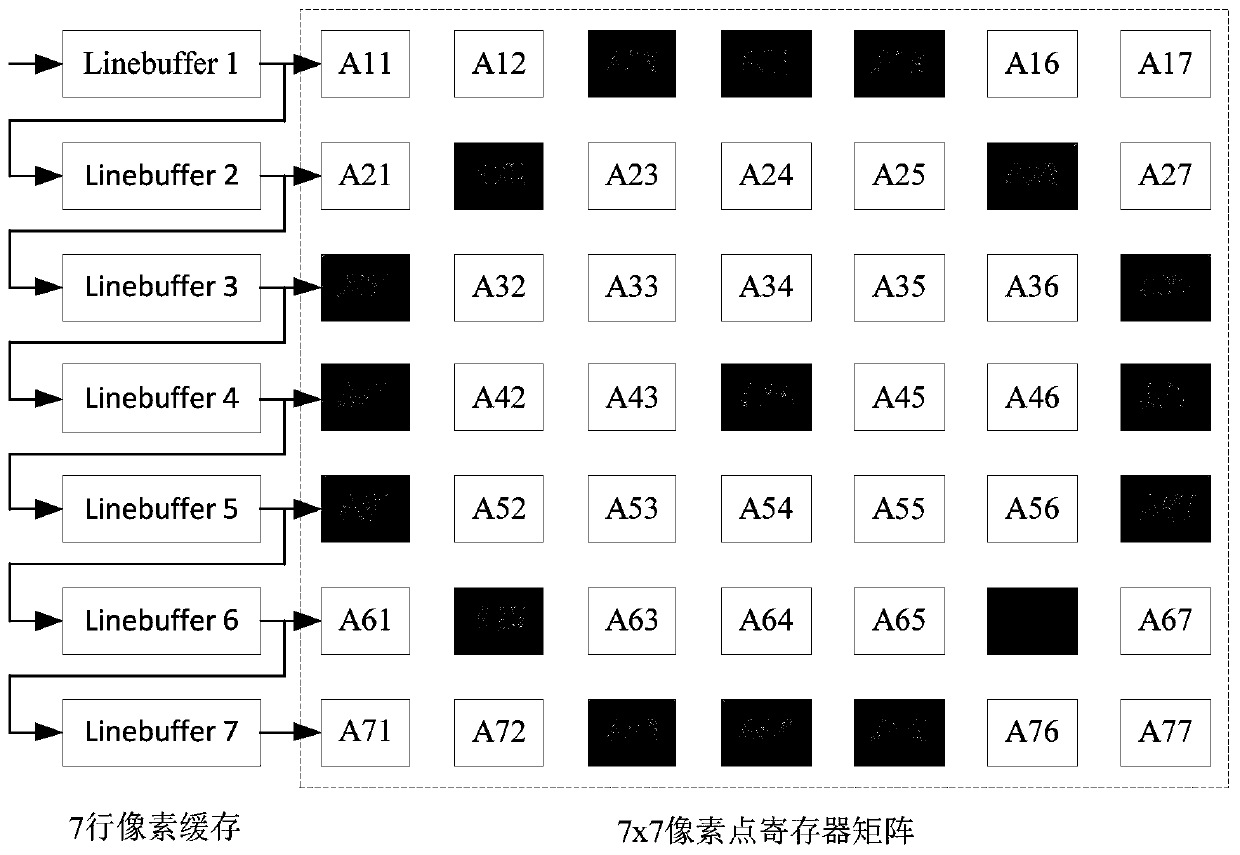
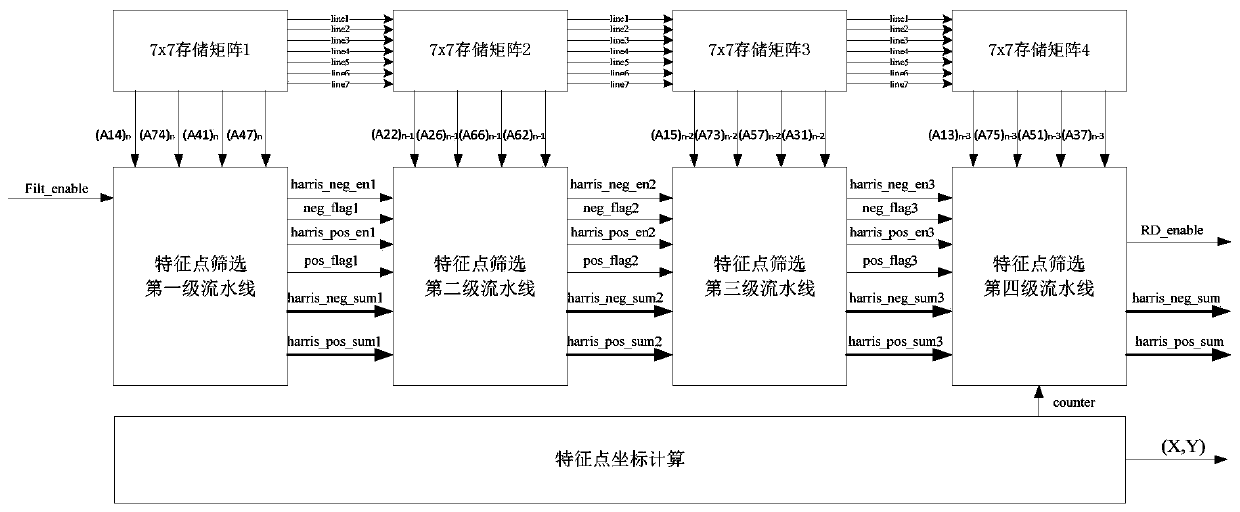
PendingCN111583093AImprove throughputProcessing speedImage analysisImage memory managementComputer hardwareData stream
The invention discloses a hardware implementation method for ORB feature point extraction with good real-time performance. The hardware implementation method for ORB feature point extraction with goodreal-time performance mainly solves the problems that in an existing visual SLAM system, feature point extraction consumes long time, and image matching efficiency is low. According to the implementation scheme, the method comprises the steps that 1, constructing an image feature point screening four-level assembly line; 2, constructing a feature point main direction angle calculation 11-level pipeline architecture; 3, obtaining the gradient direction of the feature points by using the gray centroid of the image block, and performing Gaussian sampling according to the sampling coordinates ofthe main direction rotation descriptor; and 4, designing a two-stage synchronous linear shift buffer structure and an inter-module data stream transmission structure; the method has the advantages ofhigh image processing speed, high accuracy, high platform portability and the like, and can be used in a real-time visual SLAM system to expand the application scene of the SLAM system.
Owner:XI AN JIAOTONG UNIV
Multiple-scale quantum harmonic oscillator multi-mode function optimization system and method
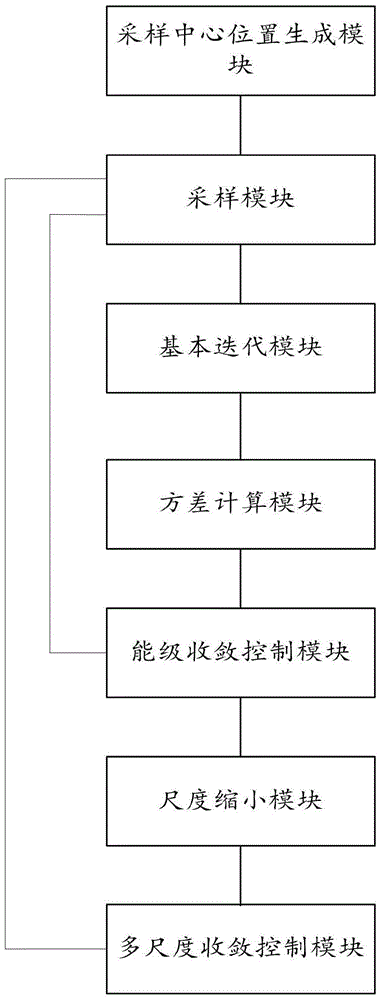
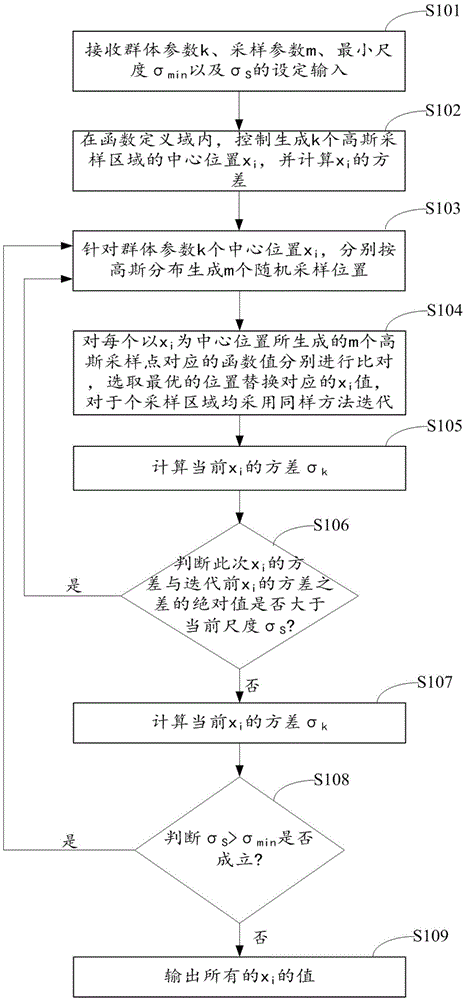
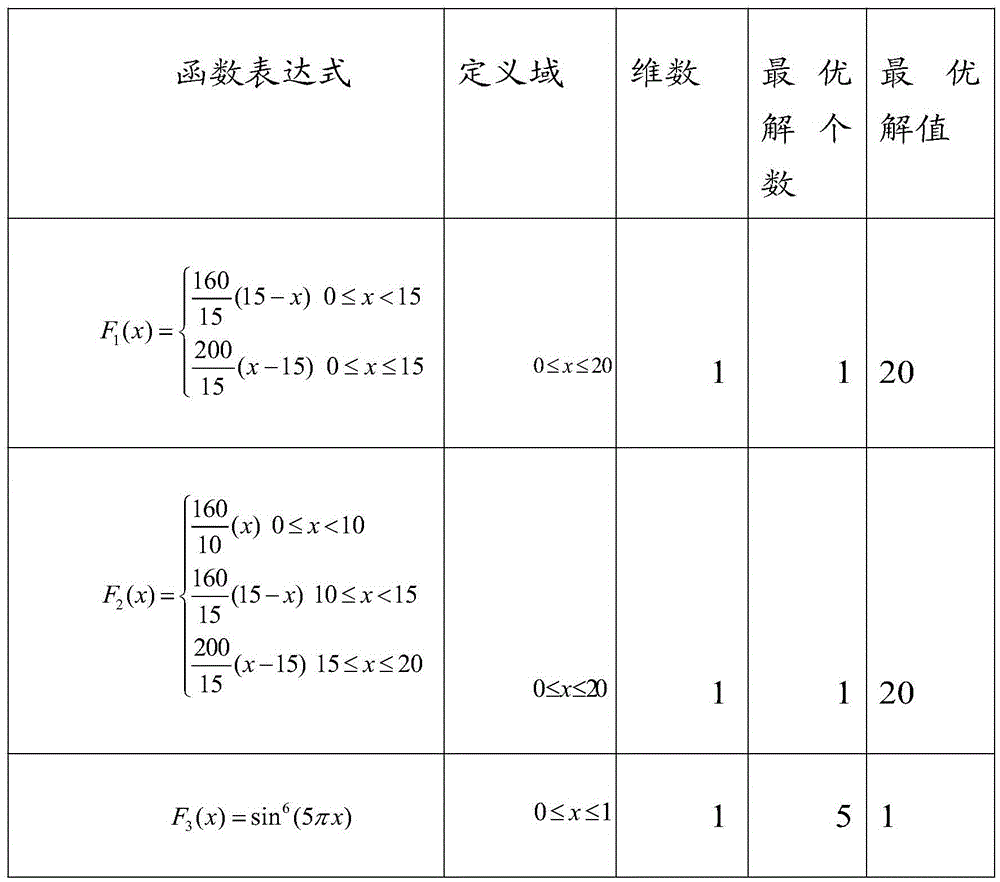
InactiveCN105550787AImplement searchAchieve optimizationForecastingFunction optimizationQuantum harmonic oscillator
The invention relates to the calculation intelligent field and particularly relates to a multiple-scale quantum harmonic oscillator multi-mode function optimization system and a method. The invention improves the optimal position selection strategy of the current MQHOA method, all gauss sampling areas perform comparison on function values by targeting the sampling points generated by itself and the position of the optimal value is reserved as a new gauss sampling center. In the meantime, the convergence condition of the innermost loop is changed to the condition where the difference of the variance of all gauss sampling center positions between two iterations is smaller or equal to the current scale, and the QHO (quantum harmonic oscillator iteration ) performs internal layer circulation convergence. In the invention, the essence of the QHO convergence condition is to perform convergence when the change of each gauss sampling area position is small. The invention can realize the optimization problem of the complex function of the multi-global optimal position. For the complex functions having the multi-global optimal position, the method disclosed by the invention can perform convergence in most of time and thus realizes the search for the multiple global optimal positions.
Owner:SOUTHWEST UNIVERSITY FOR NATIONALITIES
Motion direction change-based candidate seed point cloud single target tracking method
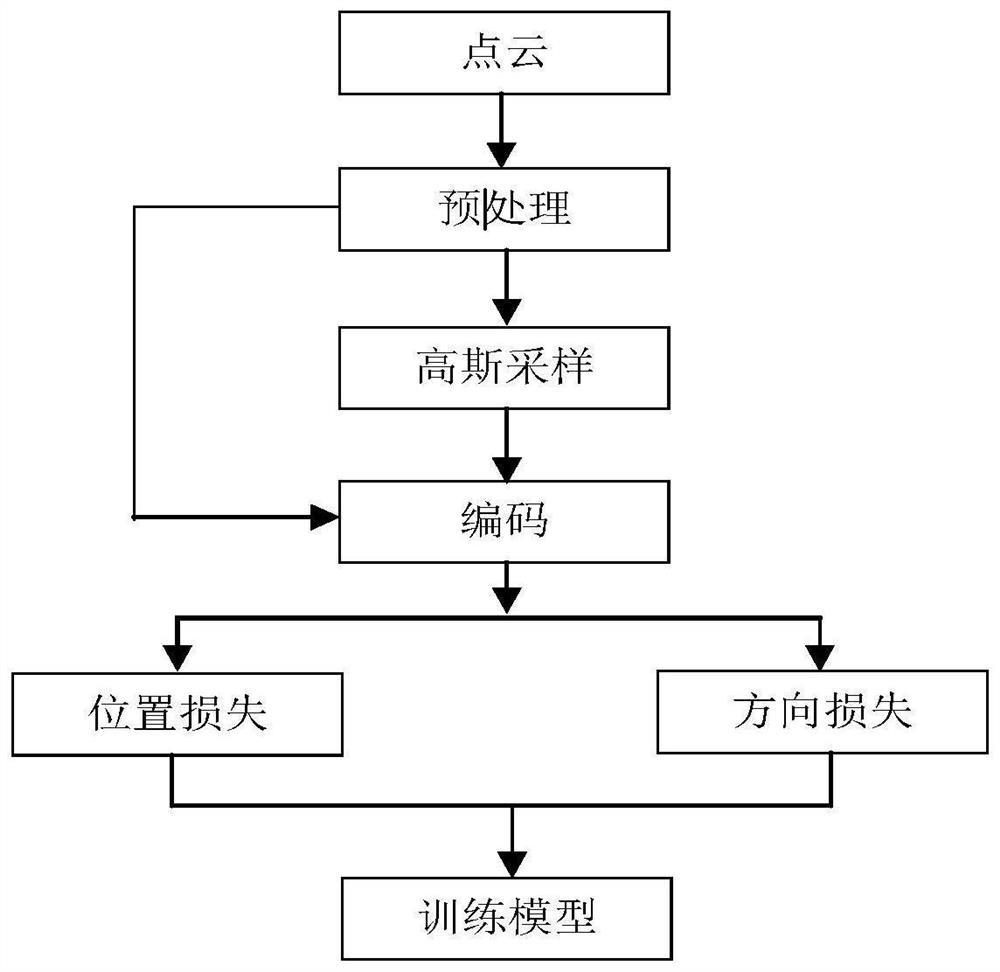
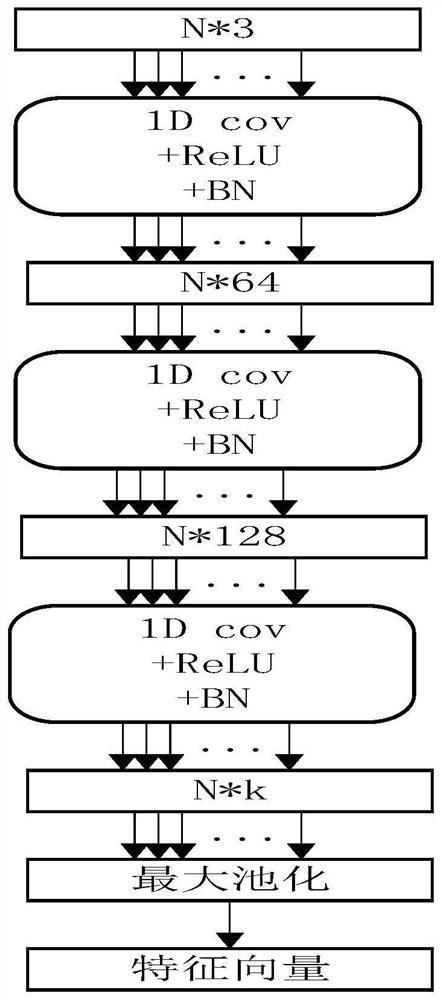
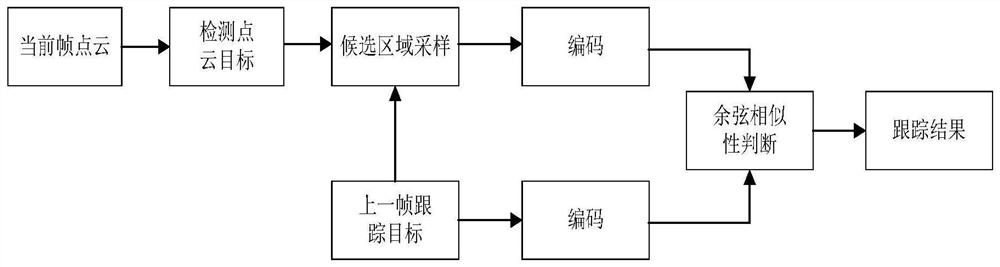
ActiveCN113177969AImprove the evaluation indexPrevent false trackingImage enhancementImage analysisCosine similarityFeature vector
The invention discloses a motion direction change-based candidate seed point cloud single target tracking method, which comprises a training module and a test module, and is characterized in that the training module firstly preprocesses point cloud to obtain template point cloud, then uses Gaussian sampling to obtain candidate point cloud, and then inputs the template point cloud and the candidate point cloud into an encoder for encoding, a corresponding feature vector is obtained, a distance loss function and a direction loss function are calculated, and the whole model is trained. The test module firstly uses a pre-trained PointRcnn model to carry out target detection, then carries out candidate area sampling, then inputs sampled candidate point cloud and tracking target point cloud of a previous frame into the trained model to carry out coding, and finally carries out target tracking on a coded feature vector by using cosine similarity comparison. According to the method, the single-target tracking precision can be improved, and a wrong tracking phenomenon can be effectively prevented.
Owner:HARBIN ENG UNIV
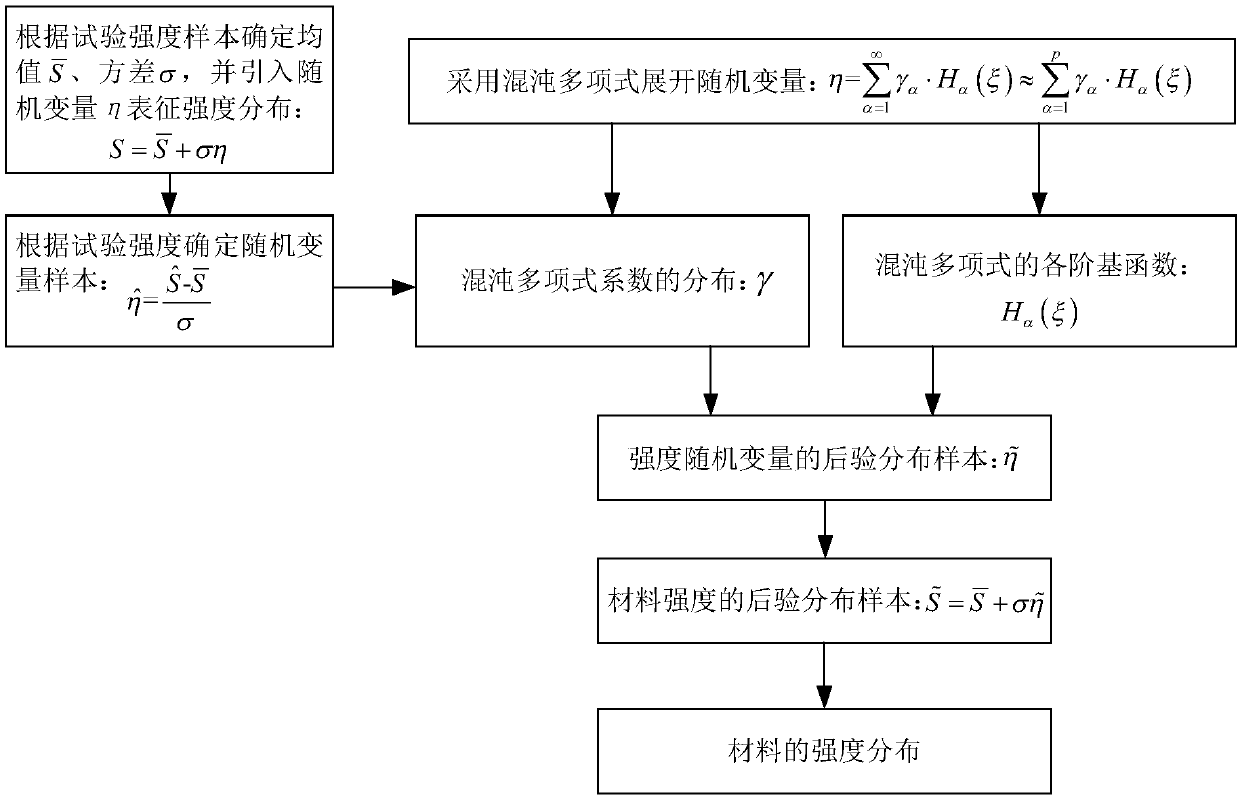
Material strength distribution obtaining method
ActiveCN108491606ASave test timeSave moneyGeometric CADDesign optimisation/simulationTested timeUltimate tensile strength
The invention provides a material strength distribution obtaining method. The method comprises the steps of obtaining multiple material strength samples defined in the specification through a materialstrength test, and determining test data-based strength random variable samples defined in the specification; expanding a strength random variable eta by adopting a chaotic polynomial, and accordingto Gaussian sampling, performing calculation to obtain all-order chaotic polynomial basis function samples defined in the specification; by adopting a Markov chain-Monte Carlo algorithm, obtaining posteriori distribution samples, defined in the specification, of all-order chaotic polynomial coefficients gamma; according to the reconstructed chaotic polynomial coefficient samples defined in the specification and the chaotic polynomial basis function samples defined in the specification, determining posteriori distribution samples, defined in the specification, of the strength random variable; and according to the posteriori distribution samples, defined in the specification, of the strength random variable, calculating posteriori distribution samples, defined in the specification, of strength, and finally obtaining material strength distribution by adopting an interval statistics method. According to the method, the material strength distribution can be obtained by only finishing few strength tests, without assuming a material strength distribution type, so that a large amount of test time and expenditures are saved, and meanwhile, an error caused by wrong selection of a material strength distribution model is avoided.
Owner:SOUTHEAST UNIV
Digital media protection text steganography method based on variational automatic encoder
PendingCN113987129AAchieving visual indistinguishabilityAchieving statistical indistinguishabilitySemantic analysisNeural architecturesPattern recognitionNetwork model
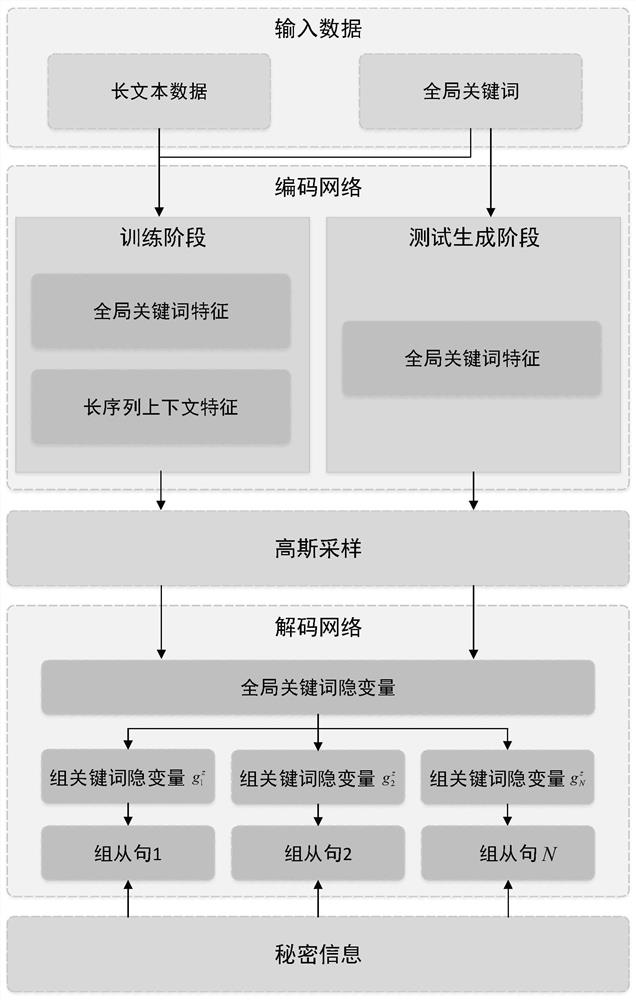
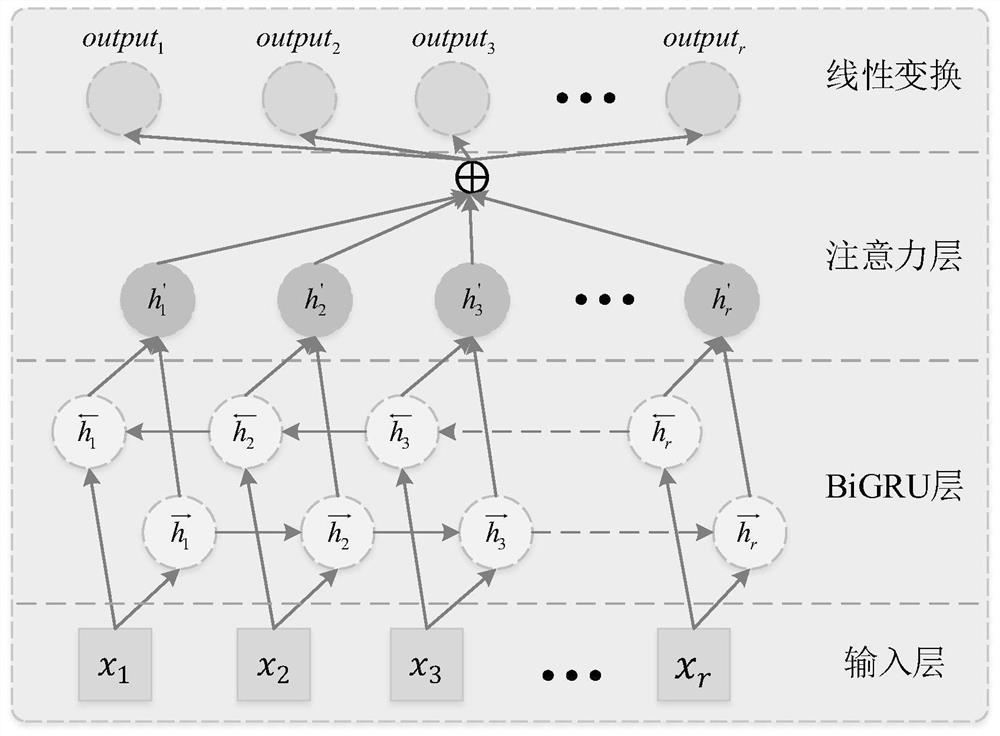
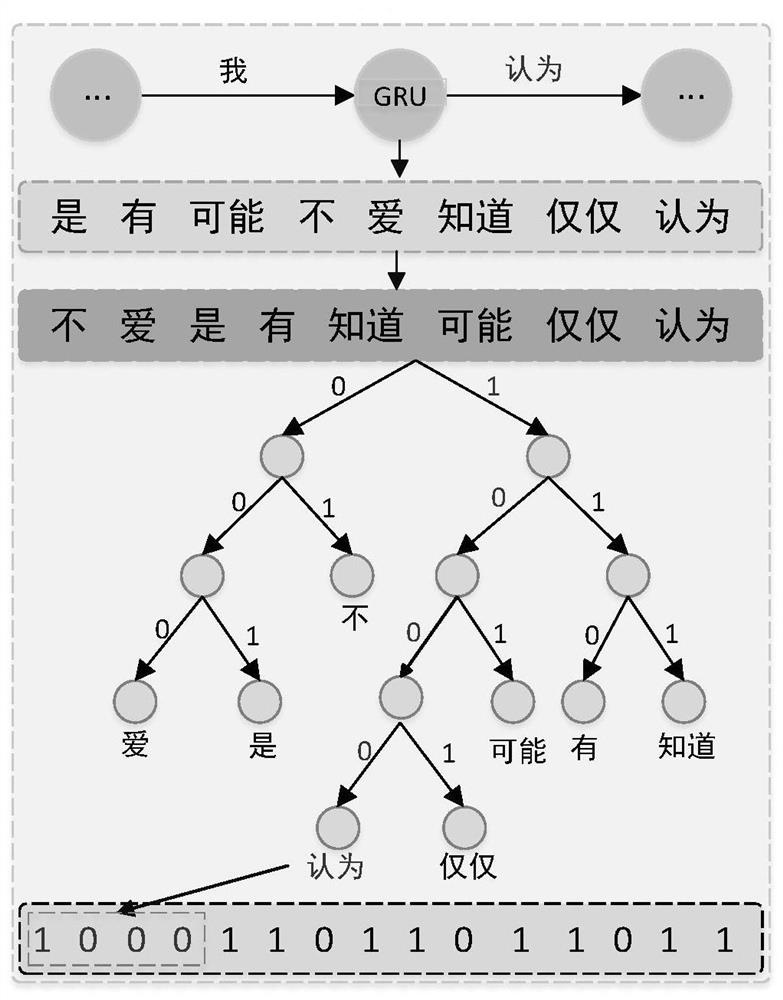
The invention belongs to the field of information security, and particularly relates to a digital media protection text steganography method based on a variational automatic encoder. The method comprises the following steps: constructing a neural network model consisting of an encoding network, Gaussian sampling and a decoding network, and vectorizing a text; utilizing the encoding network to respectively obtain features of global keywords and a long sequence, and fusing the features of the global keyword and the long sequence to obtain global feature representation; carrying out Gaussian sampling on the global feature representation in the encoding network by using Gaussian sampling; decoding a sampling result of Gaussian sampling by using the decoding network to obtain conditional probability distribution of the text; selecting k words with the maximum conditional probability, selecting a word corresponding to a secret bit stream through Huffman coding, and completing steganography of a file. According to the method, long and diverse steganographic texts can be generated, so that the steganographic texts can carry more secret information, and visual indistinguishability, statistical indistinguishability, and semantic indistinguishability of natural languages and the steganographic texts are realized.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Fast 3D path planning method for underwater robot based on goal-oriented centralized optimization
ActiveCN110196602BReduce randomnessQuality improvementPosition/course control in three dimensionsPathPingSimulation
The invention discloses a fast underwater robot three-dimensional path planning method with target-oriented centralized optimization. A target-oriented Gaussian sampling strategy is introduced in an RRT* path planning method, thereby reducing the randomness of sampling points when underwater obstacle distribution is scarce; random disturbance is combined for sampling, a random tree can be reasonably away from an obstacle area, falling into the local minimum is avoided, and search is quickly orientated to the target; and a centralized optimization search strategy is used to perform path optimization processing on the initial path acquired in the invention, the optimization convergence rate and the path quality are improved, and progressive optimization is realized. Compared with the traditional RRT* method, the improved method disclosed in the invention plans a better initial path, the path optimization speed is quicker, and consumption of time and memory is greatly reduced.
Owner:HOHAI UNIV
Vehicle Path Planning Method Using Cross Gravity Search
ActiveCN107462255BFast convergenceImprove efficiencyInstruments for road network navigationSimulationGravitational search algorithm
The invention discloses a vehicle path planning method using cross gravity search. The invention adopts the cross-gravity search algorithm to realize the planning of the vehicle transportation path. In the cross-gravity search algorithm, the position update operation operator of the basic gravity search algorithm is executed with a certain probability, and the Gaussian sampling operation operator based on the current optimal individual is executed with a certain probability, so as to speed up the convergence speed of the algorithm and improve Efficiency of vehicle path planning. The invention can greatly accelerate the convergence speed of the traditional gravitational search algorithm and improve the efficiency of vehicle path planning.
Owner:JIANGXI UNIV OF SCI & TECH
A method and device for analyzing double doublet double peaks in nuclear magnetic resonance spectrum
ActiveCN106290444BFix the flaws in parsingAnalysis saves time and effortAnalysis using nuclear magnetic resonanceNMR - Nuclear magnetic resonanceConfocal
The invention discloses a method and device for analyzing doublets of double doublets (ddd) containing a complicated coupling mode in analysis to a compound structure by using a nuclear magnetic resonance spectrum. The method comprises the following steps: treating each acquired doublet of double doublets in a compound nuclear magnetic resonance spectrum into four identical doublets on the basis of a lorenz curve; carrying out Gaussian sampling to obtain accurate chemical transfer of each doublets; and finally calculating to obtain coupling constants. In the method, the lorenz curve is taken as a basis, the doublets are established at first, then ddd peak coupling constants are automatically sampled in a preset section by a Bayesian model, accurate curves and coupling constants are obtained, finally, parameter information of a ddd peak in a compound nuclear magnetic resonance structure is filled, and the shortcomings of analysis to the nuclear magnetic resonance structure of a compound containing a ddd peak in the prior art are overcome.
Owner:郝洁 +1
System and method for joint detection and tracking of weak and small targets based on random finite sets
ActiveCN112215146BReduce computational complexityEffective trackingScene recognitionAlgorithmSmall target
The present invention provides a weak and small target joint detection and tracking system and method based on random finite sets, including an infrared image measurement module, which is used to obtain infrared measurement images of the ground environment and targets, thereby obtaining target measurement domains; target prediction The module is used to calculate the target measurement domain to obtain the predicted state of the target and the predicted track label of the target, and then perform Gaussian sampling; the target update module is used to calculate the likelihood function, and calculate the updated state of the target according to the likelihood function Update the track label with the target; and establish a hypothetical cost function associated with the target and measurement, select the hypothesis corresponding to the maximum weight according to the hypothetical weight, and obtain the target state and track estimated value at the current moment. The invention provides the basis of acquiring target infrared measurement in a complex environment, through measurement difference, self-adaptive extraction of newborn targets, and optimal allocation of track, to realize effective detection and tracking of weak and small infrared targets in a complex noise environment .
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com