Web application program bug detection method based on simulated strike
A vulnerability detection and simulated attack technology, applied in the field of vulnerability detection, can solve problems such as dangerous security risks and dangers, and achieve the effects of high operation efficiency, comprehensive and accurate security detection, and intuitive detection reports and analysis reports.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
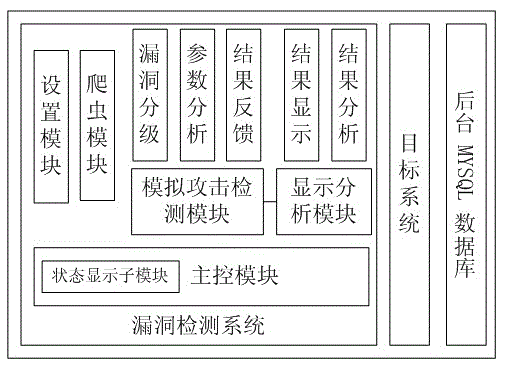
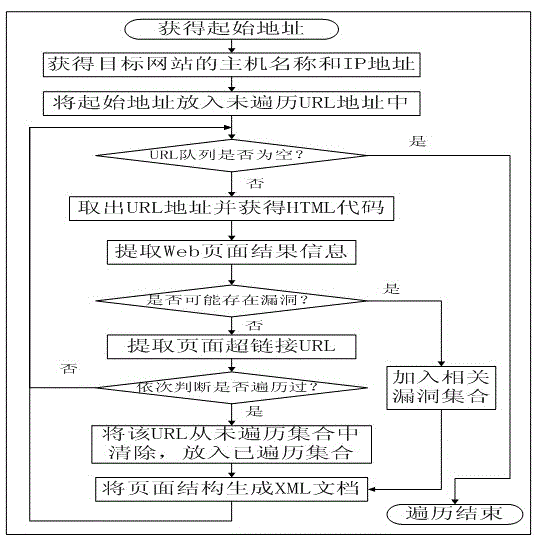
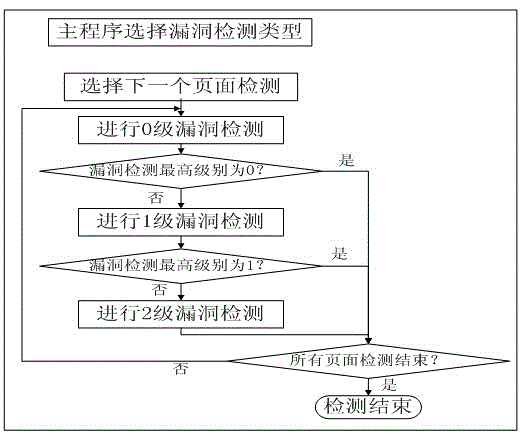
[0021] figure 1 It is a structural diagram of the Web application vulnerability detection system, which mainly includes three parts: the vulnerability detection system, the target system and the background database. The vulnerability detection system includes a control module, a setting module, a crawler module, a simulated attack detection module and a display analysis module, which are respectively used to complete the functions of overall control, detection setting, Web page crawler and structure extraction, simulated attack and display analysis. The target system includes six common web application vulnerabilities, namely SQL injection vulnerability, dynamic execution vulnerability, unsafe direct object reference vulnerability, remote file inclusion vulnerability, file upload vulnerability and path traversal vulnerability. The vulnerability detecti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com