Identity authentication method for accessing SIP security video monitoring system
A video surveillance system and identity authentication technology, which is applied in the field of identity authentication for accessing SIP security video surveillance systems, can solve problems such as network security risks and security defects, achieve safe and efficient authentication, and ensure the effect of network access security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0106] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
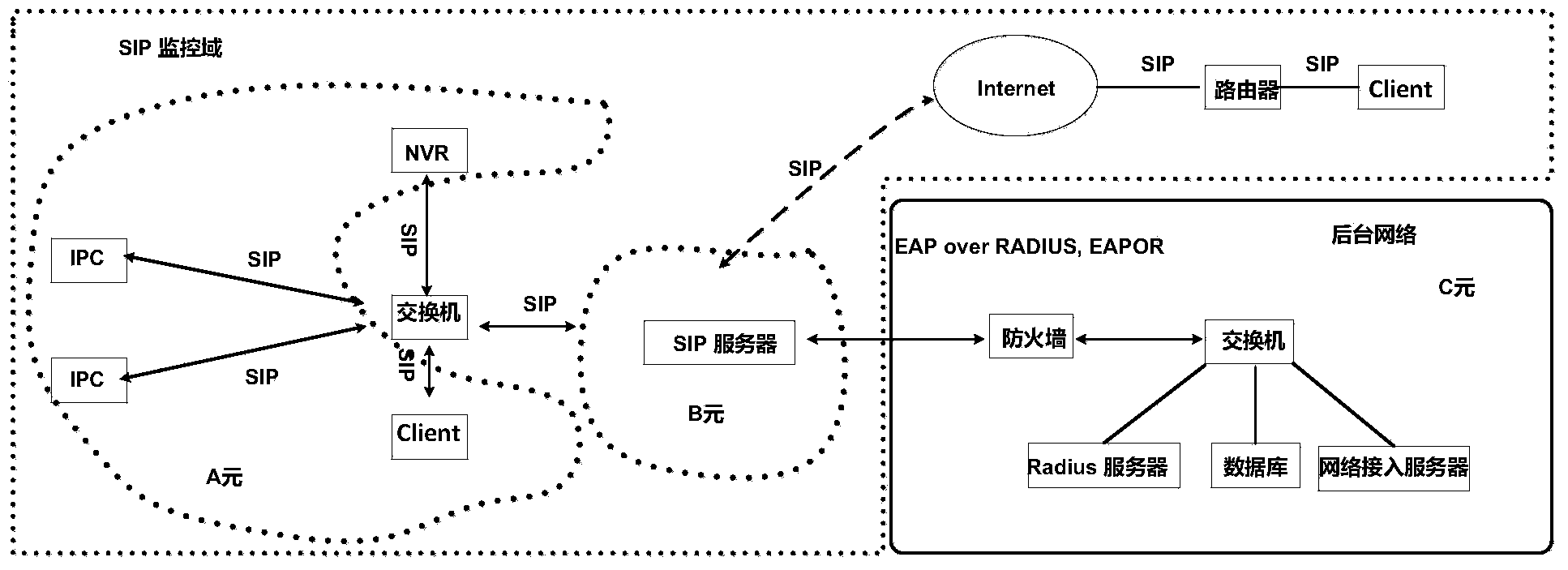
[0107] like figure 1 As shown, three network elements (A, B, and C elements) in the network are set, and each element corresponds to a type of network entity in the network. The explanation is as follows:
[0108] A element --- SIP terminal (SIP camera IPC supporting SIP protocol, SIP network hard disk video recorder NVR, SIP user client client), that is, a camera supporting SIP signaling protocol, network hard disk video recorder and user client, because the SIP terminal Both run the core program required by the SIP session, that is, the SIP User Agent (SIP User Agent, SIP UA) program. Therefore, in this patent, the SIP terminal is equivalent to the SIP UA, and both the SIP terminal and the SIP UA are relative to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com