Safety storage system and safety storage method for distributed files
A distributed file and secure storage technology, applied in the field of distributed file secure storage system, can solve the problems of system file insecurity, loss, wrong change, etc., achieve high fault tolerance and reduce loss effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
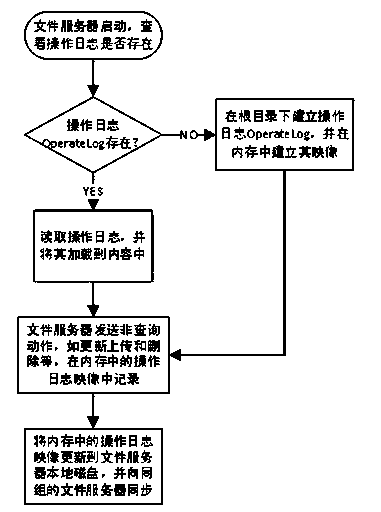
[0052] A highly fault-tolerant distributed file security storage system, including: a client end, which completes operations such as consulting, modifying, deleting, and saving files; an analysis server, which completes file encryption, decryption, and path orientation; file storage.
[0053] A highly fault-tolerant distributed file security storage method based on the above-mentioned security storage system, the specific method steps are:
[0054] A. The operation log records the operations of the file server on file content changes, including upload, update, and delete operations;
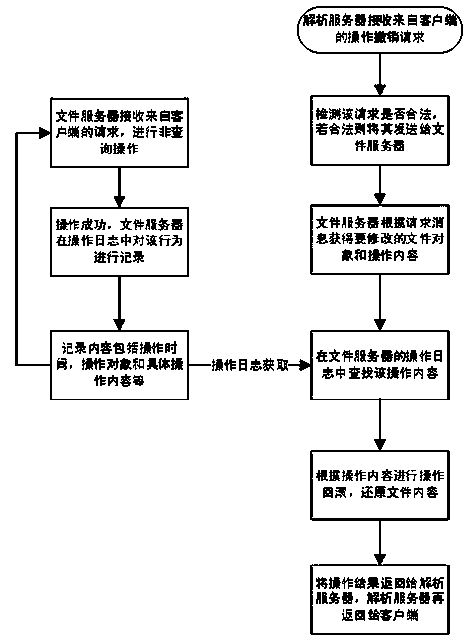
[0055] B. For errors caused by accidental file changes, the user makes a recovery request, and the system rolls back the operation through the log records to correct the errors.
[0056] Correct the wrong operation or roll back the operation to avoid or reduce the loss caused by it and achieve high fault tolerance of the system.
[0057] The steps further include: after receiving the recovery r...
specific Embodiment 2
[0071] Based on the distributed file secure storage method of the secure storage system in the specific embodiment one, the specific method steps are:
[0072] 1. The operation log records the operation of the file server FileSerDel on changing the content of the file, including uploading, updating and deleting;
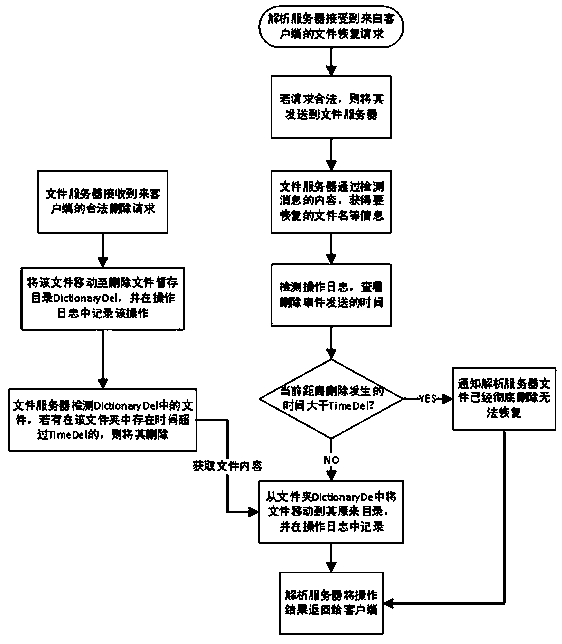
[0073] 2. For files deleted by users, retrieve them through operation logs and file deletion backups.
[0074] Retrieve accidentally deleted files, avoid or mitigate the losses caused by them, and achieve high fault tolerance of the system.
[0075] like image 3 As shown, the steps further include: after the parsing server receives the retrieval request from the user, after judging that the request is legal, the request is passed to the file server that previously stored the file. For example, it is necessary to determine whether there is permission for the retrieval request to avoid leakage of documents.
[0076] In this specific embodiment, the file server in s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com