Access control verification method and system
A verification method and verification system technology, applied in the field of access control and unlocking, can solve the problems of low cost, high cost, low accuracy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 4 example
[0090] see Figure 4 , is the flow chart of the fourth embodiment of the access control verification method of the present invention;
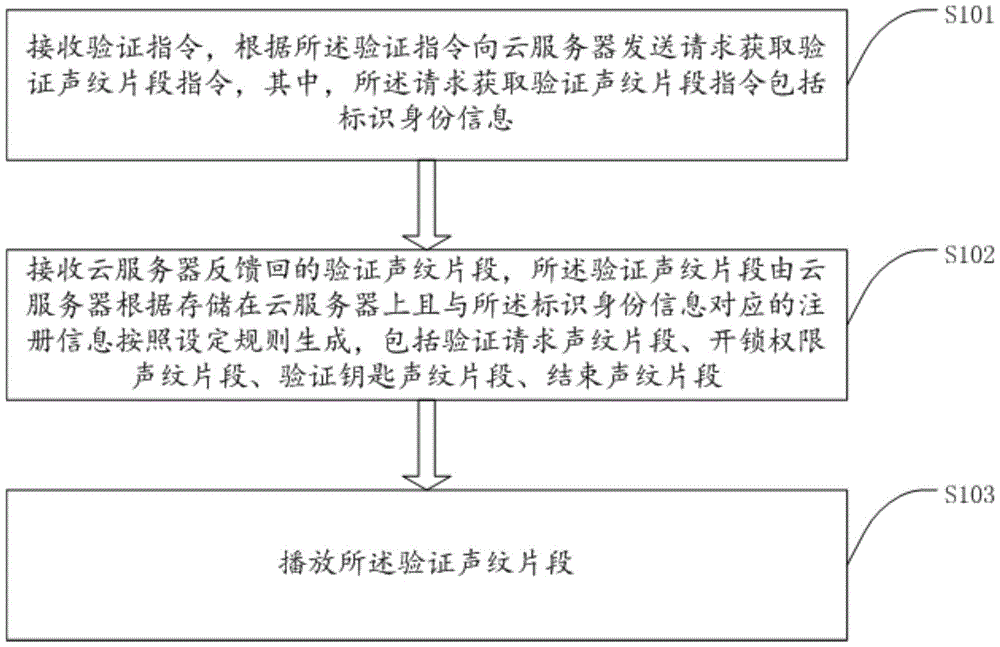
[0091] Step 401: The mobile client receives the verification instruction, connects to the cloud server according to the verification instruction, and requests to obtain the verification voiceprint segment;
[0092] Step 402: The cloud server uses the registration information stored in the cloud server and corresponding to the identification information of the mobile client to generate a verification voiceprint segment according to the set rules and send it to the mobile client;
[0093] Step 403: The mobile client receives and plays the verification voiceprint segment to the access control device;
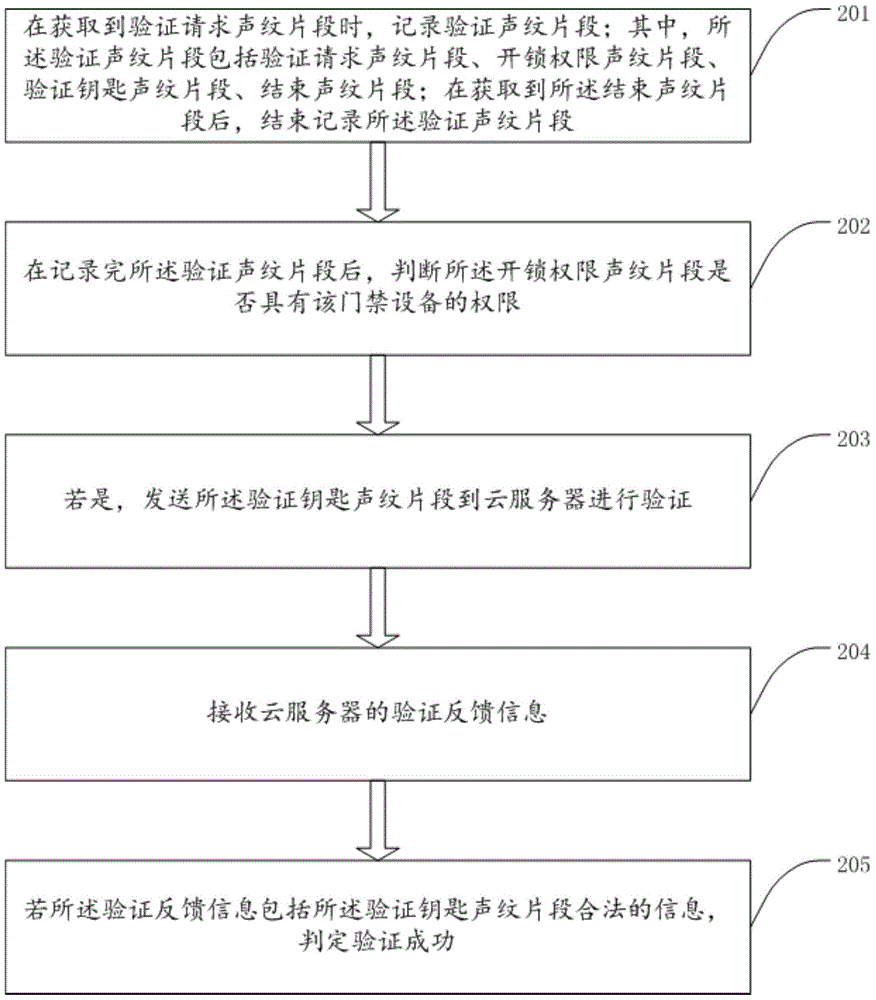
[0094] Step 404: The access control device side records and verifies the voiceprint segment;
[0095] Step 405: The access control device side judges whether the unlocking authority voiceprint segment in the verified voiceprint segment has the au...
no. 1 example
[0102] According to above-mentioned a kind of access control verification method, the scheme of the present invention also provides access control verification system, please refer to Figure 5 , is a structural diagram of the first embodiment of the access control verification system of the present invention;
[0103] An access control request verification system includes a mobile client, and the mobile client includes a receiving instruction unit 10, an information transceiving unit 11, and a playing unit 12;
[0104] The receiving instruction unit 10 receives a verification instruction, and the information transceiving unit 11 sends a request to obtain a verification voiceprint segment instruction to the cloud server according to the verification instruction, wherein the request to obtain a verification voiceprint segment instruction includes identification information;
[0105] The information transceiving unit 11 receives the verification voiceprint segment fed back by the ...
no. 3 example
[0129] see Figure 7 , is a structural diagram of the third embodiment of the access control verification system of the present invention;
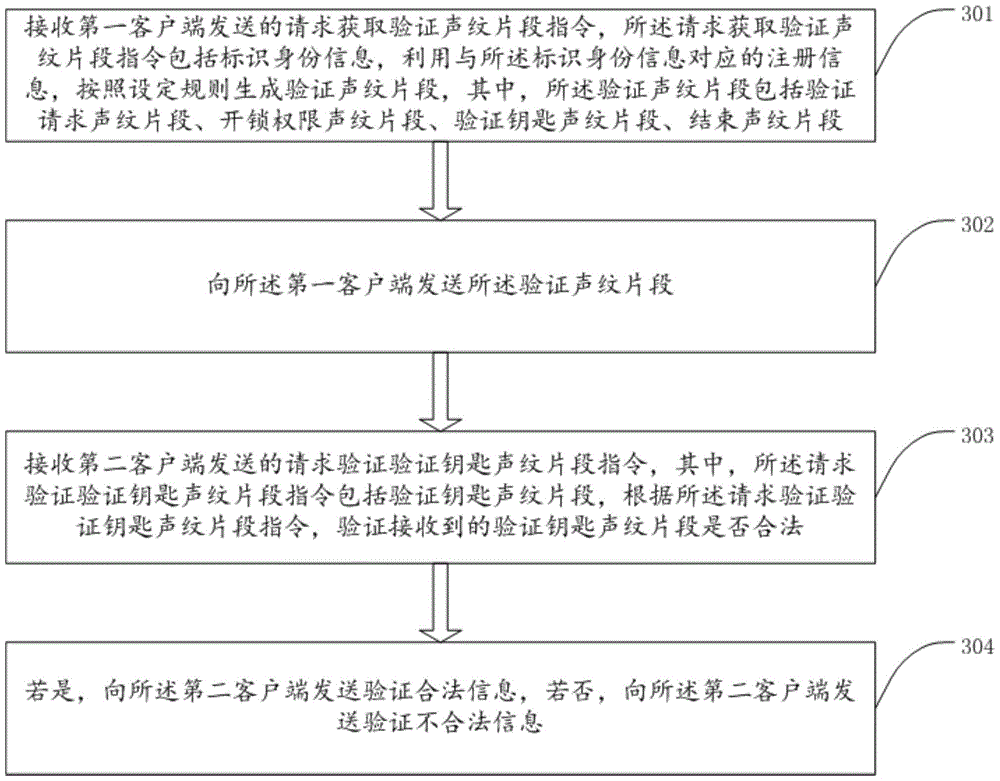
[0130] An access control verification system includes a cloud server, and the cloud server includes a second receiving unit 30, a generating unit 31, a second sending unit 32, and a verification legal unit 33;
[0131] The second receiving unit 30 receives the request to obtain the verification voiceprint fragment instruction sent by the first client, and the request to obtain the verification voiceprint fragment instruction includes identification information; receives the request verification verification key voiceprint fragment sent by the second client Instructions, the request to verify and verify the key voiceprint fragment instruction includes verifying the key voiceprint fragment;
[0132] The generating unit 31 uses the registration information corresponding to the identification information to generate verification voiceprint s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com