Login implement method for user terminal to have access to IMS network and IMS
A user terminal and terminal technology, which is applied to electrical components, security devices, transmission systems, etc., can solve the problems that terminals cannot be securely accessed, and there is no solution, so as to reduce account theft and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
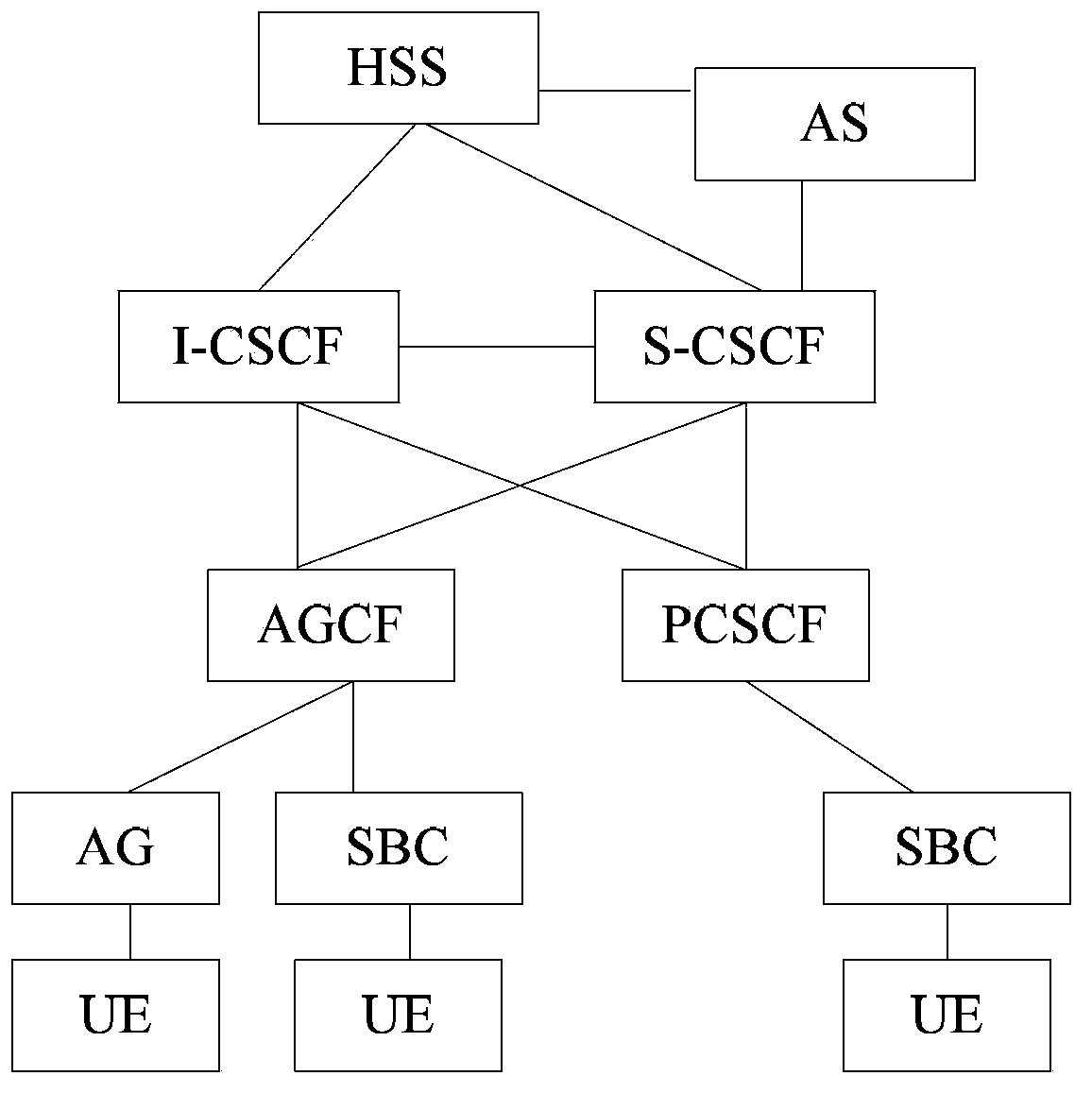
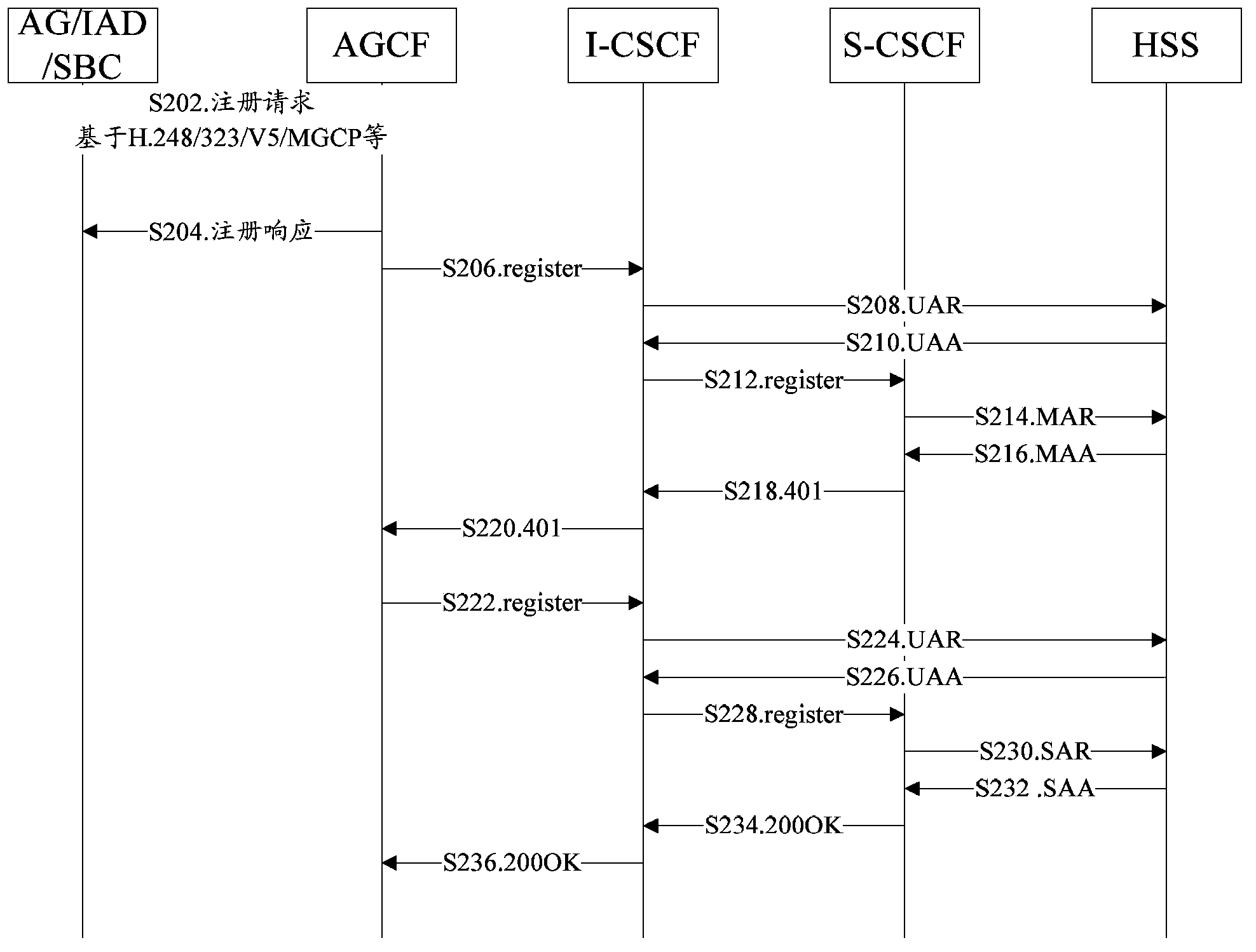
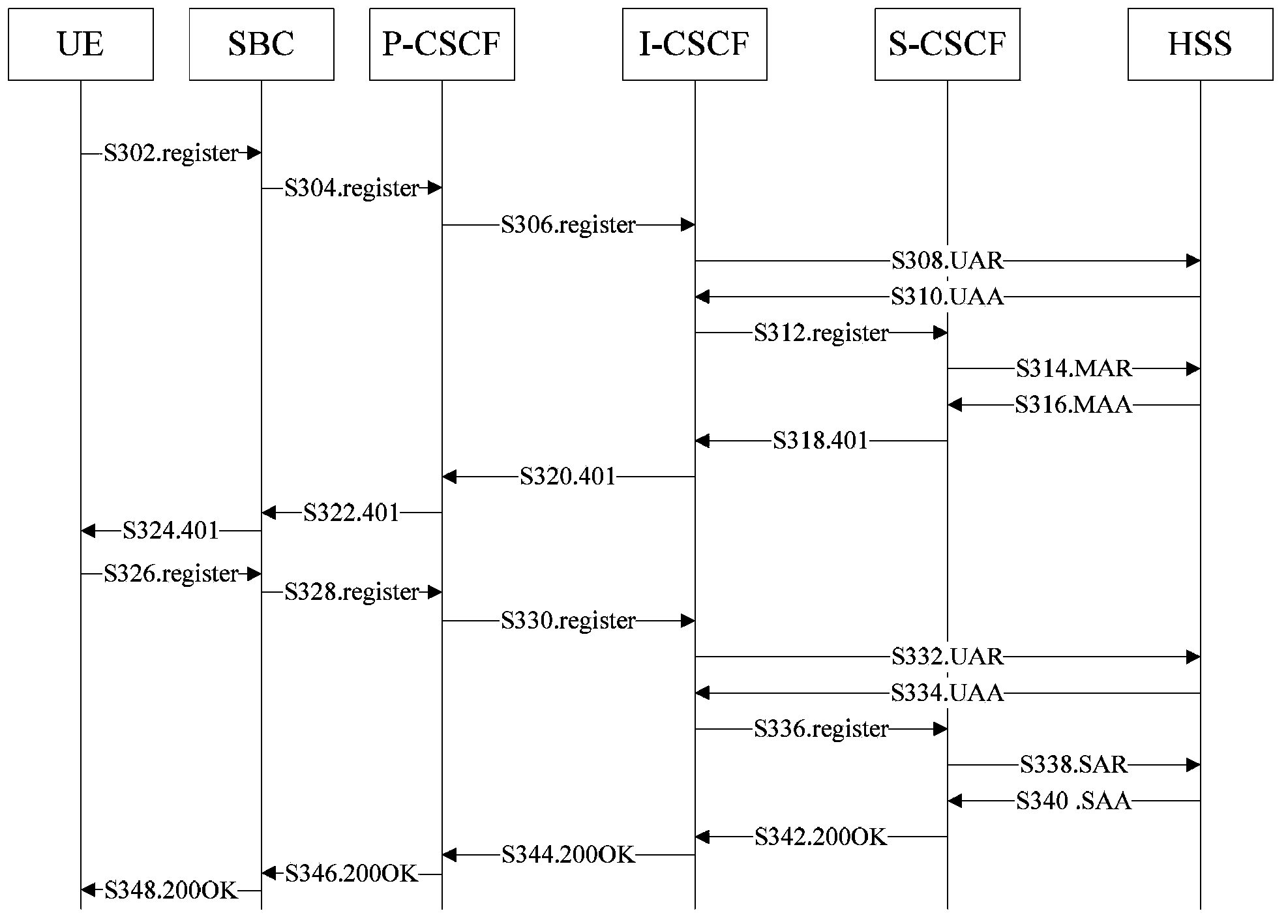
[0056] The main idea of the solution of the embodiment of the present invention is: obtain the registration request message of the access user terminal carrying the registration access address information on the access side, and perform the registration access address information in the access flow of the access user terminal Legality check, if the check is passed, the corresponding normal access process will be carried out; otherwise, the access user terminal registration will be refused, so in the user registration process, the joint authentication of "user + key + access address" will be used, In order to improve the security of IMS network.
[0057] The embodiment of the present invention takes into account the user terminals accessing the IMS network. At present, a large part of them are softswitches and public switched telephone network (Public Switched Telephone Network, PSTN) terminals, which belong to old and old equipment, and do not have the ability to use soft and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com