VPN (virtual private network) connection method based on IPSec (internet protocol security)
A connection method and IP address technology, applied in the field of communication, can solve problems such as easy to be cracked, low security, difficult to adapt, etc., to achieve the effect of avoiding low security performance, taking into account security and ease of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
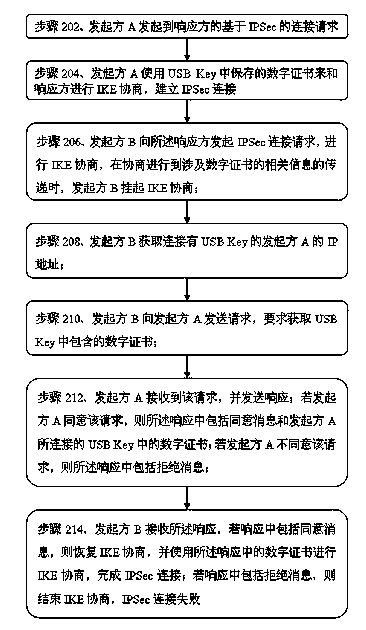
[0020] Embodiment 1 of the present invention provides a VPN connection method based on IPSec, which is characterized in that the network includes an initiator A connected to a USB Key, an initiator B not connected to a USB Key, and a responder, and the USB Key stores Obtain the digital certificate required for IPSec connection, and electrically connect with the initiator device as a third-party device, including the following steps:
[0021] Step 202, the initiator A initiates an IPSec-based connection request to the responder;
[0022] Step 204, the initiator A uses the digital certificate stored in the USB Key to perform IKE negotiation with the responder to establish an IPSec connection;
[0023] Step 206, the initiator B initiates an IPSec connection request to the responder to perform IKE negotiation, and when the negotiation proceeds to the transfer of relevant information related to the digital certificate, the initiator B suspends the IKE negotiation;
[0024] Step 20...
Embodiment 2
[0029] In step 208 of the first embodiment, the specific method for the initiator B to obtain the IP address of the initiator A connected to the USB Key is as follows:
[0030] The initiator B sends a query request to the responder, and the request responder sends the initiator B the IP address information of the initiator connected to the USB Key containing the digital certificate;
[0031] After receiving the query request, the responder finds the initiator A that has connected with itself through IPSec and connected the USB Key containing the digital certificate, and sends the IP address of the initiator A to the initiator B.
[0032] Those of ordinary skill in the art can understand that all or part of the processes in the methods of the above embodiments can be realized by instructing related hardware through a host program, and the program can be stored in a host-readable storage medium, the program During execution, it may include the processes of the embodiments of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com