Service authentication method and system
An authentication method and business technology, applied in the communication field, can solve problems such as easy forgetting, user inconvenience, frequent input of user information, etc., and achieve the effect of improving user experience and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
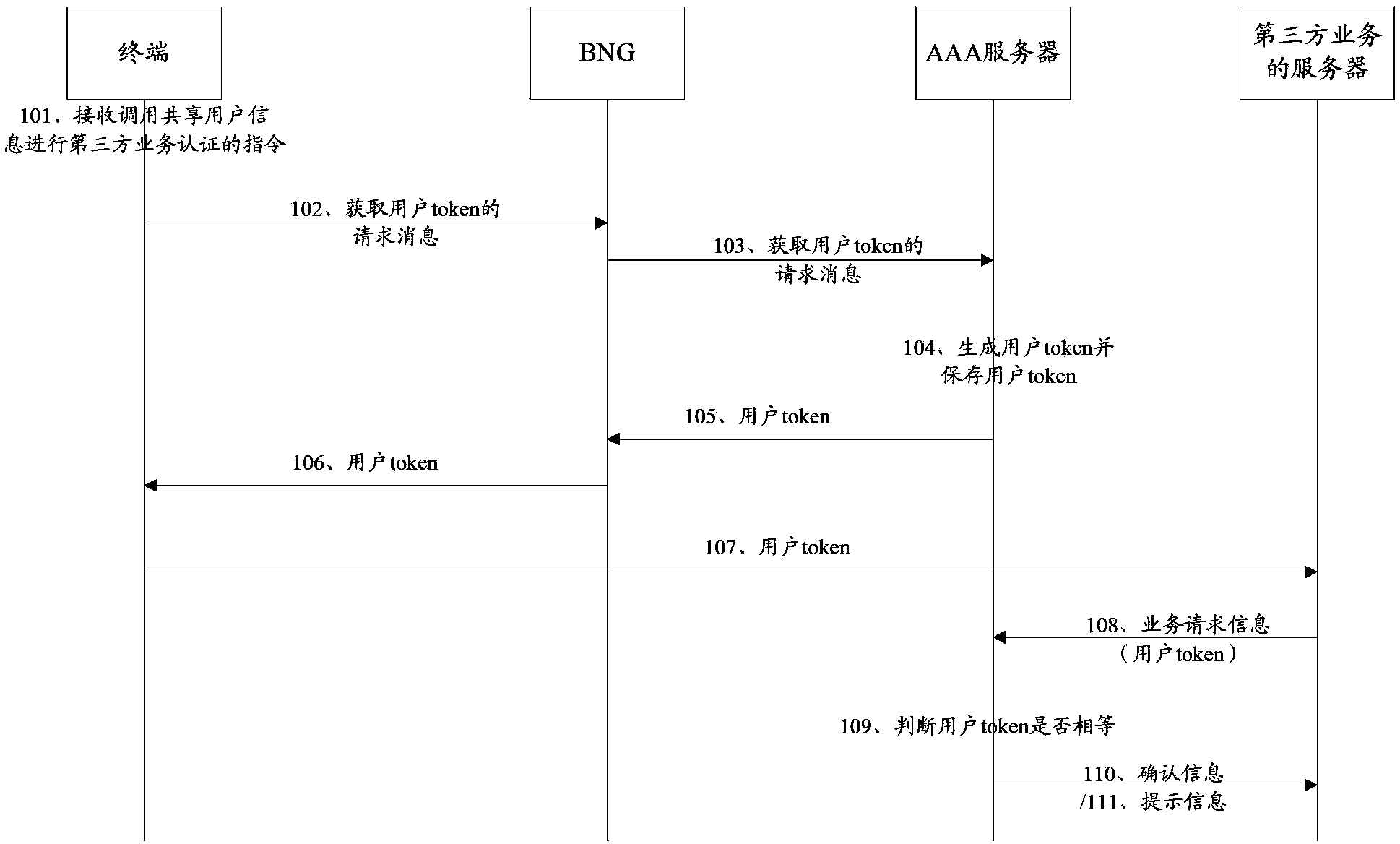
[0061] The present invention provides a service authentication method. The network architecture involved in the method includes: a terminal, a BNG and an AAA server, such as figure 1 As shown, the method includes:
[0062] 101. The terminal receives an instruction to call shared user information for third-party service authentication sent by the user; the above shared user information is the user information used by the user in AAA (Authentication, Authorization, Accounting, authentication, authorization, and accounting) authentication;
[0063] For example, the shared user information can be the account name and password used by the network operator when the user accesses the network. For example, the user uses China Telecom ADSL (Asymmetric Digital Subscriber Line) to dial The account name and password entered when surfing the Internet;
[0064] In this embodiment, if a third-party service provides the function of using shared user information for third-party service authentication...
Embodiment 2
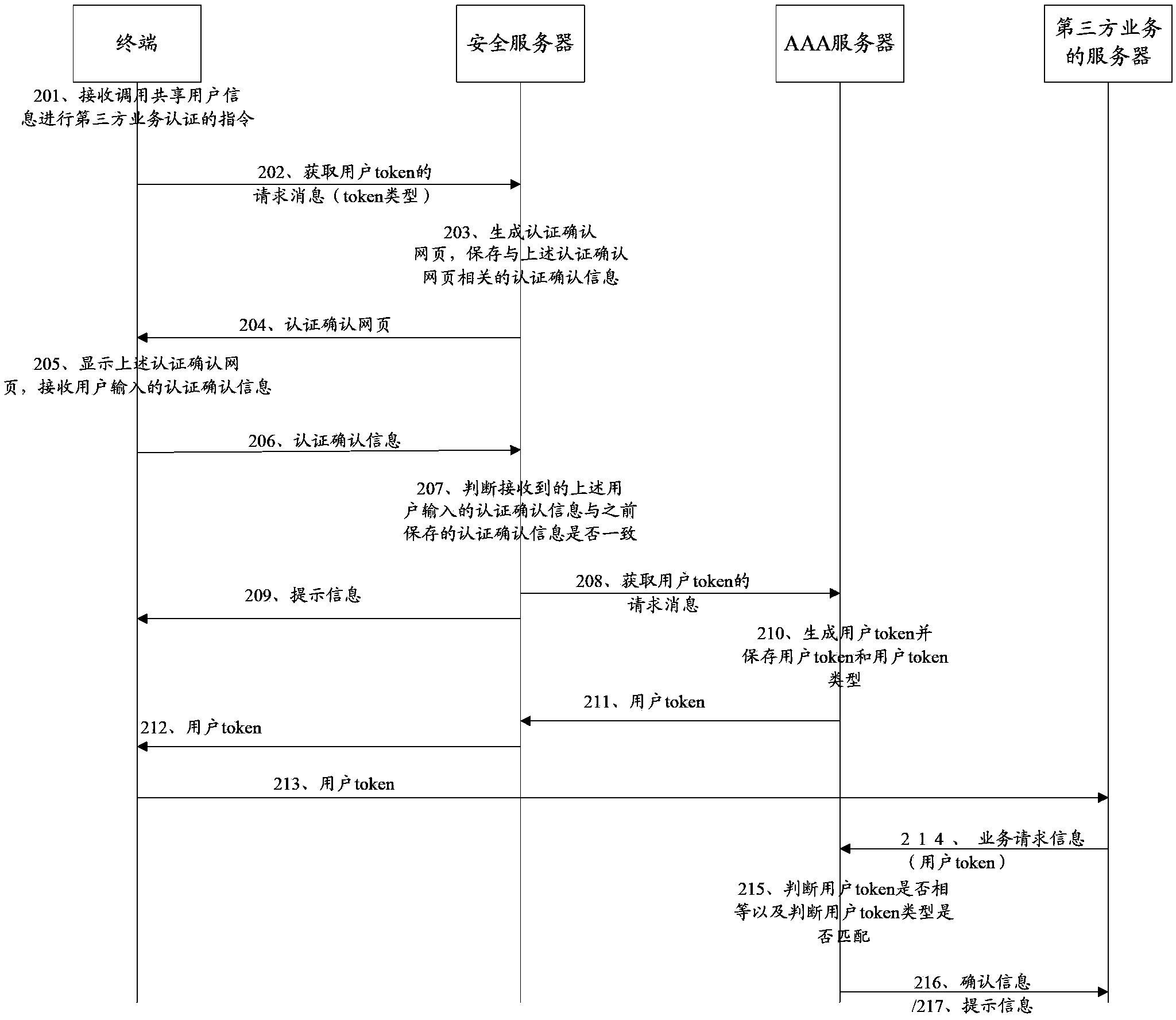
[0094] The present invention also provides a service authentication method. The network architecture involved in the method includes: a terminal, a security server and an AAA server, such as figure 2 As shown, the method includes:
[0095] 201. The terminal receives an instruction to invoke shared user information for third-party service authentication sent by a user; the above shared user information is the user information used by the user when performing AAA authentication;
[0096] For example, the shared user information can be the account name and password used by the network operator when the user accesses the network. For example, the user uses China Telecom ADSL (Asymmetric Digital Subscriber Line) to dial The account name and password entered when surfing the Internet;
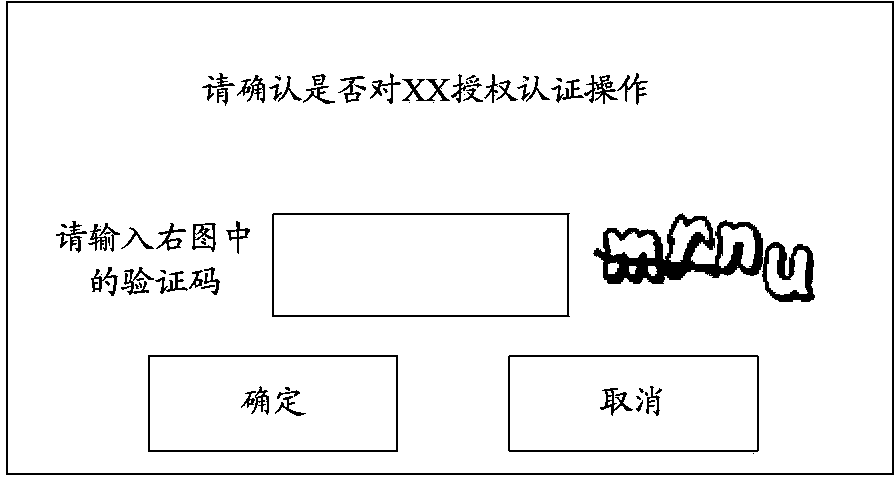
[0097] In this embodiment, if a third-party service provides the function of using shared user information for third-party service authentication, the webpage or interface of the third-party service displa...
Embodiment 3
[0135] The invention also provides a business authentication system, such as Figure 4 As shown, the system may include: a terminal 100, a BNG 200 and an AAA server 300, among which,
[0136] The terminal 100 can be used to receive an instruction sent by a user to invoke shared user information for third-party service authentication; the above shared user information is user information used by the user for authentication, authorization, and accounting AAA authentication; for example, the shared user information can be It is the account name and password entered when the user accesses the network and the network service provided by the network operator, such as the account name and password entered when the user uses China Telecom's ADSL (Asymmetric Digital Subscriber Line) dial-up Internet access; In this embodiment, if a third-party service provides the function of using shared user information for third-party service authentication, the webpage or interface of the third-party s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com