Data traffic control method and system for mobile terminal
A mobile terminal and data traffic technology, applied in the communication field, can solve the problems of traffic consumption, high service billing beyond the monthly traffic, high Internet access fees for users, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
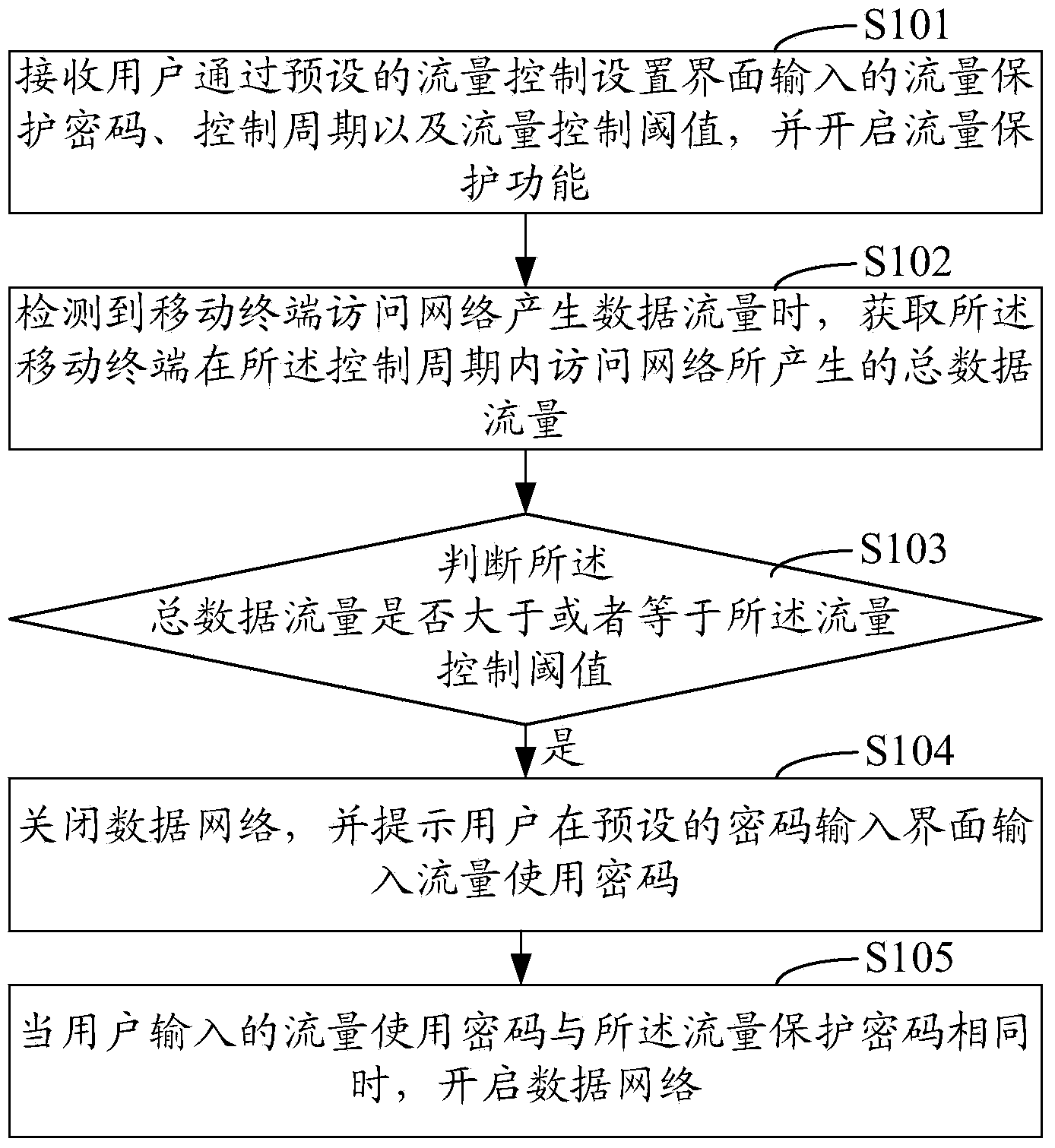
[0029] see figure 1 As shown, it is a schematic flowchart of Embodiment 1 of the data flow control method for a mobile terminal according to the present invention. Such as figure 1 As shown, the data flow control method of the mobile terminal in this embodiment includes the following steps:
[0030] Step S101: Receive the flow protection password, control cycle and flow control threshold input by the user through the preset flow control setting interface, control the mobile terminal to enable the flow protection function, and enter step S102;
[0031] In this embodiment, when the user wants to protect the data flow, so as to prevent other people from using the data flow at will, or to avoid some unnecessary flow consumption caused by some applications on the mobile terminal, data flow control can be performed. ;
[0032] When the user wants to protect the data flow, he can operate the mobile terminal to make the mobile terminal display the preset flow control setting interf...
Embodiment 2
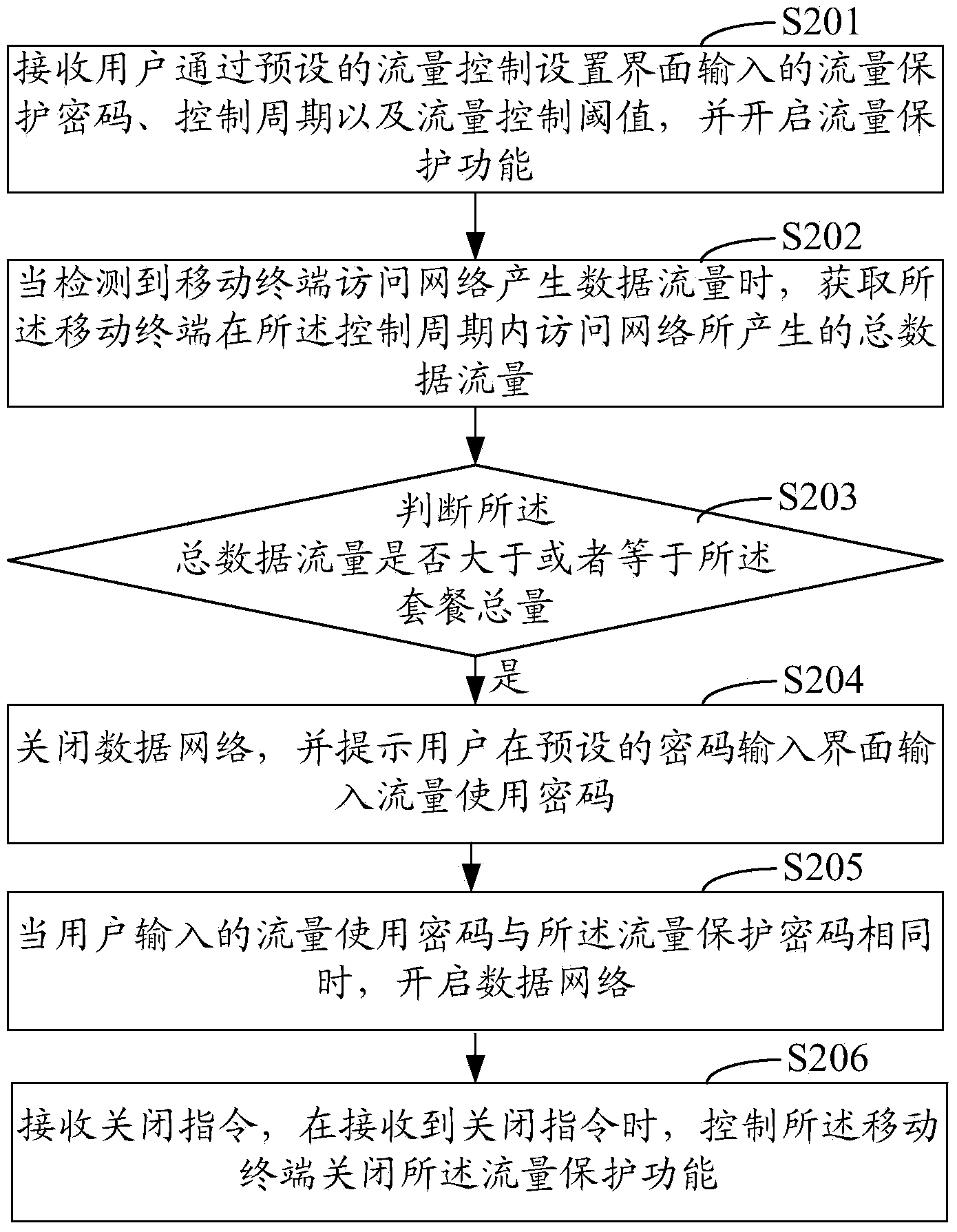
[0048] Such as figure 2 As shown, it is a schematic flowchart of the second embodiment of the data flow control method of the mobile terminal of the present invention. In this embodiment, the difference from the first embodiment mainly lies in that considering that the user may If the data flow is greater than the flow control threshold, it will be necessary to continue to use the data network, and the frequently input flow password will cause inconvenience to the user and reduce the user experience. Therefore, in this embodiment, the function of closing the flow protection function is added. step.
[0049] Such as figure 2 As shown, the data flow control method of the mobile terminal in this embodiment includes the following steps:
[0050] Step S201: Receive the flow protection password, control cycle and flow control threshold input by the user through the preset flow control setting interface, control the mobile terminal to enable the flow protection function, and ente...
Embodiment 3
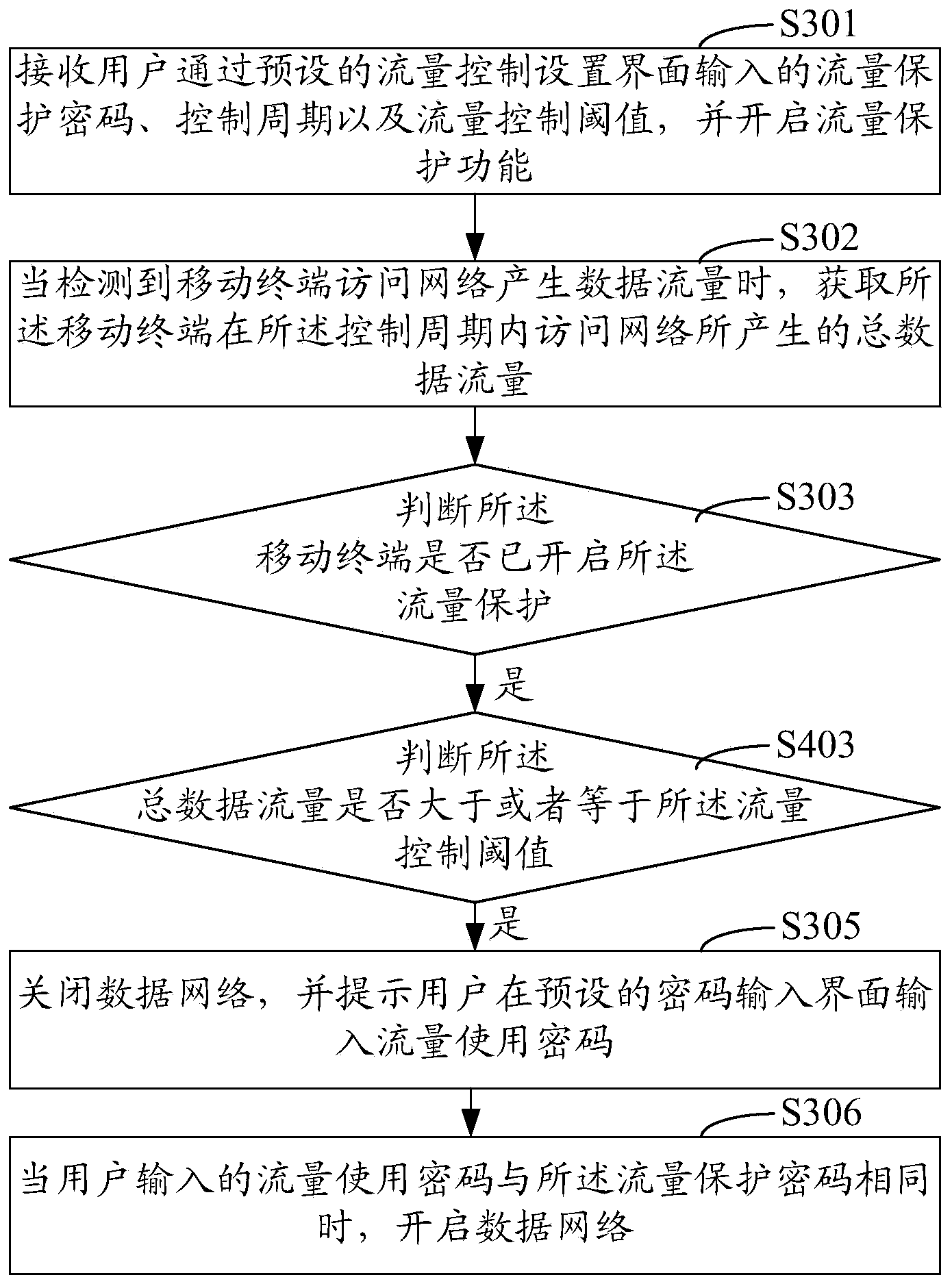
[0059] Such as image 3 As shown, it is a schematic flowchart of the third embodiment of the data flow control method of the mobile terminal according to the present invention. In this embodiment, the main difference from the first embodiment is that the user may close For the traffic protection function of the mobile terminal, a step of detecting whether the traffic protection function is turned off is added.
[0060] Such as image 3 As shown, the data flow control method of the mobile terminal in this embodiment includes the following steps:
[0061] Step S301: Receive the flow protection password, control cycle and flow control threshold input by the user through the preset flow control setting interface, control the mobile terminal to enable the flow protection function, and enter step S302;
[0062] Step S302: When it is detected that the mobile terminal accesses the network to generate data traffic, obtain the total data traffic generated by the mobile terminal access...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com