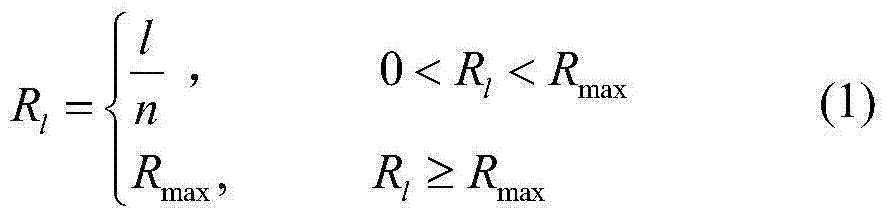Two-dimensional code generation method and application thereof
A technology of two-dimensional code and verification method, which is applied in data processing applications, special data processing applications, collaborative operation devices, etc., can solve time-consuming and labor-intensive problems, achieve high anti-counterfeiting coefficient, improve authenticity and reliability, and improve user experience. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
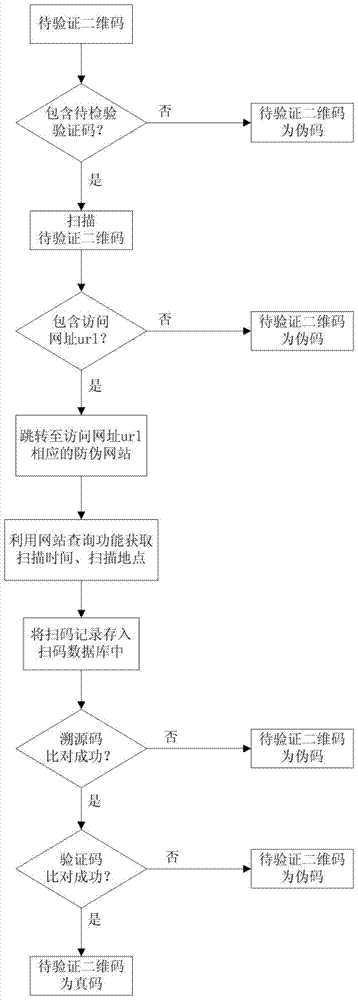
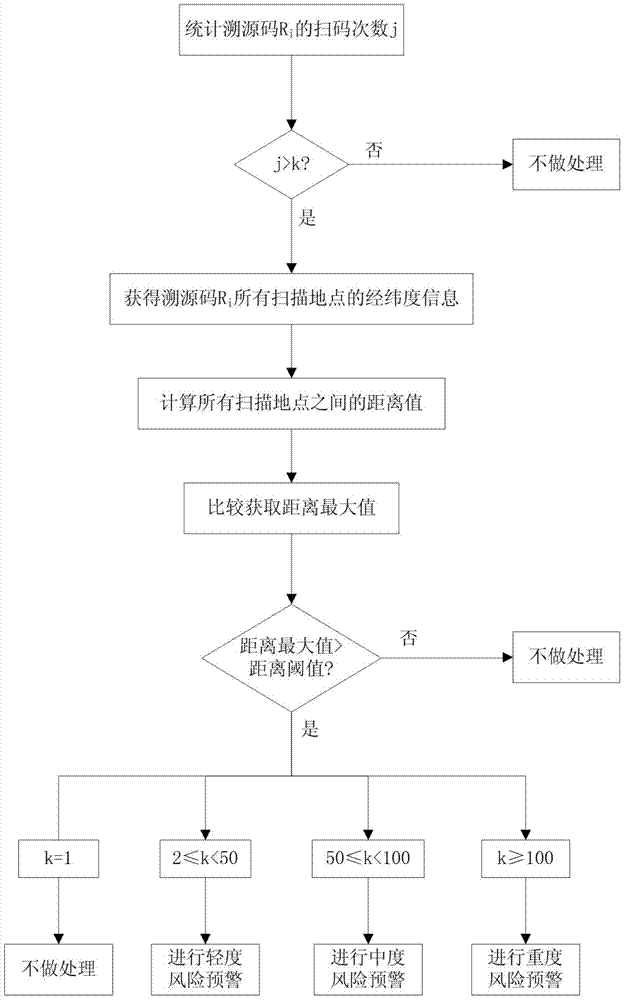
[0046] In this embodiment, a method for generating a QR code is as follows:
[0047] Step 1. Define variable i and initialize i=1;
[0048] Step 2. Batch generate traceable source code;
[0049] Step 2.1, use formula (1) to obtain the interval length R of the traceability source code l ;
[0050] R l = l n , 0 R l R max R max , R l ≥ R max - - - ( 1 )
[0051] In formula (1), l represents the length of the source code; n represents the number of generated source code, R max Represents the maximum value of the random function Rand();
[0052] Assuming that the length of the traceability source code is l=9, the traceability source code is generated from 000000000 to 99999999, which can generate up to 1000000000 traceability source codes; assuming that the product needs to generate 100,000 traceability source codes, that is, n=100000, then the formula (1 )Calculate interval length This example is r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com