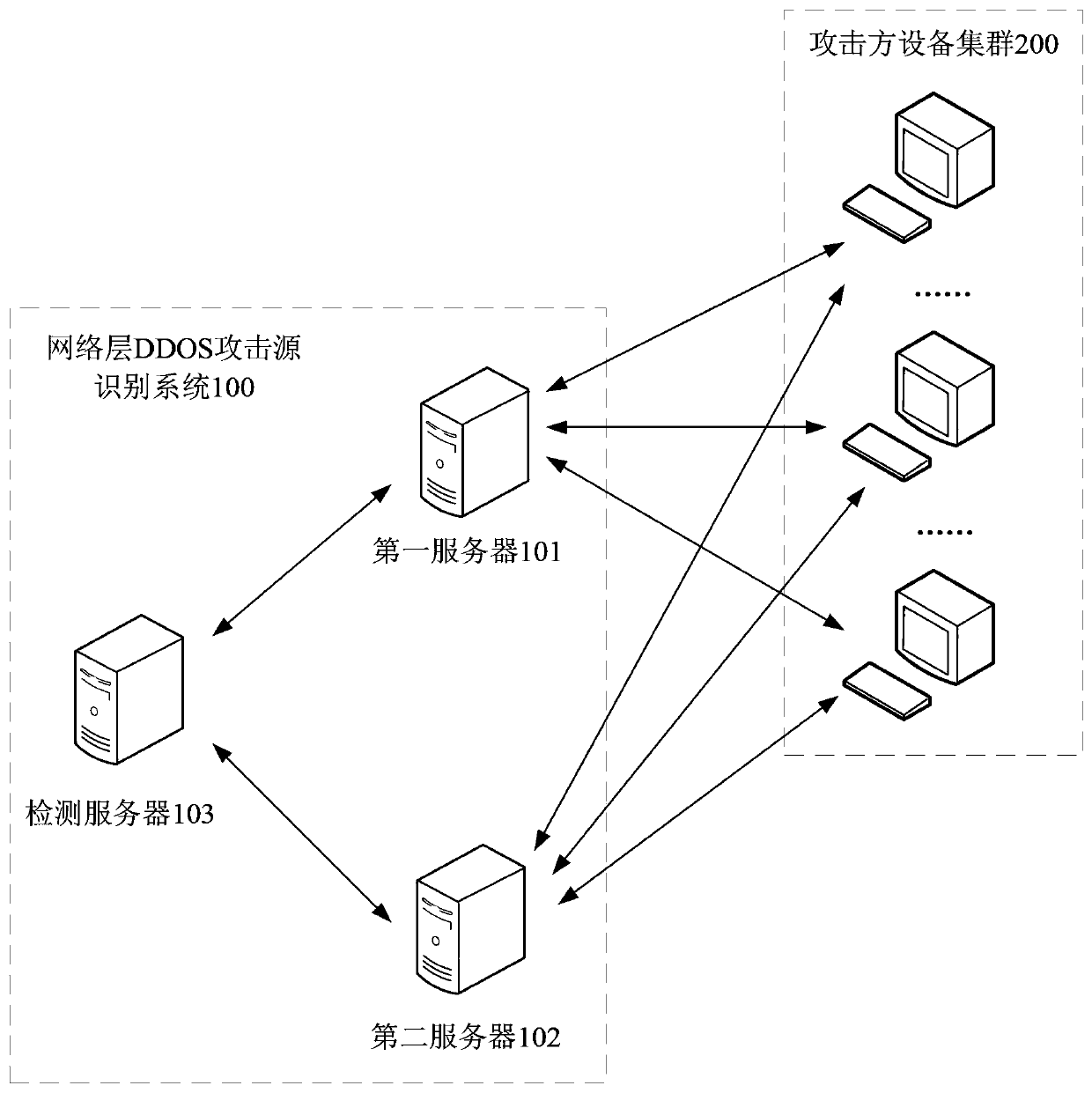
Network layer ddos attack source identification method, device and system
A DDOS and identification method technology, applied in the field of computer communication, can solve the problem that the real attack source of small traffic DDOS attack cannot be effectively traced.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
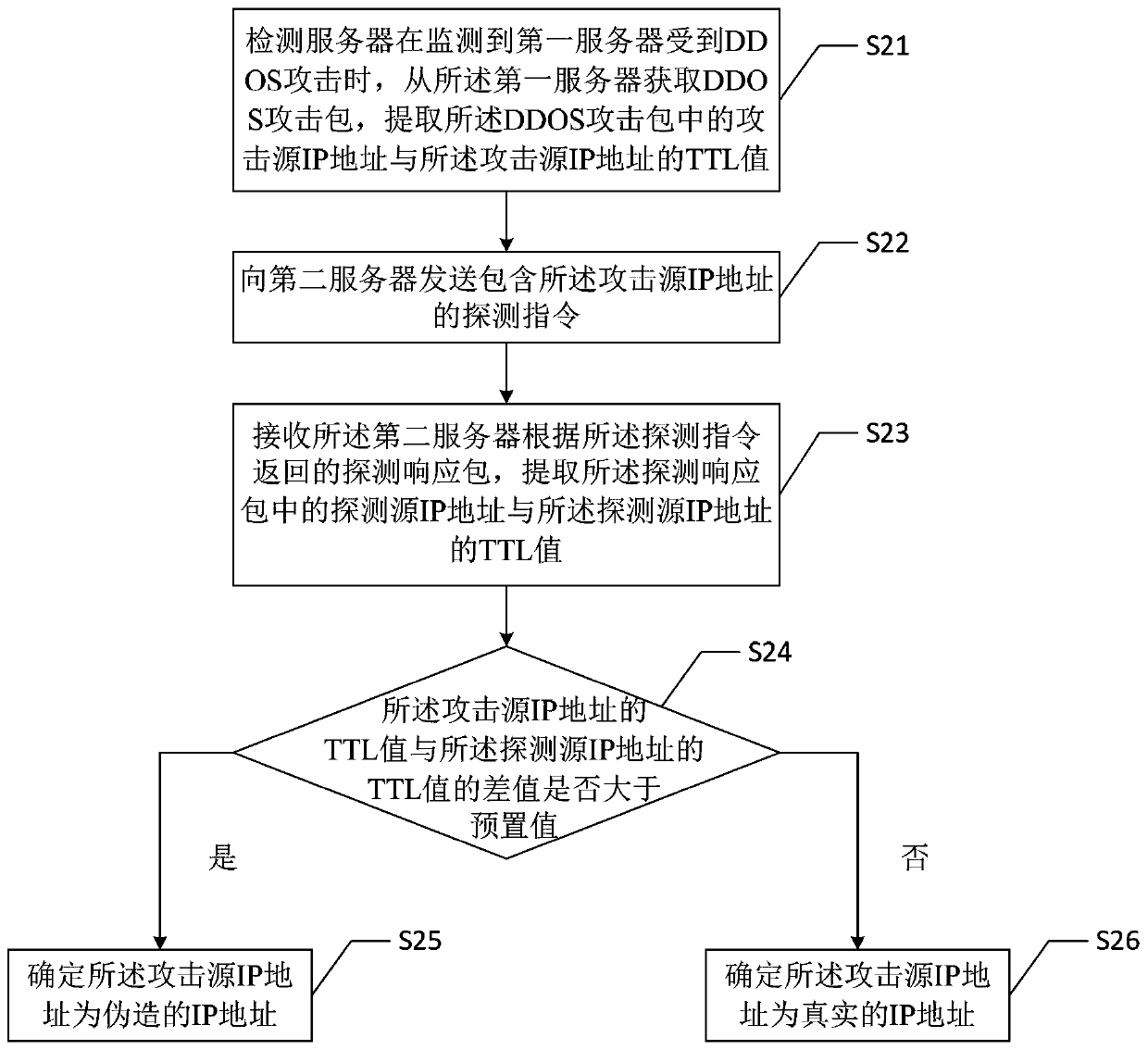
[0022] see figure 2 , which is a flow chart of the method for identifying a source of a network layer DDOS attack provided by the first embodiment of the present invention. Such as figure 2 As shown, this embodiment describes the processing flow of the detection server, combined with figure 1 The network layer DDOS attack source identification method provided by the present embodiment includes the following steps:
[0023] Step 21: When the detection server detects that the first server is attacked by DDOS, it obtains the DDOS attack packet from the first server, and extracts the attack source IP address and the TTL value of the attack source IP address in the DDOS attack packet.
[0024]Specifically, the detection server 103 monitors whether the first server is attacked by a DDOS (Distributed Denial of Service) by monitoring the data flow information of the first server 101 in real time. When it is detected that the first server 101 is attacked by a DDOS, it also That is...
no. 2 example
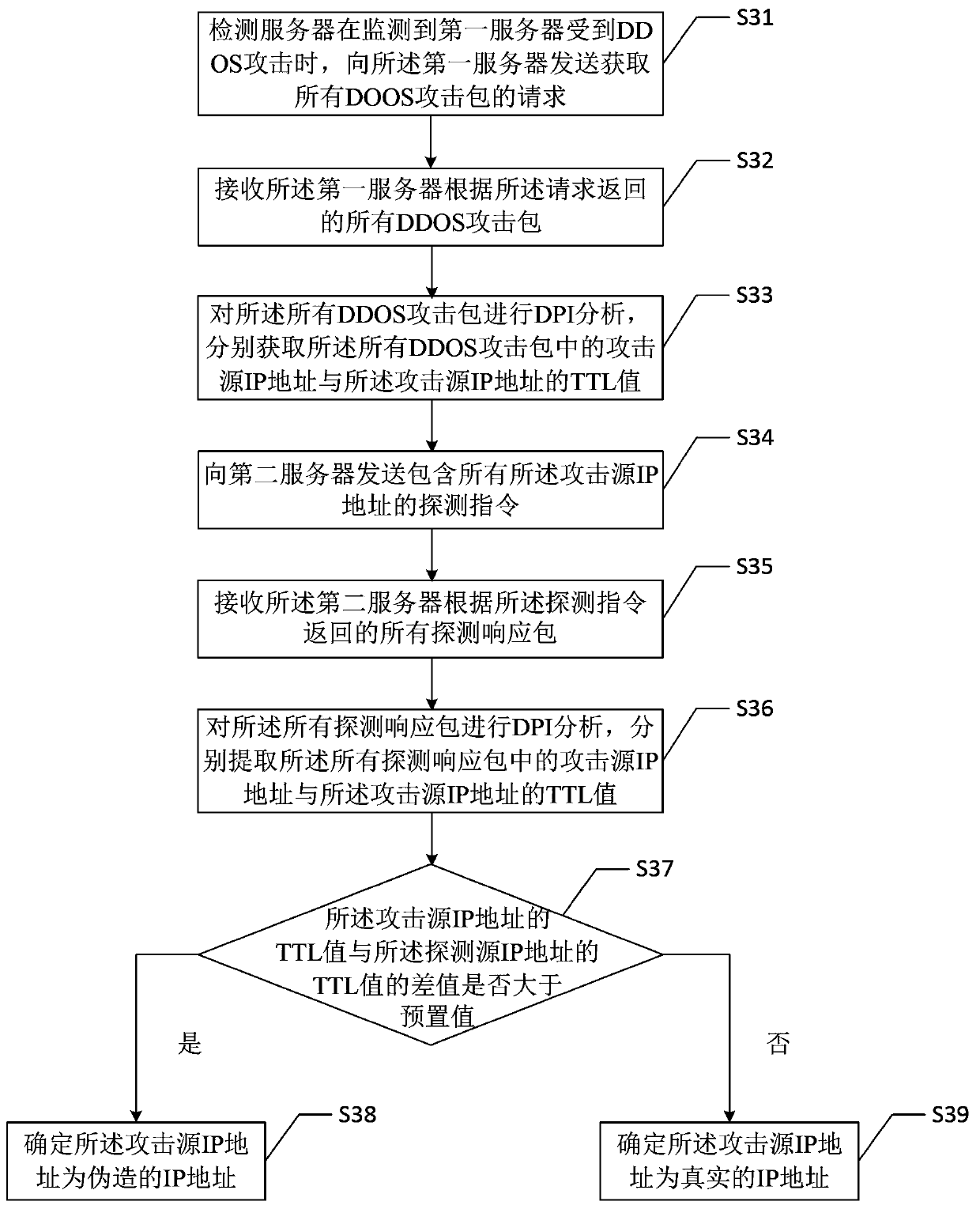
[0039] see image 3 , which is a flowchart of a method for identifying a source of a network layer DDOS attack provided by the second embodiment of the present invention. Such as image 3 As shown, this embodiment describes the processing flow of the first server, combined with figure 1 The network layer DDOS attack source identification method provided by the present embodiment includes the following steps:
[0040] Step 31 , when the detection server detects that the first server is attacked by DDOS, it sends a request for obtaining all DOOS attack packets to the first server.
[0041] For details of step 31, please refer to the corresponding content of the first embodiment, which will not be repeated here.
[0042] Step 32, receiving all DDOS attack packets returned by the first server according to the request.
[0043] Specifically, the first server 101 starts a full packet capture according to the request for obtaining all DOOS attack packets sent by the detection ser...
no. 3 example
[0060] see Figure 4 , is a flowchart of a method for identifying a source of a network layer DDOS attack provided by the third embodiment of the present invention. Such as Figure 4 As shown, this embodiment describes the processing flow of the user terminal, combined with figure 1 The network layer DDOS attack source identification method provided by the present embodiment includes the following steps:
[0061] Step 41 , when the detection server detects that the first server is under DDOS attack, it sends a DDOS attack packet acquisition request to the first server.
[0062]Specifically, the detection server 103 monitors whether the first server is attacked by a DDOS (Distributed Denial of Service) by monitoring the data flow information of the first server 101 in real time. When it is detected that the first server 101 is attacked by a DDOS, it also That is, when the data traffic of the first server 101 is detected to be abnormal, for example, when there is a large flow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com