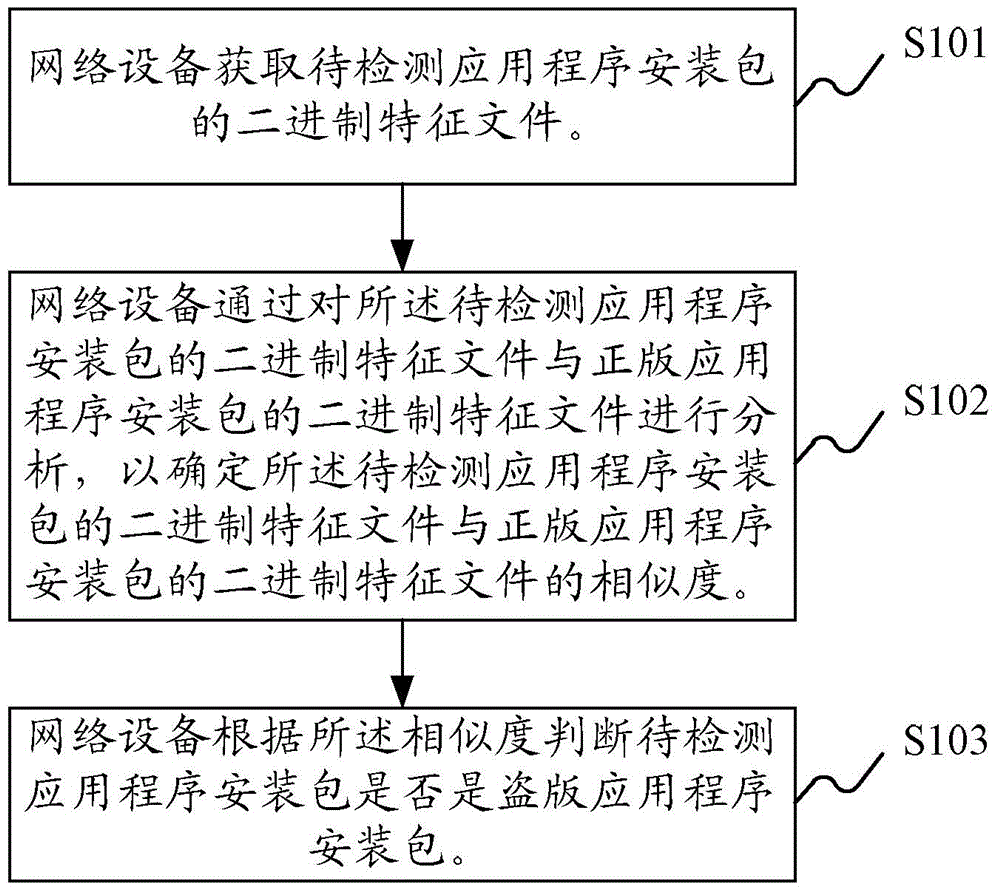
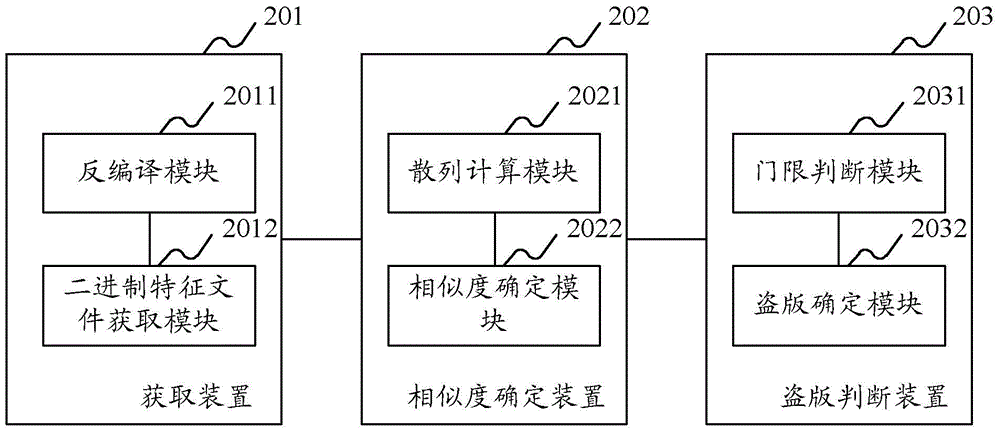
Method and device for detecting pirated application program
A technology of application programs and piracy, which is applied in the computer field and can solve problems such as inability to accurately determine application installation packages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0027] Example 1: Decompile APK using apktool
[0028] Use the command line "apktool d apk file name" in cmd to compile the APK file, where "apktool d" is the decompilation command, and d stands for decode. It should be noted that the execution directory of the command line is the same as the directory where the APK file is located. Subsequently, the decompiled file of the APK can be obtained in the command where the APK file is located.
example 2
[0029] Example 2: Decompile APK using apkdb
[0030] Install the apkdb program. After the apkdb program is installed, select the APK file to be decompiled, right-click the mouse, and select the decompilation option in the menu that appears after right-clicking the mouse. Subsequently, the decompiled file of the APK can be obtained in the command where the APK file is located.
[0031] Specifically, after obtaining the decompiled file of the application installation package to be detected, the network device performs aggregation processing on the decompiled file of the application installation package to be detected, so as to obtain a binary feature file.
[0032] Specifically, the decompiled files of the application installation package to be detected can be aggregated in the following manner to obtain binary signature files:
[0033] First, in step S1011 (not shown in the figure), the network device removes redundant information from the decompiled file of the application in...
example 3
[0039] Two program fragments in the decompiled file of the application installation package to be detected:
[0040] Fragment 1
[0041]
[0042]
[0043] Fragment 2
[0044]
[0045]After removing redundant information, obtain a program fragment that only retains operators:
[0046] Fragment 1
[0047] invoke-direct
[0048] new-instance
[0049] invoke-direct
[0050] Fragment 2
[0051] invoke-virtual
[0052] move-result-object
[0053] check-cast
[0054] iput-object
[0055] Subsequently, splicing is performed according to the lexicographical order of the fragment names of the program fragments to obtain a part of the binary feature file:
[0056] invoke-direct
[0057] new-instance
[0058] invoke-direct
[0059] #
[0060] invoke-virtual
[0061] move-result-object
[0062] check-cast
[0063] iput-object
[0064] In this embodiment, the decompiled file that only retains operators is obtained by removing redundant information such as advertis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com