System and method for achieving safety audit
A security audit and equipment technology, applied in the field of information security, can solve the problems of unable to support the server, difficult to meet the requirements, etc., and achieve the effect of reliable service, convenient expansion and high reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
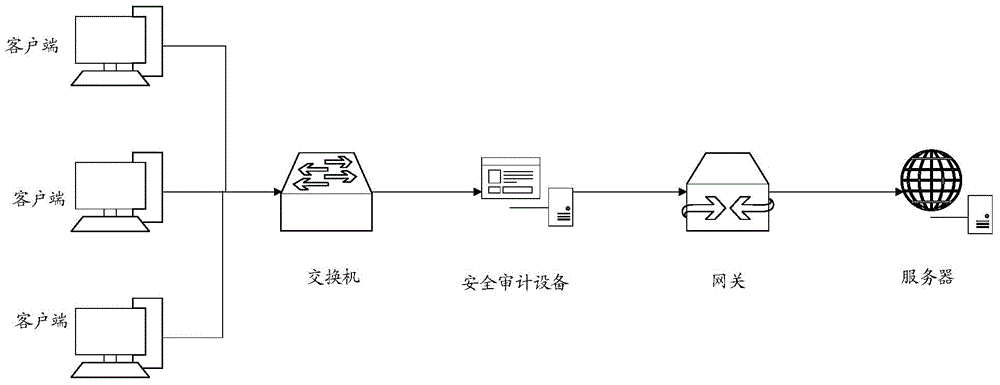
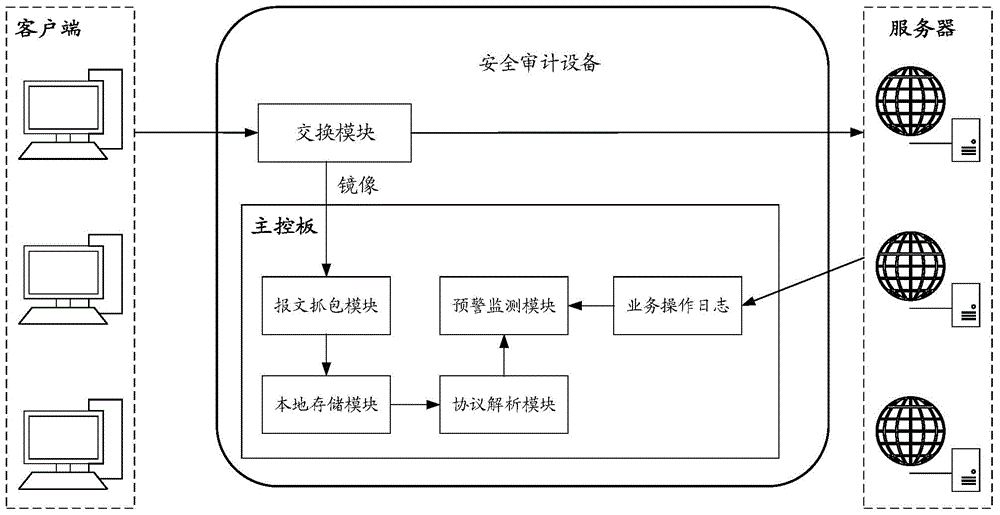
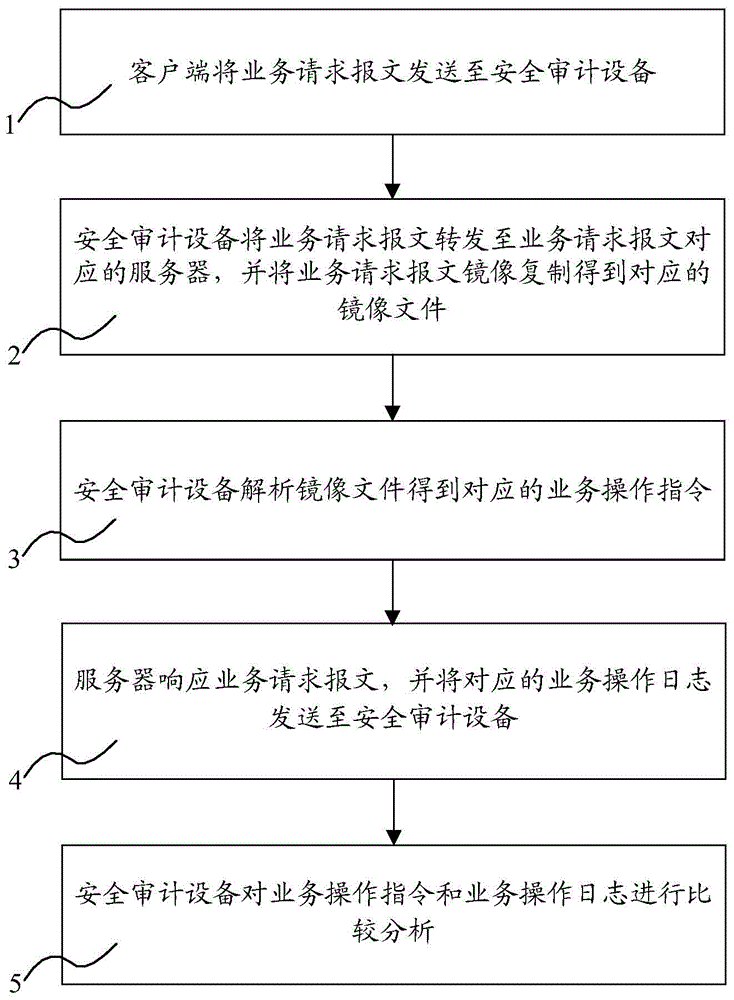
[0045] Through multiple groups of ports of the security audit device, the security audit device can be connected in series between multiple client users and multiple servers providing web services. The security audit device receives the service request message sent by the client to the server and the service operation log generated after the server responds to the user request; all http messages (ie service request messages) for the user to access the web service must pass through the security audit device, Most switches (that is, switching modules) support the mirror (mirror) strategy. The mirror strategy can copy the packets that meet the specified rules on one port to one or more ports, which is convenient to use and has a good effect. Therefore, this security audit device is used in switching Set the mirror policy on the board component, combined with image 3 Shown method, a specific embodiment of the present invention is as follows:
[0046] When a user accesses the ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com