Method for detecting cryptology misuse of Android application programs
A technology for application and misuse detection, applied in program control devices, digital data protection, etc., to solve problems such as inability to process applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
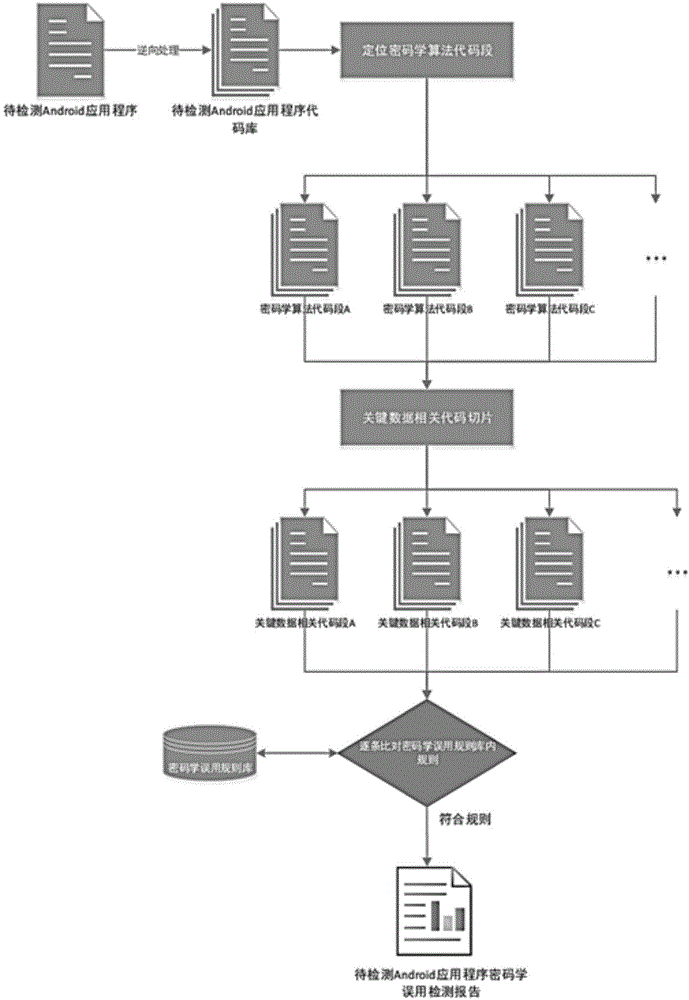
[0040] Such as figure 1 As shown, this embodiment includes the following steps:
[0041] The first step is to conduct a reverse analysis of the application to be detected to obtain the source code. The specific steps include:
[0042] 1.1 Use JEB to reverse process the application to be detected, reversely restore the program code in the compiled Android application apk file to smali code and java code.
[0043] 1.2 The application program processed by JEB includes smali code and java code. The smali code includes all class codes and can be used as a code library. The java code is divided into different files by class.
[0044]The second step is to find the code segment related to the cryptographic algorithm in the reversed smali code. The specific steps include:
[0045] 2.1 Statically scan the smali code reversed by the application to be detected, and find the API that the java cryptography library must use: the dofinal() function. By looking for this function, you can loc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com