Intrusion detection method and device
An intrusion detection and algorithm technology, applied in computer security devices, instruments, electrical and digital data processing, etc., can solve problems such as low accuracy and low detection efficiency, and achieve the effect of improving accuracy and computing speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
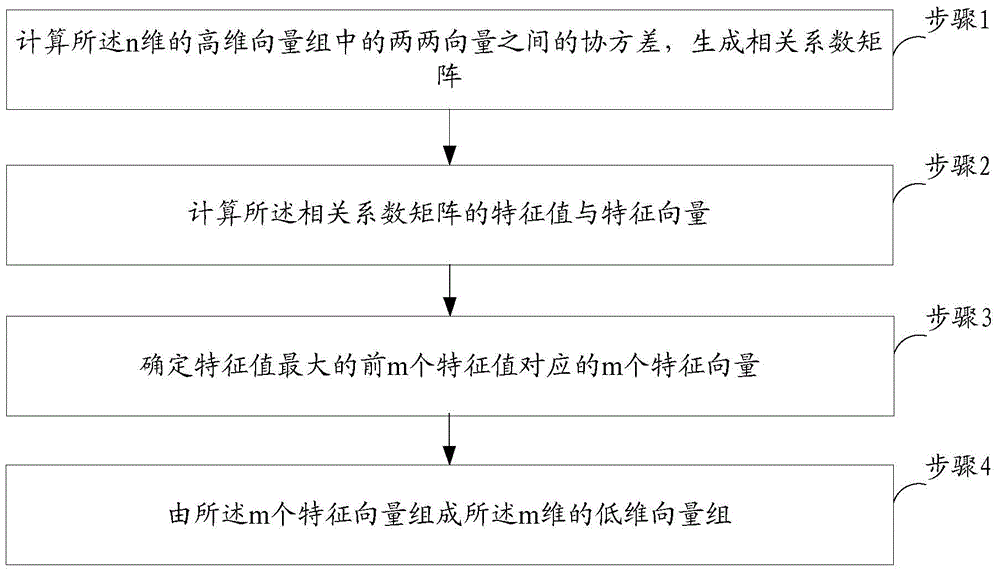
[0044] figure 1 The implementation flow of the intrusion detection method provided by Embodiment 1 of the present invention is shown, and the details are as follows:
[0045] In step S101, data normalization processing is performed on the intrusion detection data set KDD CUP99 to obtain an n-dimensional high-dimensional vector group.
[0046] In the intrusion detection model, the selection of data set is the first step in the research and evaluation of intrusion detection algorithms, and the quality of the data set will directly determine the evaluation results of various intrusion detection algorithms.
[0047] The security audit data set KDD CUP99 organized by Columbia University IDS Laboratory, many papers and research results are based on this data set. The data set is divided into training set and detection set, which contains a large number of network connection records, each connection record contains 41-dimensional features, a total of 39 types of attack records, each...
Embodiment 2
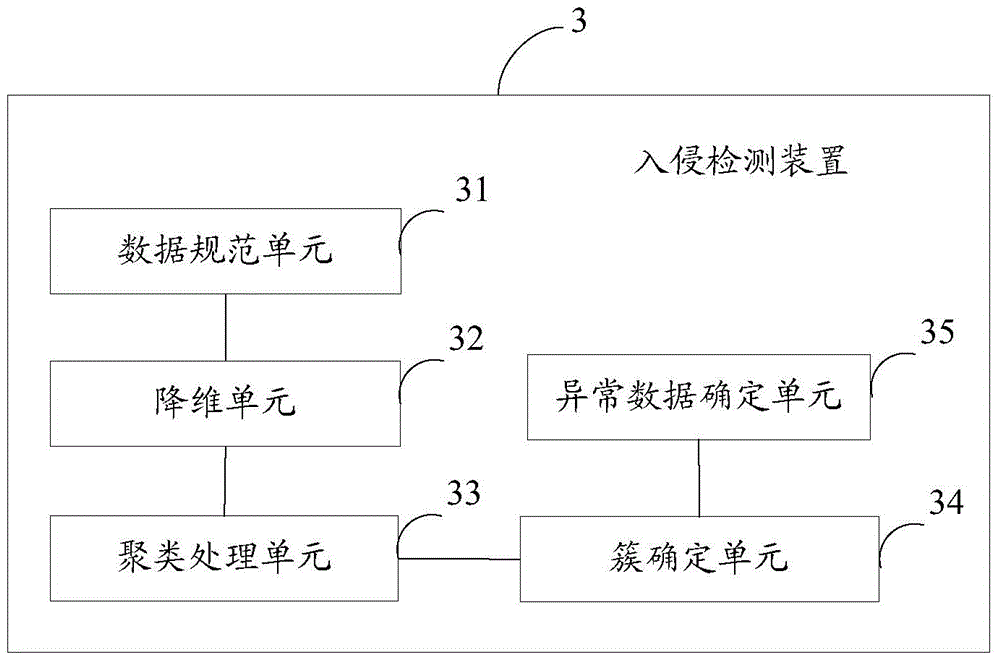
[0088] image 3 A specific structural block diagram of the intrusion detection device provided by Embodiment 2 of the present invention is shown. For convenience of description, only parts related to the embodiment of the present invention are shown. The intrusion detection device 3 includes: a data specification unit 31 , a dimensionality reduction unit 32 , a cluster processing unit 33 , a cluster determination unit 34 and an abnormal data determination unit 35 .
[0089] Wherein, the data normalization unit 31 is used to perform data normalization processing on the intrusion detection data set KDD CUP99 to obtain an n-dimensional high-dimensional vector group;
[0090] A dimensionality reduction unit 32, configured to perform dimensionality reduction processing on the n-dimensional high-dimensional vector group to obtain an m-dimensional low-dimensional vector group, wherein m is less than n;
[0091] A clustering processing unit 33, configured to process the m-dimensional...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com