Moving target protection method based on operating system fingerprint jumping
An operating system and moving target technology, which is applied in the field of moving target protection based on operating system fingerprint jumps, can solve the problems of limited protection capability, high transformation cost, and complicated implementation, so as to improve protection capability, increase complexity, and avoid transformation. cost effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
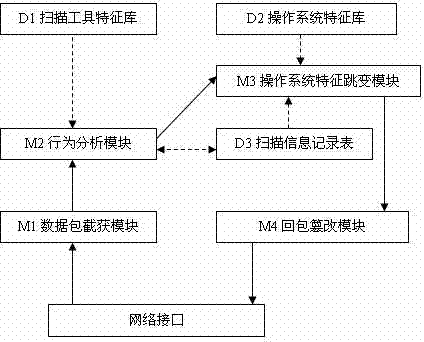
[0026] see figure 1 , a mobile target protection method based on operating system fingerprint jumps. This method is designed to defend against the scanning tools commonly used by attackers, and uses the operating system feature libraries of these scanning tools to perform targeted fingerprint jumps to realize attack scanning behavior. The identification and fingerprint feature camouflage, so that the attacker cannot obtain the specific information of the operating system to be attacked, and then cannot carry out the next attack behavior to achieve network protection.
[0027] The method adopts the isolation method of internal and external networks to protect the terminals inside the network, including the sequentially connected network interface, data packet interception module, behavior analysis module, operating system feature jump module and response data packet tampering module, which are connected with the behavior analysis module The feature library of the scanning tool,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com