Unlocking method, device and terminal
A technology for unlocking devices and terminals, applied in computer security devices, reducing energy consumption, telephone communication, etc., to achieve the effects of increasing convenience and intelligence, reducing the probability of being unlocked by mistake, and reducing the probability of misoperation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
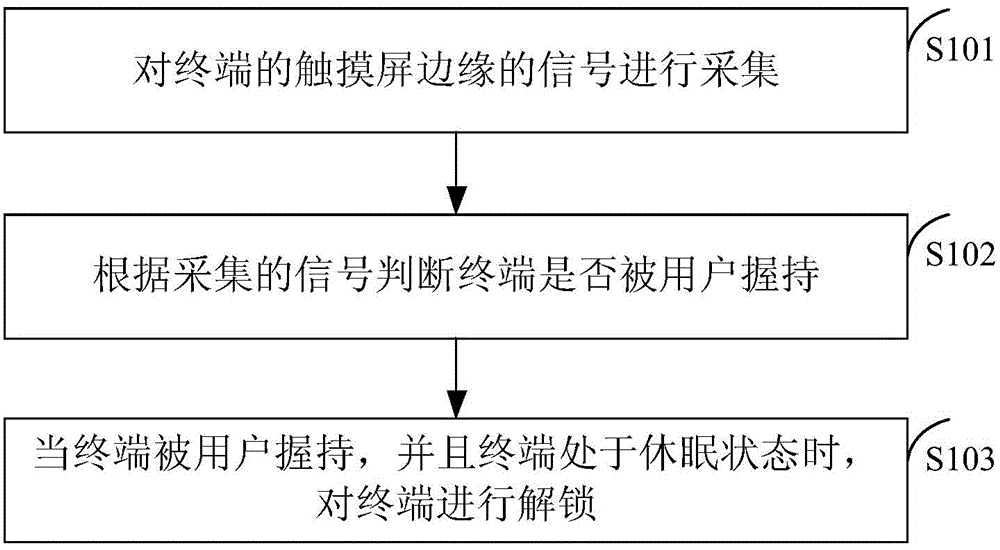
[0073] Figure 4 It is a flow chart of an unlocking method according to an exemplary embodiment 1. like Figure 4 As shown, the above unlocking method is applicable to a terminal, for example, in a mobile phone or a tablet computer, when the user holds the terminal with his left hand to unlock, the method includes the following steps:
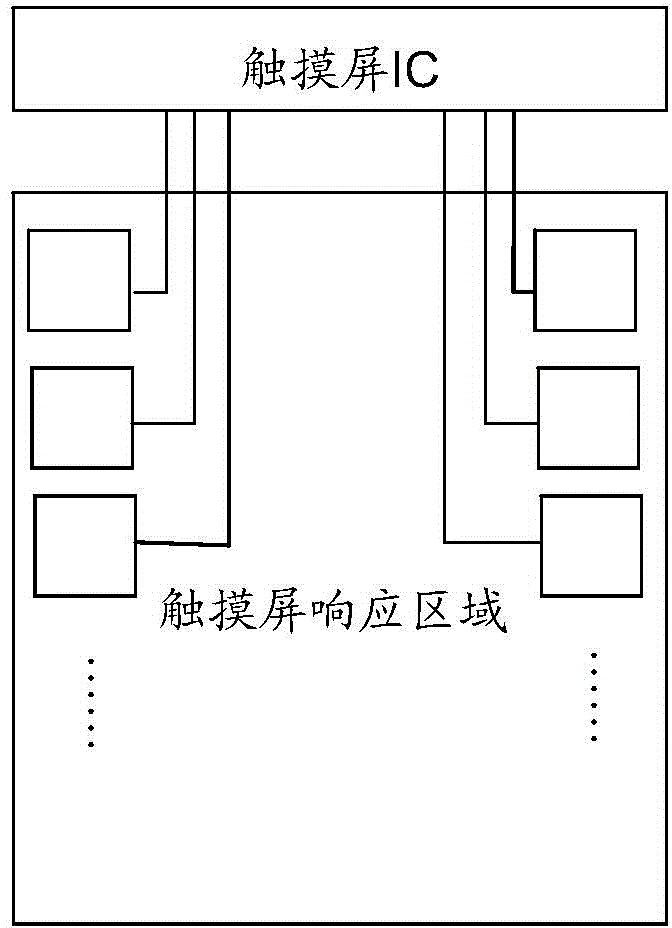
[0074] In step S401, the signal at the edge of the touch screen of the terminal is collected.
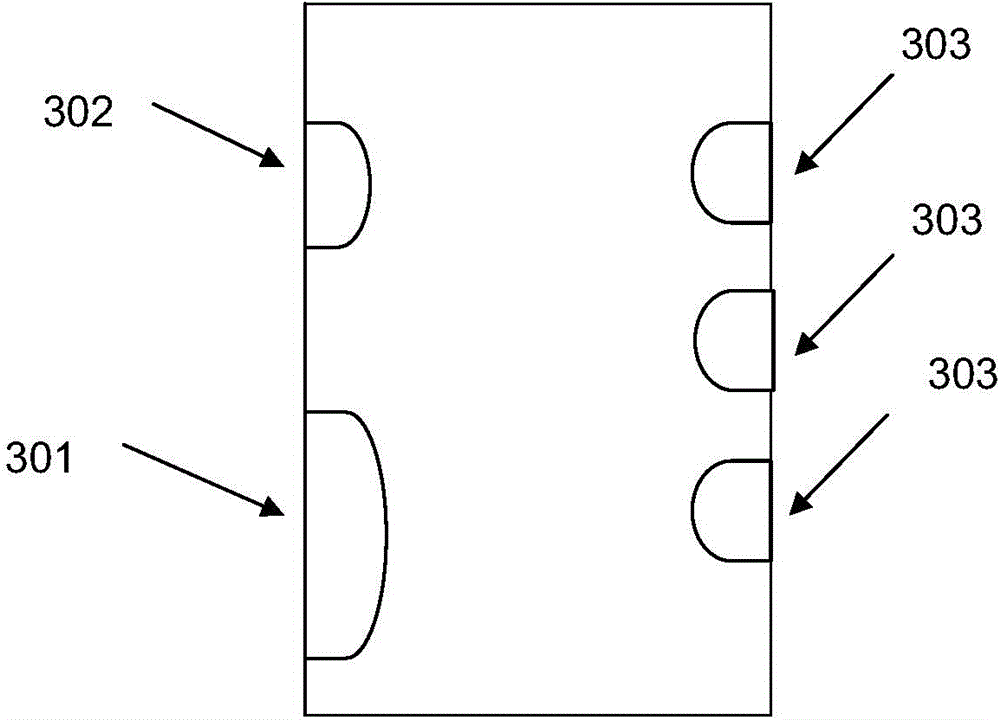
[0075] In step S402, when the first signal and the second signal are collected on the left edge of the touch screen of the terminal, and at least one third signal is collected on the right edge of the touch screen of the terminal, it is determined that the terminal is held by the user's left hand.
[0076] Wherein, the first signal is greater than the second signal, and the first signal is greater than the third signal.
[0077] In step S403, when the terminal is held by the user's left hand and the terminal is in a dormant state, an interrupt is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com