Secure two-party computation method and system based on symbol boundary value binary decision diagram
A technology for secure two-party computation and binary decision graph, applied in the field of information security, can solve problems such as state space explosion, function scale expansion, etc., to achieve the effect of improving computing efficiency and providing controllability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
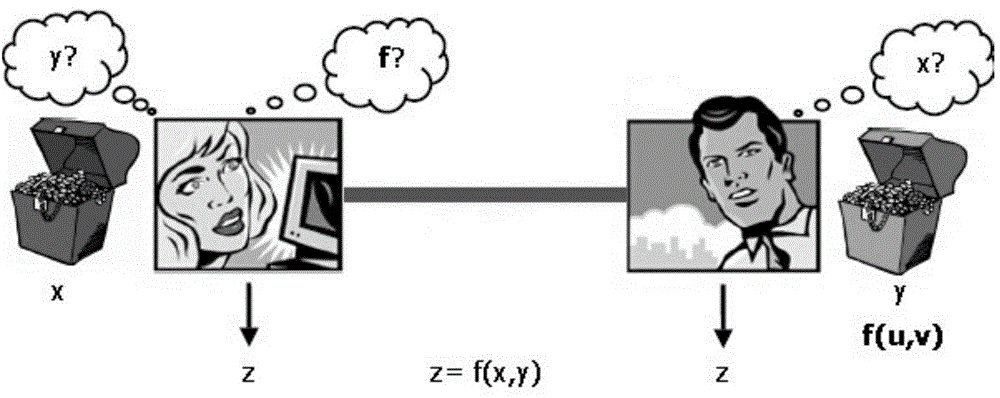
[0087] When input: represents the joint function f(x 1 ,x 2 ,...,x n ) of EVBDD(f), where the variable order is x 1 2 n . In addition, the server's input x a =(x 1 ,x 2 ,...,x k ) corresponds to the first k variables in EVBDD(f), the input x of the client b Corresponding to the last n-k variables. Expected output: C=f(x a ,x b ).
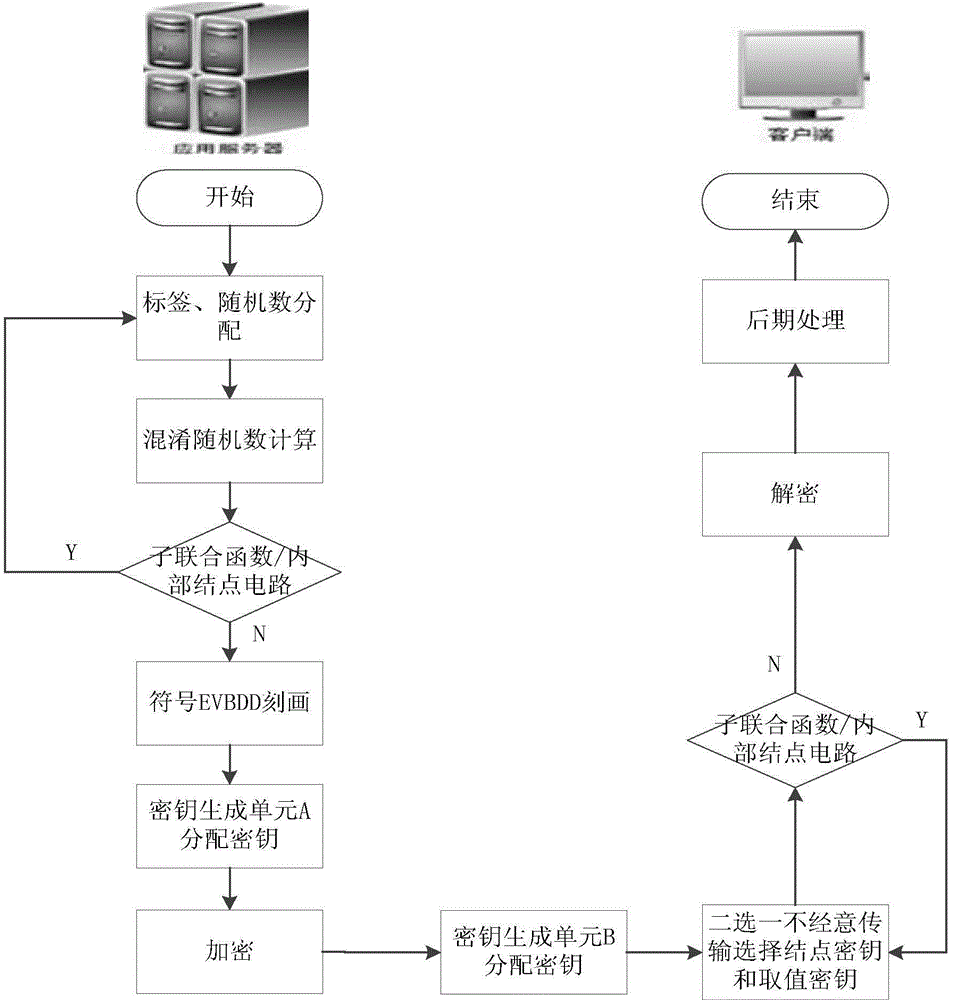
[0088] figure 1 An example model for this embodiment. figure 2 It is the embodiment flowchart of this embodiment. refer to figure 2 , a kind of safe two-party computing method based on symbol EVBDD that the present invention proposes, comprises following three phases, and namely phase I (offline) server builds and confuses joint function; Phase II (online) information interaction between server and client; Phase III The client's decryption calculation. The specific steps of each stage above are:
[0089] Phase I (offline) server builds obfuscated joint functions, including:
[0090] Step 1, the server randomly generates a label l...
Embodiment 2
[0179] This embodiment provides And-N: bitwise AND operation of two integers, the server and the client each hold an input of an N-bits integer, and the output is an N-bits integer.
[0180] Step 1. The server confuses the joint function and assigns labels, node keys and value keys.
[0181] Step 2, client-server information interaction, obfuscation of input data and acquisition of key tags required for decryption.
[0182] Step 3, the client decrypts the calculation and obtains the final result.
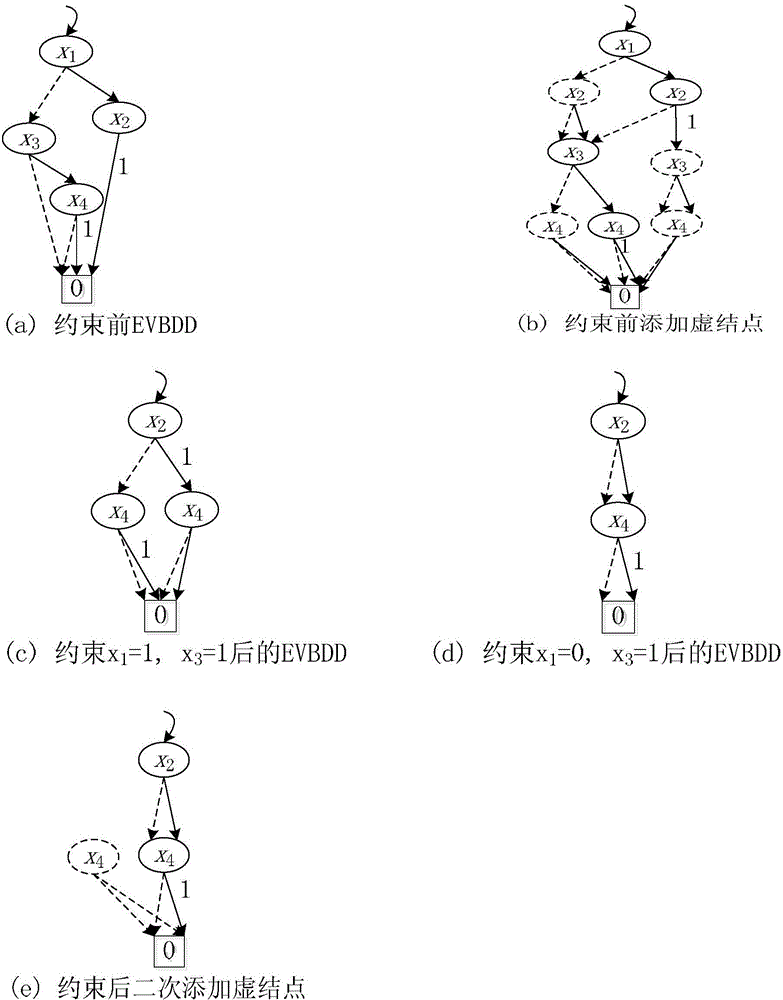
[0183] With the increase of elements in the finite field, the number of leaf nodes of the joint function will change in different representations. For this reason, we set N=4, 8, 16, and made horizontal and vertical comparisons in the two functions respectively.
[0184] Figure 4 It is the complexity analysis before encryption of the And-N joint function in this embodiment. The analysis shows that when the number of elements in the finite field is large, the size of the joint f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com