Trojan virus analysis technique based on network conversation
A technology of network conversation and analysis technology, applied in the field of computer applications, which can solve the problem of being powerless to detect unknown malicious codes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0031] In order to better understand the technical solution of the present invention, now in conjunction with the diagram in the accompanying drawing, the specific implementation is further described in detail as follows:
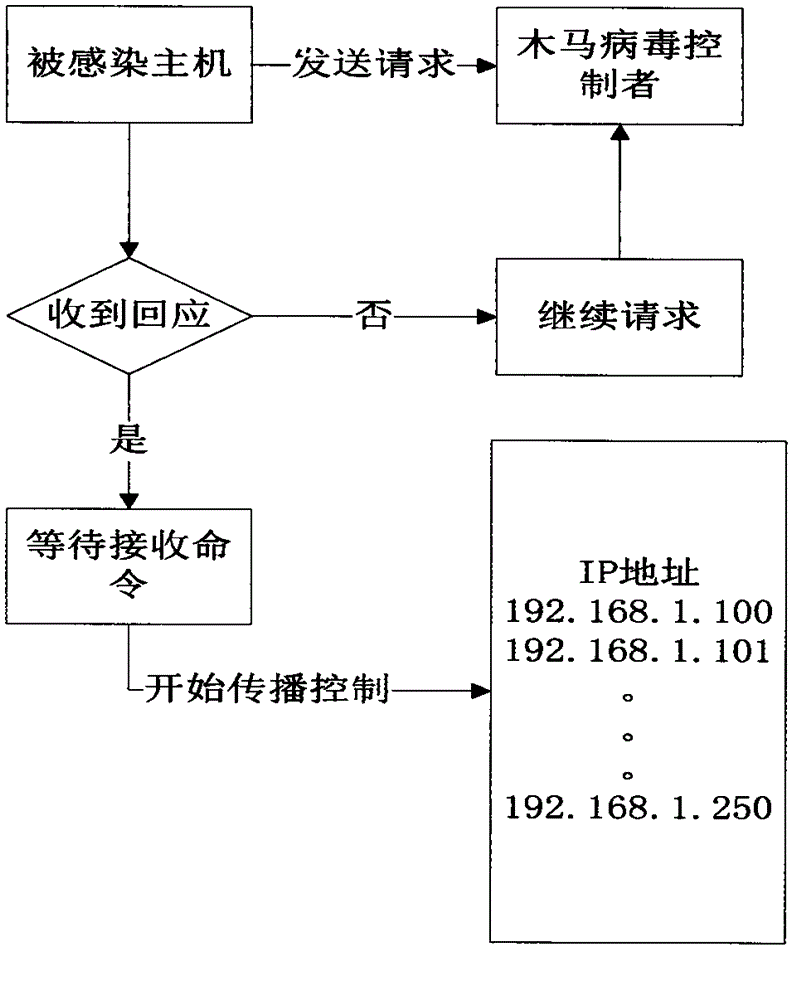
[0032] (1) Behavioral characteristics of Trojan horse virus - (such as figure 1 shown)
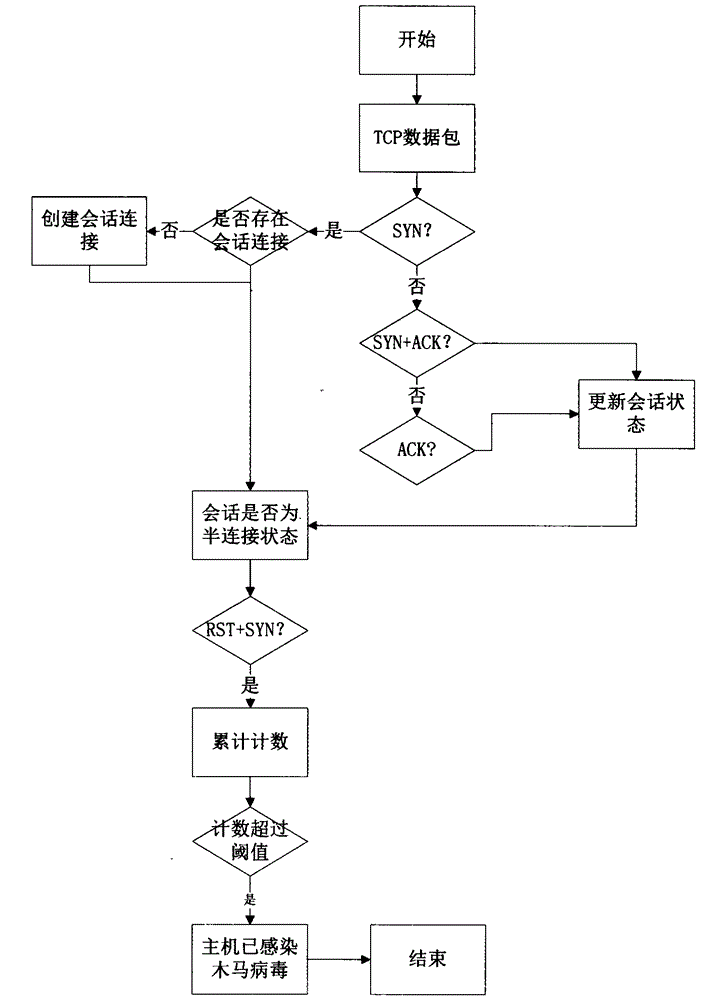
[0033] Because the host infected with the Trojan horse needs to receive the control command of the Trojan horse creator, the Trojan horse host will periodically send a reverse connection request to the control terminal, and the Trojan horse control terminal will not always be online, so this regular reverse connection will lead to network failure. Abnormal connection, by analyzing abnormal connection traffic, the Trojan horse host can be located; once the Trojan horse host is connected to the controller host, the controller will be able to further infiltrate into other hosts or perform other actions through the Trojan horse;
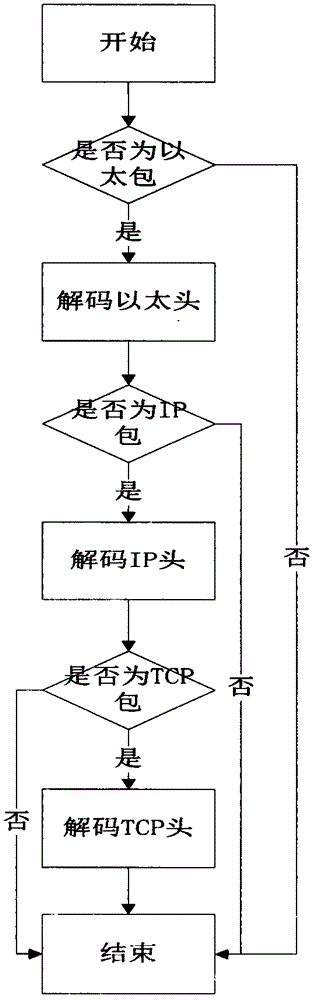
[0034] (2) Packet decoding——(such as fig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com