Safety exchange method for MMS specification application layer
An interaction method and application layer technology, applied in the field of power information communication security, can solve the problems of not paying attention to safety, no protection measures in substations, and only focusing on IED shared communication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
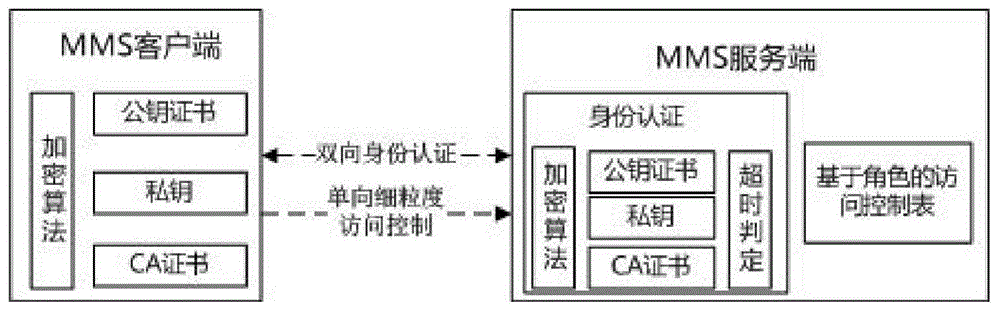
[0022] An interactive method for MMS application layer security reinforcement, by extending the MMS protocol, adding identity authentication and access control technology in the MMS application layer, so that unauthorized users cannot associate with the MMS server and corresponding MMS services.
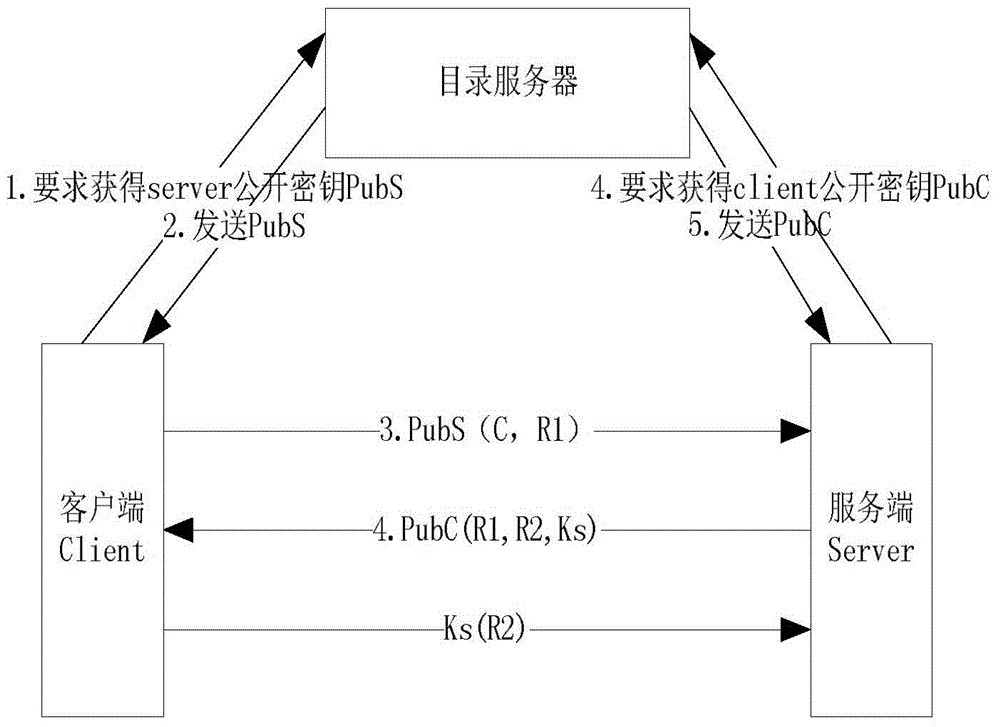
[0023] Such as figure 1 As shown, this method occurs between the MMS client and the MMS server, and the specific steps are as follows:
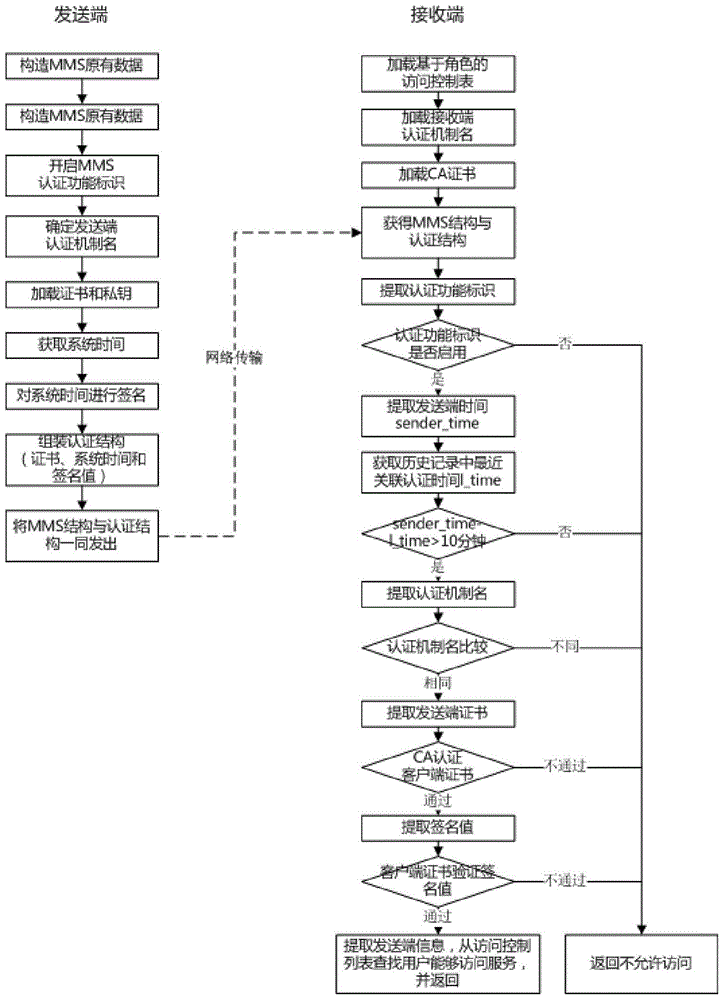
[0024] Step 1: Enable the authentication function and expand the authentication data structure.
[0025] Such as figure 2 As shown, enable the association authentication function unit of ACSE (Association Control Service Element, association authentication service unit) on the MMS application layer, and expand the authentication data structure, as follows,
[0026]
[0027] The extended authentication data structure includes the certificate C, the current system time T and the signature value SV of the time using the private key.
[0028] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com