A virtualization accessing method and apparatus
An access device and virtualization technology, applied in the field of virtualized access, can solve the problems of complex network deployment and difficult business development, and achieve the goal of reducing the configuration process, reducing the complexity of network deployment, and reducing network maintenance costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
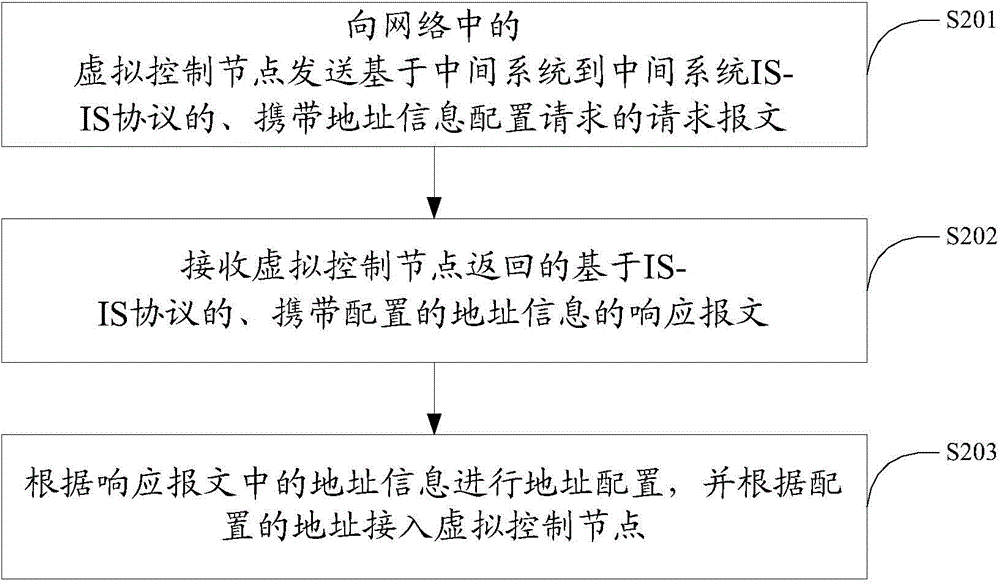
[0056] like figure 2 Shown is a virtualized access method in the embodiment of the present invention, the execution subject of the method is an access device, and the method includes:
[0057] S201, sending a request message carrying an address information configuration request based on the intermediate system to intermediate system IS-IS protocol to the virtual control node;
[0058] The current IS-IS protocol mainly includes the following message types:
[0059] Inquiry (IS-IS Hello Packets, IIH for short) message, IIH message is mainly used to establish and maintain the adjacency relationship of the access device.
[0060] Link State Packets (LSP for short) messages, LSP messages are mainly used to exchange link state information between access devices.
[0061] Complete Sequence Number packets (CSNP for short) message. The CSNP message is mainly used to confirm the latest received LSP between neighbors.
[0062] Partial Sequence Number Packets (PSNP for short) message,...
Embodiment 2
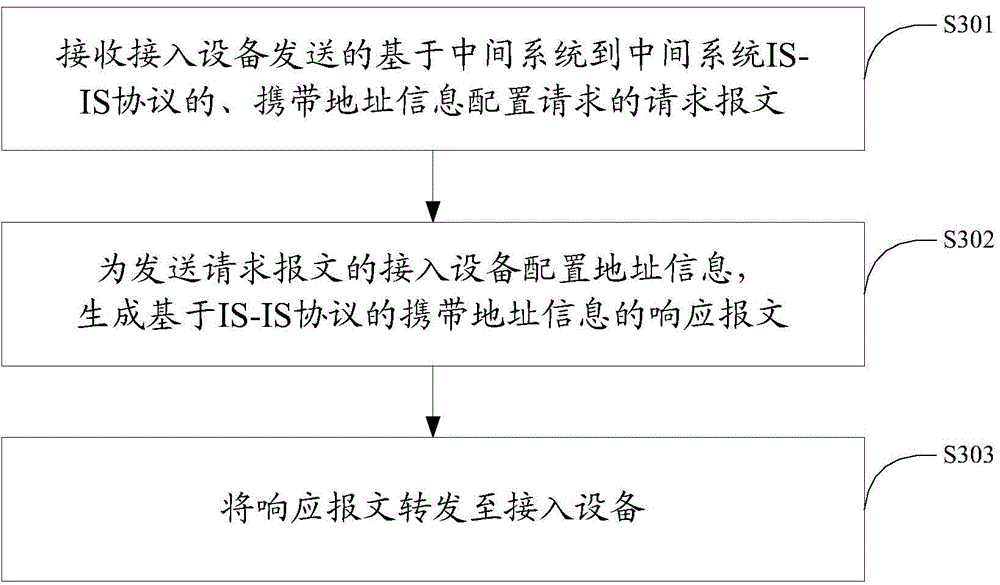
[0082] The embodiment of the present invention also provides a method for virtualized access, the execution subject of the method is a virtual control node in a virtual cluster in the network, such as image 3 Shown is a flow chart of a method for device virtualization access in an embodiment of the present invention, and the method includes:
[0083] S301. Receive a request packet based on the intermediate system to intermediate system IS-IS protocol and carrying an address information configuration request sent by the access device;
[0084] First of all, when networking, a central device or a virtual control node formed by multiple devices is selected in the network. When the virtual control node receives a request message of the IS-IS protocol, the virtual control node will analyze the request message, the virtual control node will read whether there is an address information configuration request in the TLV field of the request message, and if the request message carries ...
Embodiment 3
[0096] Corresponding to the method for virtualized access in Embodiment 1 of the present invention, this embodiment of the present invention also provides a device for virtualized access, such as Figure 4 Shown is a schematic structural diagram of a device for virtualized access in an embodiment of the present invention, and the device includes:
[0097] A sending module 401, configured to send a request message carrying an address information configuration request based on the intermediate system to intermediate system IS-IS protocol to a virtual control node in the network;
[0098] The receiving module 402 is configured to receive a response message based on the IS-IS protocol and carrying configured address information returned by the virtual control node;
[0099] The configuration module 403 is configured to perform address configuration according to the address information in the response message, and access the virtual control node according to the configured address....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com