Automatic detection method of buffer overflow vulnerabilities based on symbolic execution path pruning
A buffer overflow and symbolic execution technology, applied in the field of automatic detection of buffer overflow vulnerabilities, can solve the problems of manual inspection, time-consuming and energy-consuming, and achieve the effect of suppressing state explosion and saving time and energy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
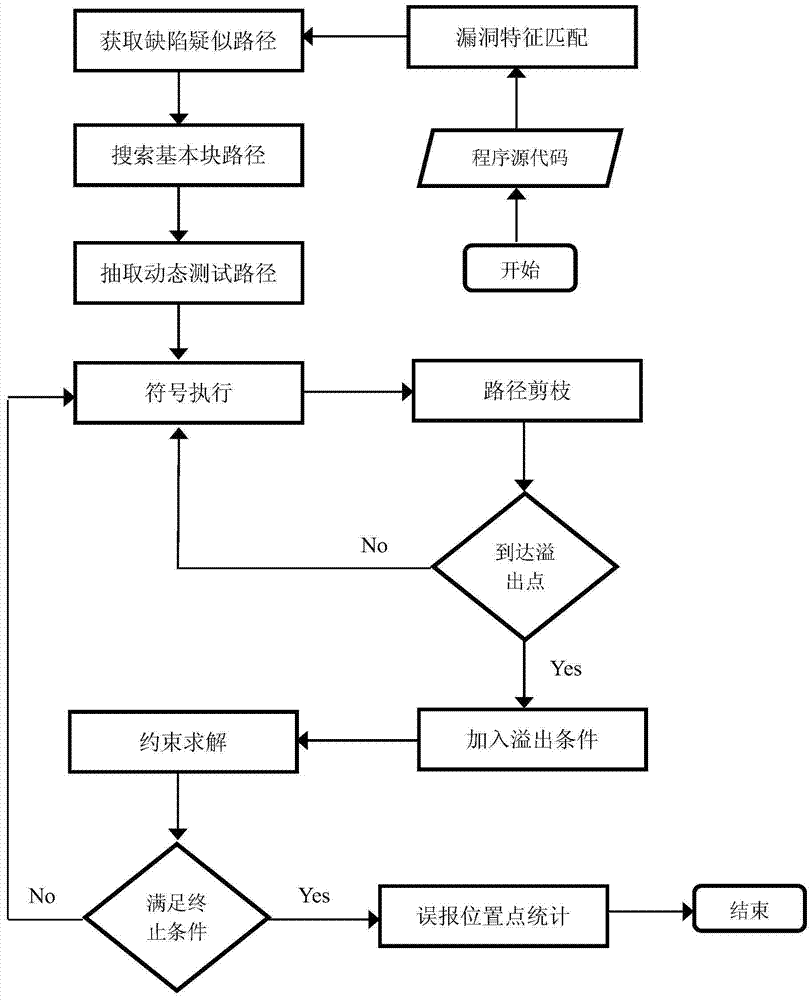
[0045] The specific implementation process can use the existing buffer overflow static analysis tools, control flow graph generation tools and symbolic execution tools. The following sections describe in more detail the details of the implementation process.
[0046] 1. Obtain a complete static analysis path that can be used to guide symbolic execution
[0047] In specific implementation, the static buffer overflow vulnerability path obtained through feature matching needs to be mapped to the control flow graph for further static analysis before it can be used in subsequent steps.
[0048] 1. Construct a control flow graph for the program or system to be tested. The so-called control flow graph is a directed graph. Each node in the control flow graph represents a basic block, and each statement in the program corresponds to a node in the graph. Control flow does not jump or halt until it leaves a basic block.
[0049] 2. Reverse the control flow graph, that is, the nodes in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com