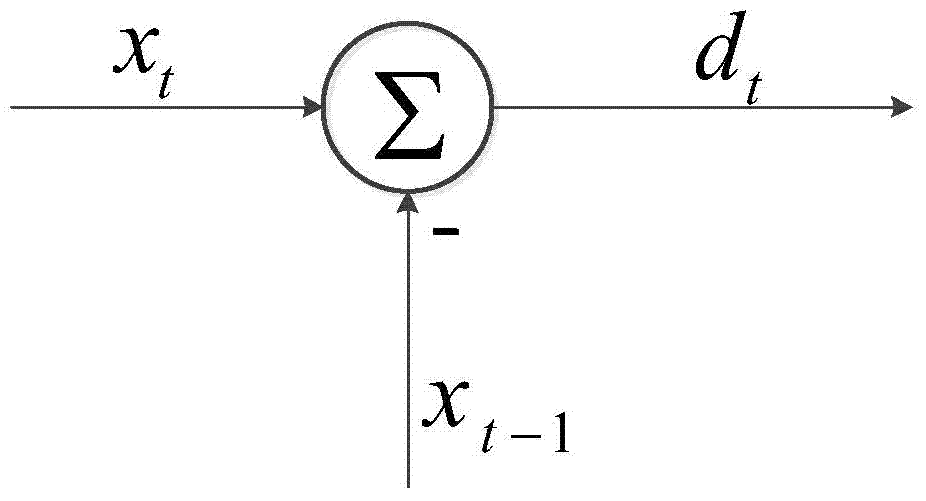Efficient multistage anomaly flow detection method based on TCP
A technology of abnormal flow and detection method, which is applied in the direction of digital transmission system, electrical components, transmission system, etc., and can solve the problems of inaccurate detection results, high false alarm rate, and large limitations in the use of detection methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the drawings in the embodiments of the present invention. Apparently, the described embodiment is only one embodiment of the present invention, not all of them.
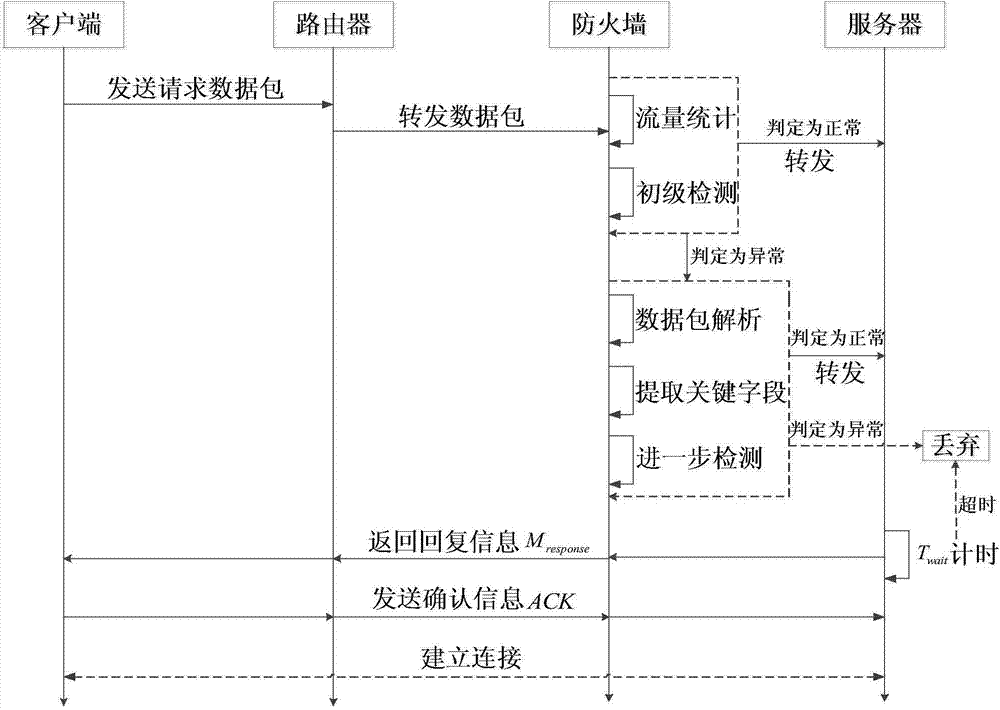
[0027] figure 1 It is a schematic diagram of the multi-level anomaly detection process of the present invention. The present invention is proposed based on the TCP three-way handshake connection protocol of Internet communication. During the communication process, the client makes a request, requests access to the server, and establishes a connection. When the access is normal, the access process is as follows:
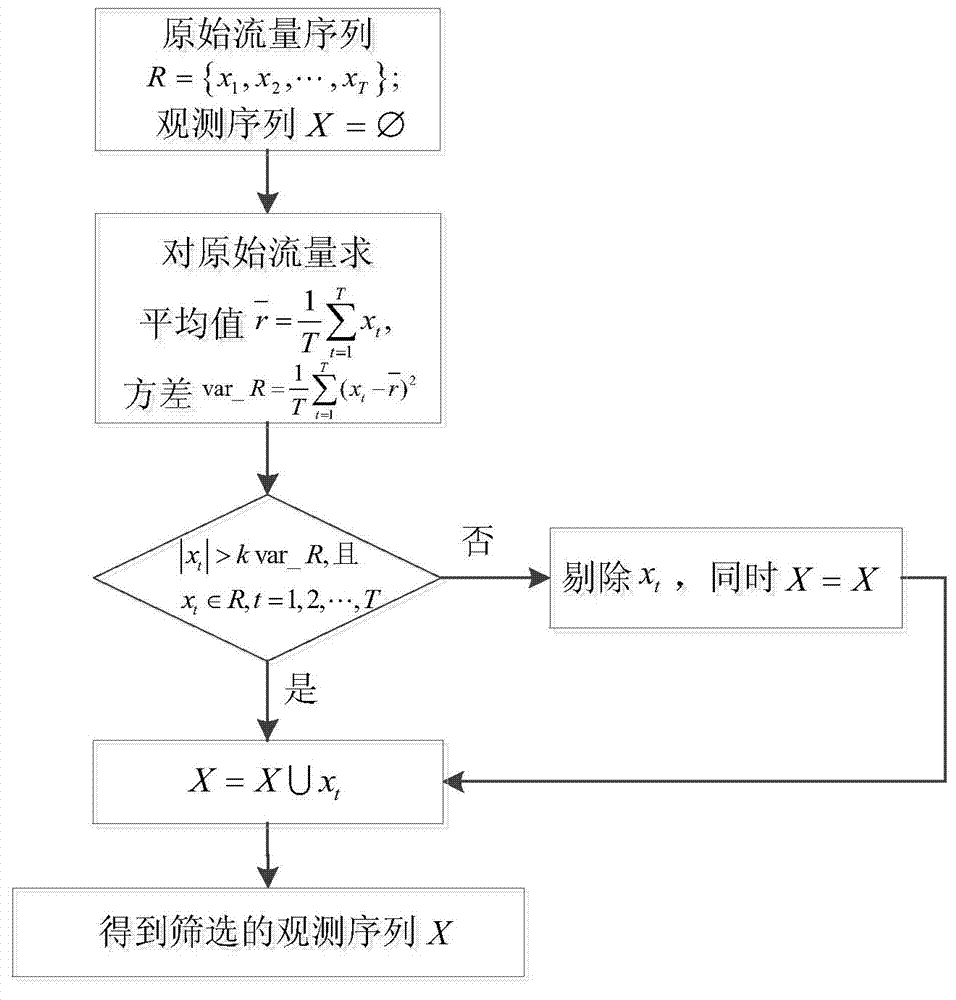
[0028] S1: The client initiates a request, and the sent request packet is forwarded to the firewall through the router. After receiving the request packet, the firewall collects statistics on the traffic and performs primary detection, that is, differential traffic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com