Method for separating known protocol multi-communication-parties data stream into point-to-point data stream
A data flow and multi-communication technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of monitoring and detection of channels that cannot steal secrets, and achieve good results and simple principles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0081] Embodiment 1 realizes for the concrete algorithm of the present invention:
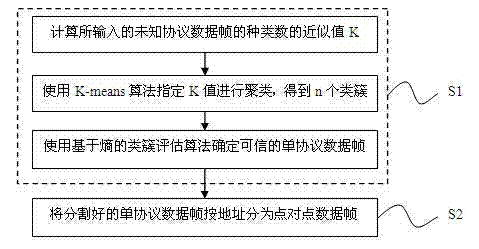
[0082] For step S11,
[0083] Data input: a mixed unknown protocol data frame with n rows and m columns.
[0084] Algorithm goal: Calculate the number k of types of protocols as accurately as possible.
[0085] Its specific algorithm implementation:
[0086] (1) Define the smallest processing unit object: OneByte, the attributes are:
[0087]
[0088] (2) Create a two-dimensional array of n rows and m columns of OneByte, assign the content of each byte of the input data frame to the oneByte field of the OneByte object, and record the row and column where the byte is located.
[0089] (3) Loop through the OneByte two-dimensional array, count by column, and count the number of occurrences of each byte in each column and which rows have this byte. Record the number of occurrences, record it as num, and add the rows that have appeared to the alist collection of OneByte, so that you can get t...
Embodiment 2
[0121] Embodiment 2 is concrete experimental verification:
[0122] For step S11, the calculation experiment of the number of protocol types:
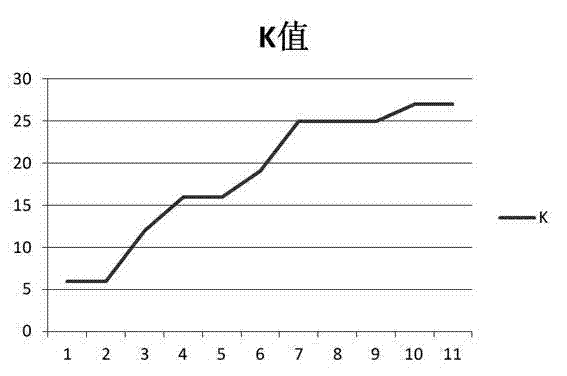
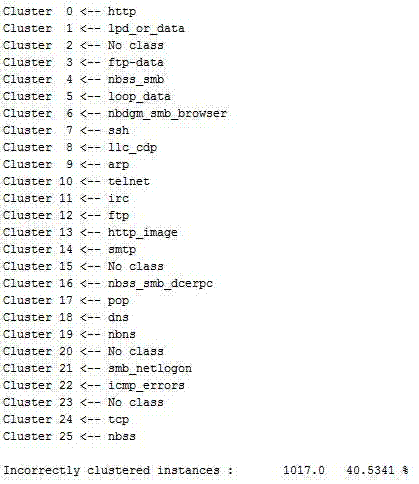
[0123] (1) Data input: 27 kinds of protocols in Tcpdump, each takes 100 data frames, all of which are less than 100; take the first 68 bytes of each data frame; mix the obtained protocols as input.
[0124] (2) Values of variable that can be set: liminal, low_liminal, uniterate. Liminal is set to 95, low_liminal is set to 10; the minimum value of uniterate is 50, and the maximum value is 99;
[0125] Experimental results:
[0126] The experiment uniterate takes the corresponding K value from 50 to 99 records, the following is the brief experiment result of liminal=95; low_liminal=10; uniterate=99 (one experiment):
[0127] The maximum frame length is: 68;
[0128] Total number of frames: 2509;
[0129] Number of column stats: 68;
[0130] The number of sets in the candidate result set: 62;
[0131] The number of collections in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com